![]() The latest generation of Koobface targets its particularly effective brand of social engineering at more social networks than ever. As the worm has evolved, we’ve seen it grow to encompass a pantheon of services, targeting more than just the widely publicized Facebook, MySpace, and Twitter, but a host of other Web sites where people meet and (apparently) post links of funny videos for one another to watch.
The latest generation of Koobface targets its particularly effective brand of social engineering at more social networks than ever. As the worm has evolved, we’ve seen it grow to encompass a pantheon of services, targeting more than just the widely publicized Facebook, MySpace, and Twitter, but a host of other Web sites where people meet and (apparently) post links of funny videos for one another to watch.
To illustrate how pervasive the worm has become at propagation, we put together the video below. (And no, you don’t need to download some random codec to watch it, just Flash.) If you’ve got two minutes, check it out, but to get the best view, maximize the video window first (click the little “X” next to “vimeo” in the lower-right corner):
[vimeo 6105480]
For our test, several members of Webroot’s Threat Research team created profiles on the social networks Koobface attempts to infiltrate, logged into those accounts on test computers, then executed the worm’s main installer application.
The worm checks to see which sites among the ones it targets that you’ve logged in to, and downloads specific payloads for each social networking site it targets. That makes sense: Each of those social networks has its own distinct user interface, which the payload targeting that site interacts with. But the sites all have one thing in common: They all permit members to send one another messages containing hotlinked URLs. And that’s what Koobface is best at: Propagating itself by sending links. Nothing surprised us more than finding that we could actually watch the worm interacting with the interface, filling in forms and clicking buttons, as we stared at the screen.
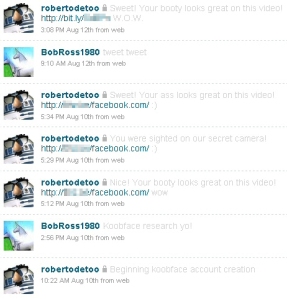
The content of the messages were typically brief: Message text sometimes consisted of a single acronym, like “LOL,” and at other times a short phrase, such as “Sweet! Your booty looks great on this video!” or “You were sighted on our secret camera!” Smileys accompanied most of the messages, and because everyone knows that malware doesn’t smile or wink, it was a perfect disguise. 😛
On Twitter, the worm merely posts a new tweet, once during the initial infection, and periodically thereafter (with the tweeted links using link-shortener services like bit.ly to obfuscate the destination).
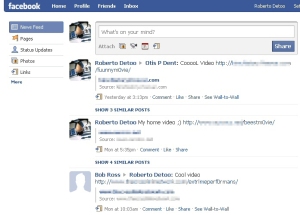
On MySpace, the worm changes the account user’s “Status” by modifying the text and adding a link (which MySpace helpfully obfuscates by changing the link to one that uses its own automatic URL shortening service). Facebook users get a triple-threat: The worm posts links on the infected user’s wall, posts different links on the walls of the infected user’s friends, and also sends yet a third link to all of the infected user’s friends through the service’s Compose Messages page.
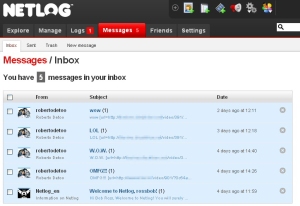
In Bebo, Netlog, Hi5, and other services, the worm sends short, private text messages and URLs to all of the user’s friends, but it doesn’t appear to interact with other aspects of the user’s account profile. After it sends these messages, the worm then goes into the sent-messages folder and deletes the record of the message out of the account. Curiously, on the Bebo service, Koobface also attempted to send one of its links to the site’s support team through the user-to-user messaging interface, but the site rejected the message with an error that indicates that the support staff no longer can receive messages in this way. I guess they got tired of getting infected.
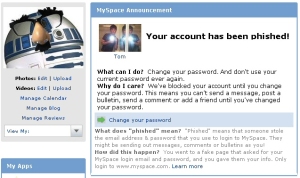
The sites also behaved differently, depending on whether they detected funny business: Facebook periodically locked out the account of the infected users, until those users logged in again from another computer. MySpace not only locked out an account, but forced the account holder to change the password. Of course, when we did that on the infected machine, we also provided someone with our account credentials. Overnight the following night, someone tried to log in to that account and change settings that would have permitted them to take control of the account, but MySpace once again locked the account and we had to change the password a third time. When we logged back in, the service displayed a message warning us that our account had been phished.
Several of the sites appear to use algorithms that flag private messages containing URLs, and challenge the worm to fill in a captcha field. According to reports published online, one of the payloads the worm has downloaded in the past has the ability to break captchas, but we didn’t observe this behavior. So on those sites, including Bebo, Tagged, and MyYearbook, the messages were created but never sent because the captcha blocked the process and the “captcha breaker” didn’t appear to be present, or didn’t work.
In fact, Koobface appears to have become a “brand name” in malware; its unfortunate prominence means we’re likely to see more evolutionary changes in its propagation methods and payloads the months to come, so please treat every social networking link with caution — especially the ones promising a link to a video.
Special thanks to Christoph Keller for giving us permission to use his masterful piano performance in our video.




















A friend put me on Facebook. It sounds like i should get my name removed and also tell my friends not to use this connection.
@ Olaon: You should definitely tell your friends not to follow any links that you, yourself, didn’t post. But there’s no reason to delete your Facebook account.
@ anyone who thinks they have a Koobface infection: You also need to clean your system and click the LOG OUT button in Facebook, so the worm doesn’t have the ability to continue to post links while you sort out your computer.
Hey thanks for the info here. I just had to format my computer a couple of weeks ago I had Win32 Scribble B.
I have had my laptop for 2yrs now and am so happy with my choice to go with Webroot Antivirus protection for my computer. It’s fantastic with sending me signals when something may not be right, when a sweep was missed, or a back-up is needed. I can count on it to give my computer the protection that it needs, and at the same time feel safe going on different sites such as you-tube. If there is too much traffic or it senses something isn’t right, Webroot will signal to me BEFORE getting on sites like that that it is not in my best interest to do so at that time. I just started a Facebook account a couple of months ago, and the info you’ve provided on the Koobface once again shows me that not only did I make the right choice in selecting your services as my protection for my PC, but shows me that you guys are on top of many things that are harmful to us. Thanks for making it easy to understand, and providing the great work you do!
I let my renewal to Webroot expire and just kept Norton. What a HUGE mistake!!! I got he malware/trojan horse and Norton kept popping up telling me it caught it. The malware started to block me from Symantec’s site as well as most anything that could provide information that could help. After two days of pure torture and bizarre pop-ups I istalled/updated Webroot and it caught five malware/trojanhorse/koobface issues. I am now virus free and running like a dream! Thanks Webroot! You are the best!! I have read nightmare on-line nightmares and wish they could all find out that you guys have solved the problem!!!!
a link to a video such as you described was sent to my facebook account. My anti-virus software recognized it and instructed me to isolate and delete it, which I did. Is there any chance that it is on my facebook page and corrupting messages that I send to my friends, without my being aware of it?