 Today’s the official kickoff for National Cyber Security Awareness Month, and the organizations supporting the event, including the National Cyber Security Alliance, the Anti-Phishing Working Group, and dozens of corporate citizens including Webroot, want you to protect your computer and your personal information. So they’ve come up with a three word campaign slogan they hope will become conventional wisdom for every Internet user: Stop. Think. Connect. Think of it as the 21st century equivalent of looking both ways before crossing the street.
Today’s the official kickoff for National Cyber Security Awareness Month, and the organizations supporting the event, including the National Cyber Security Alliance, the Anti-Phishing Working Group, and dozens of corporate citizens including Webroot, want you to protect your computer and your personal information. So they’ve come up with a three word campaign slogan they hope will become conventional wisdom for every Internet user: Stop. Think. Connect. Think of it as the 21st century equivalent of looking both ways before crossing the street.
In my case, they’re preaching to the choir. For years, I’ve advocated that people treat everything they see online critically, and to scrutinize information before acting on it. That’s because the army of criminals who commit fraud and theft over the Internet on a daily basis rely on you to not stop, not think, and to click links or open files immediately, without regard to the consequences of your actions. That’s how most people infect themselves. If you stop and think before you connect, you can prevent most of these infections yourself, simply by exercising a little restraint.
It’s hard to think of a major cybercrime outbreak over the past year that hasn’t relied, to some extent, on the naivete of its targets. Security professionals call these tricks “social engineering,” but that’s just a geeky term for criminal skullduggery that’s as common offline as online. The ruse almost always tries to invoke an adrenaline-fueled need for an immediate response — usually out of fear, greed, or panic — on the part of a victim. The victim ends up in a mental state where they are likely to make rash, impulsive decisions. And they do.
Putting the brakes on social engineering tricks usually takes all the steam out of them. To that end, I’d like to show you examples of five of the most common cyberscams that lead to the loss of personal information or sensitive data. Hopefully, if you know what to expect, you’ll simply walk away from the encounters unscathed.
Scam #1: Your computer is (not) infected (yet)
We’ve detailed in depth the lengths that some scam artists will go to convince you to hand over money willingly. The biggest criminal enterprise in this regard is the rogue antivirus product. Through deceit and trickery, the criminals behind rogue security products make an exceptional living for themselves by selling literally nothing to hapless victims.
The scam: Convince the victim that their computer is infected. Open popup windows with fake warning messages; hijack search engine results to launch bogus “antivirus scans”; place benign “malware” files on the victim’s computer; convince the victim to download and run a malicious executable, then refuse to remove the executable unless the victim pays an exhorbitant “license fee.”
How to avoid it: Most of these scams come from deliberately manipulated search results: You click the link and you’re sucked in — but it’s not too late. The minute you see a fakealert, stop everything you’re doing, kill the browser (use the Alt-F4 key combination if you need to), and perform a full scan with the legitimate antivirus product of your choice.
Scam #2: Someone you know sends you a message with a link
Ask anyone who uses social media, and they’ll tell you that nobody scrutinizes the links passed around by friends, until someone stumbles upon a drive-by download or a worm. Koobface is the archetypical example of malware that abuses the bond of interpersonal relationships in order to spread.
The scam: Send a social network user’s friends a brief message with a short URL. Make the short URL point to a page that convinces the user to download and run a “codec” or a “Flash update” program. When the victim runs the “codec” installer, infect the victim’s computer with a wide array of malicious programs, including keyloggers, rogue AV installers, and downloaders. Then hijack the victim’s own social network account(s) to continue the spread of the worm.
How to avoid it: Stop and think. Most shortlink services have a feature that lets you preview where the shortlink will go; Use it. If you’ve never heard of the Web site, check the true destination domain against a reputation service, such as Webroot’s Brightcloud. And don’t be the first one among your friends to click a link.
