 Liz Lemon should be livid. Jack would be damned angry…in a quiet, repressed sort of way.
Liz Lemon should be livid. Jack would be damned angry…in a quiet, repressed sort of way.
The rogue antivirus goons have taken on 30 Rock, the NBC meta-sitcom about the internal workings of a sketch comedy show.
In a subplot from last week’s episode (which I will recap for those who may have missed it), Alec Baldwin’s character teams up with one of the writing team to prank the rest of the writers. The two form a secret society named the Silver Panthers, and when the prank is successfully sprung on the unsuspecting writers, Baldwin’s character Jack begins to walk out of the room, but pauses, turns back to the victims, and ominously utters the (we assume) Silver Panther motto: “Circulus et Pruna.”
Latin scholars (who, I’m sure, are all ardent 30 Rock fans) probably chuckled when they heard Baldwin’s character utter the nonsense phrase “circle and (burning) charcoal (ember).” Or is it circle and plum? Meanwhile, the rest of us were left scratching our heads and wondering what the hell does that mean?
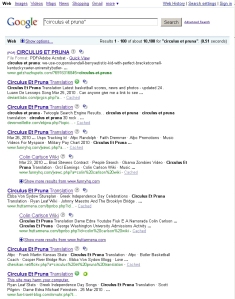
And so, turning to the font of all worldly knowledge, many Googled the phrase and may have been surprised to find that not one, not a few, but every search result on the first page (and most of the second page of results) led to a Fakealert trap that tries to force victims into downloading and running the installer for a Rogue Antivirus product.
The scoundrels.
It’s actually kind of an astonishing feat, as well as a horrific example of the current state of search results. When you consider that few, if any, outside Tina Fey’s production team had heard the phrase Circulus et Pruna uttered prior to last Thursday night at 9:30 (8:30 central), one has to wonder how the purveyors of these rogue antivirus products managed to wrest such total control of a nonsense Latin phrase from the world’s largest and (in theory) most comprehensive Internet search engine — mere moments after those words were spoken on television.
For the moment, the mechanism of their rogue SEO remains obscured. But the results are plain to see.
Every single website serving up a search result that leads into the Fakealert appear to be honest-to-goodness legitimate Web sites that had been hijacked by the rogues. In the screenshot below (click for the full size version), you can see the results from two Firefox plugins designed to render a verdict on the safety of search results: McAfee’s SiteAdvisor and Web of Trust. Both services were totally stymied by the use of legitimate sites to host the bad code.
But those hacked sites are just the event horizon of a black hole that leads victims’ browsers to load Web pages that are so malicious, even light cannot escape. OK, that’s an exaggeration. The hacked sites redirect the browser into various subdomains on the xorg.pl Web site. Xorg is a Polish Web site that provides free subdomains, much like various Dynamic DNS services or free Web hosts elsewhere. Criminals have a tendency to abuse services such as these for a short period of time, then move on to another when the heat is on.
We saw no fewer than three versions of Javascripted Fakealerts, one of which I hadn’t seen before. Here’s what one of the new fake virus scan screens looks like (click for a larger image). Note that, at the bottom of the window, it claims that the victim is running Internet Explorer 7.0 on Windows Vista — even though my test system in this case is running Internet Explorer 6 on Windows XP. D’oh.
Once the “scan” is complete, the page greys out the background and pops another image that looks like a popup from the Windows Security Center control panel into the foreground.
As with all previously seen Javascript Fakealerts, it doesn’t matter where or what you click. The page will attempt to foist an installer for a Rogue Antivirus product onto your computer. As with previous pages of this type, killing the browser with the Alt-F4 key combination works wonders at getting rid of this nastiness.
Meanwhile, the rogue behind this is nasty in its own right. Oddly enough, the installer calls itself “Love lines.” It uses the same padlock icon as many other rogue installers. The filename of the installer typically follows a pattern resembling “packupdate_build(number)_(number).exe” with the first number being a single digit, and the second number three digits long. Each time we attempted to download the file, we got an identical file with a different name that followed this pattern.
I also saw at least one fake video page that attempted to push an installer for the Security Tool rogue at my test machine. This one used the filename hd_codec.exe but the same icon of a blue shield with five circles inside that the rogue calling itself Security Tool has been using for months.
I think the bottom line isn’t so clear anymore. It’s not reasonable to suggest that you not use a major search engine. However, it’s prudent to use extreme care with any search engine nowadays. Up-to-date antivirus software with current definitions are a must. The Firefox browser with the NoScript add-on is essentially the only browser combination you can rely upon for moderately safe surfing, because this particular pairing of browser and add-on does not permit any of the malicious Javascript — the stuff that starts the problems in the first place — to run.






















It’s not ‘Circulus’. It’s ‘Surculus’.
That’s what you got from the article?
Nerd.