 It’s not clear whether the past year will go down in history as a particularly bad year for malware, but one thing is certain: It was bad enough, at times, that fighting infections and cleaning PCs took priority over virtually all other work. Neither home users nor businesses were immune from wave after wave of increasingly nasty malware tricks, though there were a few bright spots: A fix issued by Microsoft mid-year meant that worms are far less likely to be able to spread using portable storage like thumbdrives or digital photo frames; A corresponding dropoff in overall worm detections has borne out the effectiveness of that update. And the social engineering tricks employed by malware gangs are, at least for the moment, repetitive enough that they’ve become fairly easy to identify. What follows is Webroot’s list of the five most egregious examples of malicious software that, even if some of them didn’t initially appear in 2009, progressed to serious threats throughout the past year.
It’s not clear whether the past year will go down in history as a particularly bad year for malware, but one thing is certain: It was bad enough, at times, that fighting infections and cleaning PCs took priority over virtually all other work. Neither home users nor businesses were immune from wave after wave of increasingly nasty malware tricks, though there were a few bright spots: A fix issued by Microsoft mid-year meant that worms are far less likely to be able to spread using portable storage like thumbdrives or digital photo frames; A corresponding dropoff in overall worm detections has borne out the effectiveness of that update. And the social engineering tricks employed by malware gangs are, at least for the moment, repetitive enough that they’ve become fairly easy to identify. What follows is Webroot’s list of the five most egregious examples of malicious software that, even if some of them didn’t initially appear in 2009, progressed to serious threats throughout the past year.
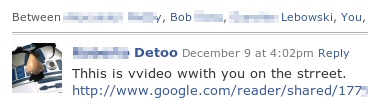
Worm-Koobface
Also ringing in the new year with 2009, the Koobface worm has now become the most serious threat facing users of social networks. Initially targeting users of Facebook, the worm — actually a complex, well-coordinated combination of malicious applications, each of which is designed to carry out specific tasks — continues to circulate within more than a dozen social networks. Koobface also brought to the fore the utility of social engineering (through PT Barnum-esque trickery) as a means for malware to propagate itself, not just infect an initial victim’s PC. Koobface almost represents its own branch on the family tree of malware, a malicious organism that can be used to distribute any number of undesirable files to an infected computer. The success of Koobface, and its continued development and improvement throughout 2009, shows no sign of abating into next year.
Trojan-Backdoor-Zbot
With Koobface highlighting the effectiveness of social engineering, others have joined the bandwagon. The second half of 2009 showed how trickery could lead to infections even with keyloggers as mature as Zbot, which has been seen in the wild in various forms since 2006. However, 2009 saw Zbot infections on the rise, as one or more malware gangs crafted coordinated spam campaigns that fooled recipients into believing that the messages’ legitimate origin were banks, or government organizations (both in the US and elsewhere), trade groups, or financial institutions, or even Microsoft itself. The A-list organizations spoofed by these campaigns read like a Fortune 100 who’s who list: Visa International, the IRS (and its UK counterpart the HMRC), DHL, FedEx, Chase, Bank of America, the US Postal Service, and the Federal Deposit Insurance Corporation, just to name a few. These spam messages, leading to fairly sophisticated fake Web pages, were put together with one goal in mind: To convince potential victims to download and execute the Trojan horse installer themselves. These campaigns show no sign of letup, and it’s not hard to foresee more of the same continuing into 2010.
Conficker
Virtually ignoring home users, Conficker spread like wildfire through business, government, and military networks, infecting an estimated 9 to 15 million networked Windows systems by the beginning of 2009. The worm’s effects, though indirect, were significant: Infected critical systems grounded French fighter jets, fubared hospitals, and forced corporations worldwide to spend months cleaning infected networks. But the worst problems were never realized, possibly due to the massive global attention drawn to the worm. Thanks to significant updates by Microsoft to Windows, the worm is essentially unable to propagate on up-to-date PCs.