Scam #3: Someone you don’t know sends you a message with a link and/or an attached file
Even though you weren’t expecting anything, you receive an email from DHL informing you that a package destined for your address is being held at the local facility, and an attached shipping manifest will permit you to claim the package. Oops, that manifest is actually the installer for a keylogger, or a downloader, or some other undesirable junk.
The scam: Create a downloader or a keylogger, and give it an icon so it looks like a Word document, Excel spreadsheet, or a text file. Compress the file into a .zip archive. Spam out the file to 24 brajillion people, with a poorly worded sob story, a business contract, or an order confirmation message, and wait for the valuable data to come flooding back.
How to avoid it: Stop and think, then don’t click. Whether it’s a message that claims to be from the IRS; from a shipping company like DHL, UPS or FedEx; from a Web store like Amazon or iTunes; or from someone supposedly sending a resume, apartment application, or some other misdirected form, never, ever open those files, especially if they have a .exe extension. Uncheck the “Hide file extensions for known file types” option (instructions at the end of this post).
Scam #4: You receive an “invitation” to a service from a stranger
Juanita Uzmayo wants to be your friend on Yahoo. Frank Schmedlebeck wants to connect on LinkedIn. Sexy Beast has sent you a message on Facebook. Click here to…uh oh.
The scam: Set up a drive-by download site, Canadian Pharmacy page, or phishing page. Look at one of the automated messages sent out by a multitude of online services, such as Facebook, LinkedIn, Plaxo, or an instant messaging service. Duplicate the format and wording of that message, but instead of hotlinking to the service, tag the message with links to your malicious page instead.
How to avoid it: Without clicking anything, move the mouse over the link in your email message, then look at the Status Bar (along the bottom edge of the browser window) to see exactly where the link leads. If the message claims to come from one company, but the URL points to a domain you’ve never heard of, don’t click the link. See how easy that is? If you’re curious, check the domain against Brightcloud’s reputation database. Don’t have a Status Bar visible? Turn it on now. Click View -> Status Bar in most browsers.
Scam #5: Offer the victim something of value, steal credentials instead
Want 1600 points on Xbox Live? How about early access to the latest beta test for World of Warcraft? Maybe you’re interested in getting free stuff for your Habbo Hotel account. Do you want to know who is blocking you on MSN Messenger? Join our club, log into Steam, and get a free game. Just enter your username and password here, and we’ll send you your points/access/whatever in four to six weeks.
The scam: Create a Web page which uses the site graphics and design used by a legitimate company. Make outrageous, impossible-to-keep promises on the page. Stick a username and password field on the page. Program the page to submit any usernames and passwords that people enter into the form to you, and not to the real company the page claims to represent. Spam the world with links to the page. Profit.
How to avoid it: Stop, then think about it, and do not follow the link. TANSTAAFL, gamer boy. Does the page say “Blizzard” but the domain name in the URL contain 110mb.com, surge8.com, altervista.org, or t35.com? Those are legit, free Web hosting services, abused by cheapskate script kiddies, who set up temporary pages on those services in order to scam foolish people. There is no mechanism that can permit you to see who has blocked your IM account on MSN, Yahoo, ICQ, or anywhere else. Nobody’s going to give you anything for free. Provide your credentials, and you’re just going to lose control of your account (and probably that rare armor the mob dropped during the raid you participated in last week).
Of course, these aren’t the only scams in the world perpetrated against victims, only some of the most common. If something seems fishy, trust your gut and stop what you’re doing. Don’t worry about losing your place in the browser; It’s easy to retrace your steps, but hard to clean up an infected PC.



















