 A new variant of the Koobface worm started striking out this week, with a twist: Where the older Koobface would steal and use the cookies saved by Internet Explorer which store social network logins in order to spread its infectious messages in the victim’s name, this new variant is pulling down a tool designed to steal credentials saved by Firefox (in the form of cookies and stored passwords). Users of the Firefox browser were, until now, able to thwart the pernicious spy’s ability to hijack a victim’s social network accounts, because the two browsers store their cookies in different locations, and in different formats.
A new variant of the Koobface worm started striking out this week, with a twist: Where the older Koobface would steal and use the cookies saved by Internet Explorer which store social network logins in order to spread its infectious messages in the victim’s name, this new variant is pulling down a tool designed to steal credentials saved by Firefox (in the form of cookies and stored passwords). Users of the Firefox browser were, until now, able to thwart the pernicious spy’s ability to hijack a victim’s social network accounts, because the two browsers store their cookies in different locations, and in different formats.
We got wind of the new variant as we saw the characteristic links spreading through various networks yesterday. In our early tests, the worm exhibited similiar skill at spreading over multiple networks: In addition to Facebook, the MySpace, Hi5, Friendster, Tagged and Netlog accounts we use for testing its behavior were used to spread malicious links, posted either to the victim’s “wall” or status, or as messages sent to all of the account-holder’s friends.
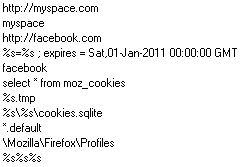
Using a well-documented hack to access the Firefox cookie file, the payload (appropriately named ff2ie.exe) looks for a copy of the file sqlite3.dll on the victim’s hard drive, then uses the functionality of that file to pull social network cookie information from the Firefox cookie database (as shown in the screenshot, above), and write an Internet Explorer cookie containing all that information. With the IE cookie(s) in place, the rest of the Koobface payloads work as they did before.
The worm continues to query the download server for payloads targeting 10 social networking services, but for an undetermined reason, it only delivered six targeted payloads. We also saw that, instead of downloading the executable payloads directly, the worm downloaded installers, each of which place various payloads in the Windows folder, then self-delete.
The social networks are not sitting still, though. We observed them doing a better job at hardening their messaging mechanisms against Koobface. MySpace, which automatically passes all links attached to Status updates through its internal link-shortener service, immediately locked out the account attached to our infected user and displayed its “your account has been phished” warning message. Though that’s not technically correct, we’ll give them credit for using their internal mechaism to engage an immediate and effective lockdown, which halted our Koobface-infected PC’s ability to post anything to the account. And the random, unpredictable use of Captcha technology on several sites blocked the worm from sending personal messages (but, notably, didn’t prevent it from posting malicious links on the walls of the victim or other Facebook users in the victim’s friends list).
Here’s a quick screenshot, showing the program looking for any Facebook cookies stored in IE, deleting them, then writing a new cookie with the information gleaned from the Firefox cookie file.
It should be noted that the entire act of moving the cookie data took under 5 seconds, from execution to self-immolation of the ff2ie.exe file.
This latest spin to the Koobface “brand” means there’s one fewer weak link in its chain of destruction. It also signals an acknowledgment by the malware designers that the market share of Firefox is now significant enough, with a sufficiently large user base to merit the development of a tool targeting that specific browser — a backhanded compliment, for sure, and an acknowledgment that new development of the worm continues undeterred.




















Hi:
I just registered with blog.webroot.com.
I’m planning to search round a while and come across interesting people and learn several tips.
Hopefully this message idn’t get posted in an inappropriate section. I am sorry if it does.
——————–
GRANVILLE SHERMAN
Cook (Private Household)