Trojan-Backdoor-Stinkbreath
 One of the nastiest downloaders of recent memory, a Trojan we call Stinkbreath (others call it Bredolab) became more prominent in 2009, along with a simultaneous rise in the number of rogue antivirus infections (the rogue installers downloaded, natch, by this threat). Initially, the infection spreads when a spam message — almost always about some sort of product shipment or online order confirmation — containing a Trojan file attachment is opened, read, and the attachment executed. The downloader outwardly appears to be a distribution method-for-hire, as we observed the Trojan being used to distribute initially only rogue AVs, but later found it was used to push adware, ad clickers (a type of Trojan which commits fraud against advertising networks), rootkits, other downloaders, and remote backdoors, including Zbot, into the PCs of victims. While not as flashy or prominent as other downloaders, Stinkbreath has proven resilient and will probably continue to be seen into the coming year.
One of the nastiest downloaders of recent memory, a Trojan we call Stinkbreath (others call it Bredolab) became more prominent in 2009, along with a simultaneous rise in the number of rogue antivirus infections (the rogue installers downloaded, natch, by this threat). Initially, the infection spreads when a spam message — almost always about some sort of product shipment or online order confirmation — containing a Trojan file attachment is opened, read, and the attachment executed. The downloader outwardly appears to be a distribution method-for-hire, as we observed the Trojan being used to distribute initially only rogue AVs, but later found it was used to push adware, ad clickers (a type of Trojan which commits fraud against advertising networks), rootkits, other downloaders, and remote backdoors, including Zbot, into the PCs of victims. While not as flashy or prominent as other downloaders, Stinkbreath has proven resilient and will probably continue to be seen into the coming year.
Trojan-Backdoor-TDSS
Along with Stinkbreath, Trojan-Backdoor-TDSS is one of the most pervasive downloaders in the wild. It also appears to be used as a gun-for-hire method of distribution for a wide array of malicious programs. Its bundled rootkit (which, in early versions, prepended “TDSS” to the file names of various malicious payloads) is among the most challenging to remove, and remains a thorn in the side of victims. Its use appears to have fallen off in recent months, but not due to any apparent reason. As it remains an enigmatic, difficult spy to remove, I’m not willing to write it off just yet. I don’t think it’s unreasonable to predict that the world may see a resurgence of TDSS infections next year, though I sincerely hope we don’t.



















There is a possibility that someone manually put a key logger on my laptop while I was away from my computer. I’m not a computer person, but I will try to ask this question clearly. Is this different than key loggers and spywares that invade through the internet? More importantly, can Webroot detect if someone manually put something in my computer that remotely tracks my key strokes, emails, online banking etc? Currently, I have Norton and the OS is Vista if you need to know.
Commercial keyloggers are tools that are sold for this purpose; They are designed to be installed by someone with physical access to the machine (as opposed to someone who unluckily clicks a malicious link or is tricked into launching a Zbot installer, for example). Yes, they are different, though some commercial keyloggers are able to steal similar or the same information that Zbot can.
To your second question, Webroot devotes a significant amount of energy and time into researching commercial keyloggers for the simple reason that few other companies make the effort. We believe we have the best detection of commercial keyloggers in the industry, but don’t take my word for it. There’s a link to download a free scan near the top of the page; Go ahead and give it a try.
Getting back to the social net-working problems, I’ve noticed a few attempts to infiltrate my PC, after leaving comments on blogs. The site page keeps trying to re-load after I’ve exited the site. Blogs I’ve been to many times are now doing the same thing and it seems to be on the increase. I have to shut down each time and re-boot. I’m currently using Webroot Essentials with the latest updates and all shields are up. The latest scan came back clean but past nes are finding quite a few spyware apps.
Is there a way to scan apps on a blog? Especially the comment box apps? Or am I just crying wolf?
Todd, I’ve looked over your blog post about this topic, and it looks like you’re seeing our product detect and remove tracking cookies. These are not attempts to infiltrate your PC.
I have seen numerous postings about “Trojan-Backdoor-stink breath” but no one seems to have any info about removing it permanently. Every time it is removed and the PC is re-booted, it is found again on the next scan. I am amazed to find that McAfee and Norton apparently aren’t even aware that it exists, as it is not listed in their “Threats”. How can it be removed permanently?