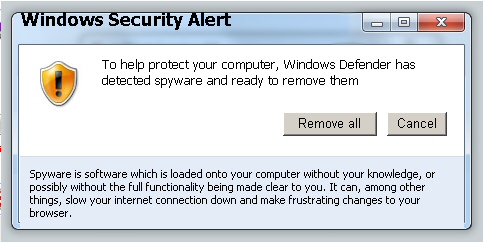


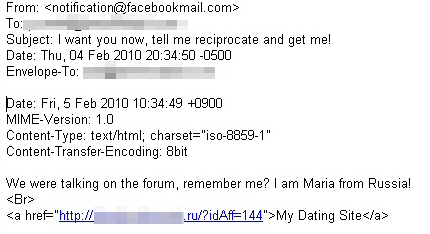
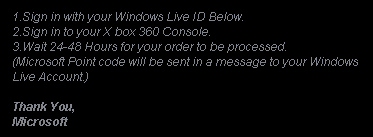
I’ve had a couple of people say that they want to be my friend on Yahoo, but I do not know them, so I just x’ed out of them. I’m glad I did, because I might have been scammed. I also got the Windows Defender one, but got out of that one right away, too.
I try to be as cautious as possible. Today, you can’t trust anyone. It is ashame that people are so filled with evil that they will do anything to destroy what’s good on the internet. It’s so sad.
THANK YOU FOR THIS ALERT AND ALL INFORMATION INCLUDED. i AM GOING TO SEND MUCH OF IT TO SEVERAL FRIENDS. I ALSO AM GOING TO “RESTABLISH” CERTAIN “RULES” REGARDING WHAT I WILL AND WILL NOT ACCEPT FROM FRIENDS.
If I get emails with a long string of addresses included, I will soon start blocking those email addresses until that stops! I will be composing a message to explain all this again and also to my “facebook” friends—-who have that THING! I refuse to be involved in it AT ALL! I have many “invitations” to join or can’t see thier posted pnhotos of trips, etc. UNLESS I join! then I have found those did NOT come from them but from facebook “INVADING” that friend’s “address book and automatically sedning that invitation!
There are reasons I am going to do this and incidences I have experiencd and ONLY the excellent Webroot security system we have had now for 3 years has saved me!
Thank you again and bless you all for your diligence!
C. Huber
Thanks for such a great article!
Thanks so much for this article. I got bitten by the fake security alert. It completely took over my computer and ended up costing me $200.00 to get fixed. That’s when I got introduced to Webroot and I couldn’t be happier. You have a wonderful product and I will be renewing when my time comes. Thanks once again.
Lord I think I got that Defender one it was insistent locked down my entire computer. they want you to buy the software to uninfect your computer.. well i tell you a trick too.. lots of time a anti virus or even spybot search and destroy will not get me out of. my Son has a few up his sleeve and you have to run your program with your computer in safemode to really get it out.
Dear Sir or Madam,
Re WEbroot warning letter
You emphasize “DON’T CLICK ON IT” when one receives a strange message from unknown senders.
You are wrong. The only way to get rid of an email is to first click on it, otherwise you cannot get rid of that particular email by hitting the DELETE BUTTON.
so please explain how one can delete a particular email without clicking on it
Thank you,
Karl Issel
are not correct when you say
I think you’re misunderstanding the difference between clicking a link embedded in an email message, and clicking the message as it appears in the list of messages you’ve received in Outlook Express. Of course you have to select the message to delete it. Just don’t click any of the suspicious links in the message body itself.
Good article. Honestly, these sorts of threats aren’t scary because my OS is Linux (less than 40 viruses, worms, etc developed annually for Linux as opposed to 60,000+ for Windows), but I’ll pass it on to family/friends who insist on sticking with Windows.
I have just about lost faith in all internet security. I’m beginning to think it’s a big joke that do nothing but rip us off. On July 31, 2008 I had an internet business a gift shop, I had just finish restocking my business, had a new face and everything. Later that day I decided to check my bank statement online and I saw where $100 was being transferred from my account to my online account at PayPal. Then I got an alert about funds being transferred from another bank where I have my checking. I phoned PayPal and ask them why are you taking money out of my saving. They said they were not doing that and they could do nothing until the funds posted into my account. I phoned the bank where my saving was and them I did not authorized this,
the same thing was happing at WAMU where I had my checking, I phoned them also. To make a long story short, 3 banks I notified all of them to what was happing. I was speaking with there security department.
