 Late Monday, after news about the death of troubled pop singer Amy Winehouse had been circling the globe for a little more than 48 hours, we saw the first malware appear that used the singer’s name as a social engineering trick to entice victims to run the malicious file. Abusing celebrity names, news, or even deaths isn’t a new (or even particularly interesting) social engineering tactic, but there was one unique aspect to this particular malware’s behavior that raised some eyebrows around here: It appears that Brazilian phisher-Trojan writers seem to be working more closely with their Chinese counterparts, using servers in China as dead drops for their stolen goods.
Late Monday, after news about the death of troubled pop singer Amy Winehouse had been circling the globe for a little more than 48 hours, we saw the first malware appear that used the singer’s name as a social engineering trick to entice victims to run the malicious file. Abusing celebrity names, news, or even deaths isn’t a new (or even particularly interesting) social engineering tactic, but there was one unique aspect to this particular malware’s behavior that raised some eyebrows around here: It appears that Brazilian phisher-Trojan writers seem to be working more closely with their Chinese counterparts, using servers in China as dead drops for their stolen goods.
The widely-reported case of the malware campaign continues to distribute new, randomized files via a download link managed through a dynamic DNS service, more than a week on. The file’s name, in Portugese, (“103684policia-inglesa-divulga-fotos-do-corpo-da-cantora-amy-winehouse-WVA.exe“) translates roughly to English police divulge photos of singer Amy Winehouse’s corpse, but victims who open this file are only going to see their computer become compromised.
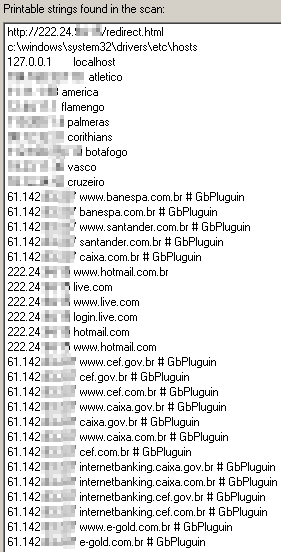
The malware modifies the Hosts file in Windows to redirect traffic from 78 different Web sites — the vast majority of which are Brazilian banks and finance sites such as e-gold, with the rest being American Express, and Microsoft‘s Brazilian and US domains for Hotmail, Live, and MSN — to one of 9 IP addresses, almost all of which point to servers hosted in Chinese networks. One oddball outlier IP address in the modified Hosts file list points to an IP address belonging to the network operated by the Ford Motor Company, but that IP address was not allocated to an operational server when I did some tests.
It’s been a longstanding pattern that most malware originating in Brazil are bank phishing Trojans. We’ve been seeing Brazilian phishing gangs steal bank credentials (and, presumably, money) from their fellow countrymen and -women for more than five years now.
In fact, most AV vendors (including us) lump all members of the extended family of relatively low-tech Trojans targeting banks in South America into a single definition, called SABanks. But the Brazilian phishers typically keep the stolen data within their country’s (or at least their continent’s) borders, on dead drops inside of compromised Web servers.
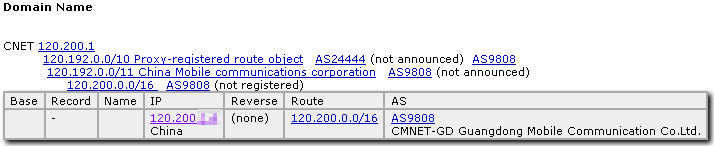
In the case of this Trojan, most of the IP addresses listed in the modified Hosts file point to servers in various Chinese networks, including one IP address range assigned to Guangdong Mobile, and several assigned to China Telecom.
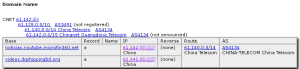
Interestingly, the malware authors appear to have divided the phishing pages associated with certain Web sites with specific IP addresses: Phishing for Hotmail, Live.com, and MSN happen on an IP address associated with the China Education and Research Network Center network, physically located in Beijing at Tsinghua University.
The phishing pages are fairly clean looking, but that’s because they’ve been built using GIFs made from screenshots of the real login pages of the Web sites they’re trying to phish from. So, of course, they’re virtually identical to the Brazilian pages the targeted victims would normally see.
That doesn’t mean that the people behind this campaign are smart, however: When a victim enters credentials into those phishing pages, the pages attempt (as is typically done) to redirect the victim’s browser back to the legitimate Web site, but there’s an unintended consequence of the malware-modified Hosts file. The phishing page simply redirects users back to the root of the phishing server, which has no index page, and is unprotected and wide open for anyone to browse from an infected computer.
So instead of seeing, for example, the Live.com home page after their credentials were stolen, phishing victims see this:
The phishers also did something else incredibly, unbelievably dumb (I know, hard to believe, right?): They did nothing to encrypt, mask, or hide the stolen data, which has been collected at a rate of approximately two to ten credentials per minute since 9:56pm on the evening of July 21st.
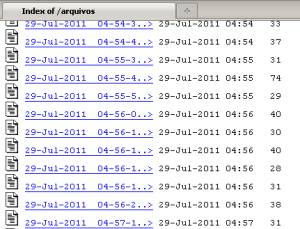
All the stolen passwords — willingly given (sometimes several times over) by the owners of infected computers — reside in text files on the same server hosting the phishing pages, inside a subfolder named arquivos in the same directory as the phishing pages.
Yeah, whoopsie doodle there, malware morons. Better luck next time.
Compromised accounts on Hotmail and other free email services are becoming the most popular way for spammers to spread their form of junk around the globe, and these credentials constitute a lot of raw materials for a spammer to hone into a finely crafted spam campaign.
As of last night, the phishers had taken more than 23,000 Hotmail credentials, which were the only stolen credentials stored on the server, and were accruing new or repeated entries of the same credentials at a rate of one to three per minute. When we informed Microsoft about the fact we’d discovered the large number of compromised accounts and asked for their assistance locking them down, the MSRC referred us to this page.
Taking a brief look at the credentials tells us a little about the security habits of Hotmail users. Out of a sample set of roughly 13,000 credentials, here are a few facepalm-worthy stats:
- More than 3800 people used only numbers in their passwords (with one user’s password consisting of 32 4s in a row).
- 64 of those users had a password of “123456” and 17 more went the extra mile with “1234567”
- Several users’ passwords were just words that indicate or describe their profession (eg., “abogado” – lawyer)
- At least 10% of the users included some form of their name, or part of the account name, in their password
- Two users’ passwords were the same as their email address
- 14 of those phished credentials appear to belong to accounts used by officers in the Policía Nacional de Colombia (and five of those 14 accounts use six-digit numbers for passwords)
Several people who were not fooled by the phishing pages left the phishers messages, most of which involved helpful, if aggressive, suggestions that the phishers insert one body part into another. Among the less hostile comments was one which translates roughly to unlucky hacker, use your intellect to help humanity.
We’ve thrown the malicious IP addresses associated with these attacks into our blocklists, added detection for the Trojan and its behaviors to our various products, and tried to inform Microsoft about the stolen credentials. But even seven days on, the Trojan is still collecting several credentials per minute from unsuspecting (mainly Brazilian) infection victims. We can only hope the victims will find that Microsoft, and not some cybercriminal goon, has locked them out of their email and IM accounts until they can change their password.