 Over the past several months, we’ve seen Koobface steadily progress in its ability to infect systems with malware. In our latest tests, we’ve found that the most recent version of this social-networm has a few new holiday-themed tricks up its sleeve. Among those tricks are a new, improved “captcha breaker” utility; A tool to check whether you have a Google and/or a Blogspot account (and, if not, it creates a new Google account); And a tool designed to create Google Reader pages on the fly, which the worm then uses to post malicious code. Those Google Reader accounts then end up linked in private messages and wall-to-wall posts on a variety of social network sites.
Over the past several months, we’ve seen Koobface steadily progress in its ability to infect systems with malware. In our latest tests, we’ve found that the most recent version of this social-networm has a few new holiday-themed tricks up its sleeve. Among those tricks are a new, improved “captcha breaker” utility; A tool to check whether you have a Google and/or a Blogspot account (and, if not, it creates a new Google account); And a tool designed to create Google Reader pages on the fly, which the worm then uses to post malicious code. Those Google Reader accounts then end up linked in private messages and wall-to-wall posts on a variety of social network sites.
The Koobface-generated Google Reader pages have been floating around for a little while now, but I’d never seen the worm in action. What I found fascinating was that I could observe the process of the worm creating a new Google account on my testbed.
 In order to create the Google account, it downloaded and ran four new applications: “v2googlecheck” simply looks at your browser cookies to determine whether you already have a Google account; “v2newblogger” creates a new account if one doesn’t already exist; “v2captcha” prompts the user of the infected machine to enter a captcha into a dialog box that looks like a Windows login dialog (in order to complete the account creation); and “v2reader,” which creates the new page, and passes that information to the worm.
In order to create the Google account, it downloaded and ran four new applications: “v2googlecheck” simply looks at your browser cookies to determine whether you already have a Google account; “v2newblogger” creates a new account if one doesn’t already exist; “v2captcha” prompts the user of the infected machine to enter a captcha into a dialog box that looks like a Windows login dialog (in order to complete the account creation); and “v2reader,” which creates the new page, and passes that information to the worm.
Once the Google account is created, it then uses that account to generate a new, malicious Google Reader page.
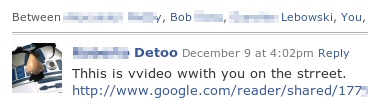
These worm-generated pages look identical, with the exception of the Google Reader user’s name at the top of the page. Each of them appears to be a link to a Google Reader “shared items” page — files that Google Reader users can post for others to download. In this case, the shared item appears to link to a YouTube video, but the “video” link is just an animated GIF image.
Links to these Google Reader pages are what the worm posts — there’s almost no way for Facebook to keep up with new pages being created on-the-fly by the worm, and because this all happens at breakneck speed, the links often remain active for some time. As soon as it has created the malicious account, it logs out the user from the spontaneously-created Google account.
In addition, Facebook’s user account mechanism used to be able to detect when an infected machine attempted to post these kinds of links, and locked out the account immediately. With the use of these Google Reader pages, the links (and infected accounts) remain active for a much longer time.
When the user clicks the “video” link in Google Reader, they’re redirected to a different fake-video page. This page looks more familiar, because this trick (and a page with almost the same appearance) has been used for some time by Koobface. The “video” on this second page is just a black box with a small message that says “This content requires Adobe Flash Player 10.37. Would you like to install it now?” In fact, the entire page is just a single GIF image; Clicking the video on this page — or anywhere on the page, for that matter — brings up a download dialog for a program called Setup.exe. This program is yet another Koobface installer.
The final result is that the worm links to the spontaneously created Google Reader page on Facebook, Bebo, Twitter, Hi5, and a number of other networks and services on which the Threat Research team maintains a linked network of bogus accounts.
For now, if you see links to Google Reader pages posted in your social network, keep your guard up. And if you see someone in your network posting these links, drop them a line to let them know they might be infected.























How do you get rid of Koobface…will Webroot detect and delete
Yes, we can handily take care of Koobface.