Everyone one of them said to me, once the funds post just transfer them back. It took five days to post and at 3:00am while I was sleeping someone out there in cyber space was online every 5 or 10 minutes taking $100.00 out of each of my account until they could get no more. They even rack up $634.00 in non sufficent fund charges. The minute the funds hit PayPal they were gone. 3 security departments from 3 companies could not stop this when I notified them way before it happen. Who ever it was wipe me out, I lost my internet gift shop and to top it all off, I could not sue non of them. They refuse to give me an affidavite or even a statement saying my accounts had been compromise. I came close to being put out on the street because I could not pay my bills. I had the best microsoft had to offer in security, didn’t work. I now am trying a trial security called TREND Micro for 30 days. It seem to be working ok and it ends November 15, 2010. Can anyone tell me what happen with these security companies? It so hard for me to trust now. Thanks for listing.
I don’t know about the state of your computer, but it sounds to me like someone Phished your PayPal password and then used the account credentials to drain your savings.
Other than file a police report, I don’t know what to tell you. I’m sorry this happened, but PayPal is one of the most heavily targeted online financial services by criminals. All I can say is, while I feel for your loss, there are thousands of stories just like this one that I never hear about.
PayPal has an SMS Verification service that sends a six-digit code as a text message to your cellphone every time you try to log in. If you don’t enter the code as well as the username and password, PayPal won’t log you in. As a phishing prevention mechanism, it is extremely effective and I would urge you to sign up for this free service — if you haven’t lost faith in PayPal altogether and canceled your account by now.
Please update us when you know more.
-=A
My wife was on the PC last month doing some emails.We use Windows XP with all the free protection given to MSN subscibers. The computer was attacted by a barrage of viruses and spyware, all of which was stopped in it’s track by Webroot,McAfee and Windows XP. I did a Webroot sweep after the attact and found an issue Webroot quaratined it had four red bars ( guess that means bad news.) Any way it is in quaranteen now. The mistake I made during the attack was PANIC. I downloaded something but never opened it because of the information you and others provide, just threw it in the trash. About a week later a porn video pops up out of no where and runs on it’s own. Thank God I was on the computer at the time. Enjoyed the video but cleaned my video files after it ran. THANK You for your diligence in protecting amatuers like myself and family.
I’m happy to hear that things worked out.
Remember, the panic reaction is exactly what the scammers want you to have. When you panic, you don’t think and act on instinct, and for most people, that gets them into trouble.
-=A
I will be forwarding this article to my friends, family and co-workers. Nice and concise break down of the most common threats. Thanks!
A late response, I admit, but I only just search-landed here while following up on some t35.com spam issues.
“The minute you see a fakealert, stop everything you’re doing, kill the browser (use the Alt-F4 key combination if you need to), and perform a full scan with the legitimate antivirus product of your choice.”
If I may offer some info related to that, I usually suggest folks ignore everything they see, fight instinctive responses to click/close anything (the “rules” change when dealing with malicious activities, so what normally “closes” something might instead initiate more unwanted actions), and instead head right to whatever is necessary to immediately kill their Internet connection. Cable or DSL, pull the ethernet cable from the computer or modem, dial-up, the telephone chord, and wireless, the router or modem incoming cables, or even the power cord to one of those. If those are not handy, then use the quickest method to disable the Internet connection, such as switching a laptop’s “radio button” off. Isolate the malware, and cut off it’s connection to it’s “mothership”.
Regardless of what has occurred, this first action will guarantee nothing else gets delivered. And then folks should follow the other helpful guidelines you suggested.
Woah! I’m really digging the template/theme of this blog. It’s simple, yet effective. A lot of times it’s challenging to get that “perfect balance” between usability and visual appeal. I must say you’ve done a fantastic job with this. Additionally, the blog loads very fast for me on Chrome. Superb Blog!