The thriving cybercrime underground marketplace has a lot to offer. From DIY botnet builders, DIY DDoS platforms, to platforms for executing clickjacking and likejacking campaigns, next to drive-by malware attacks, the ecosystem is always a step ahead of the industry established to fight back.
Continuing the “A peek inside…” series, in this post I will profile yet another freely available DIY Botnet building tool – the Umbra Malware Loader.
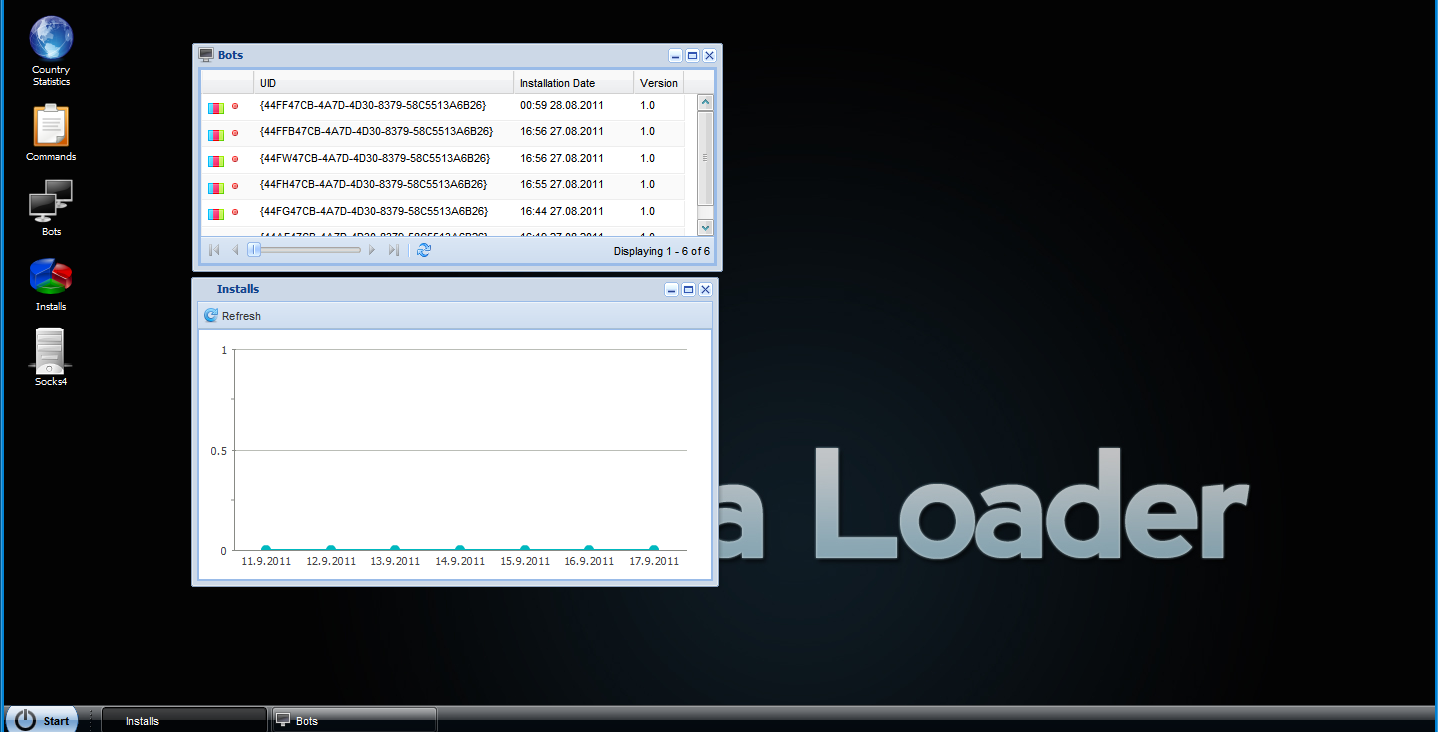
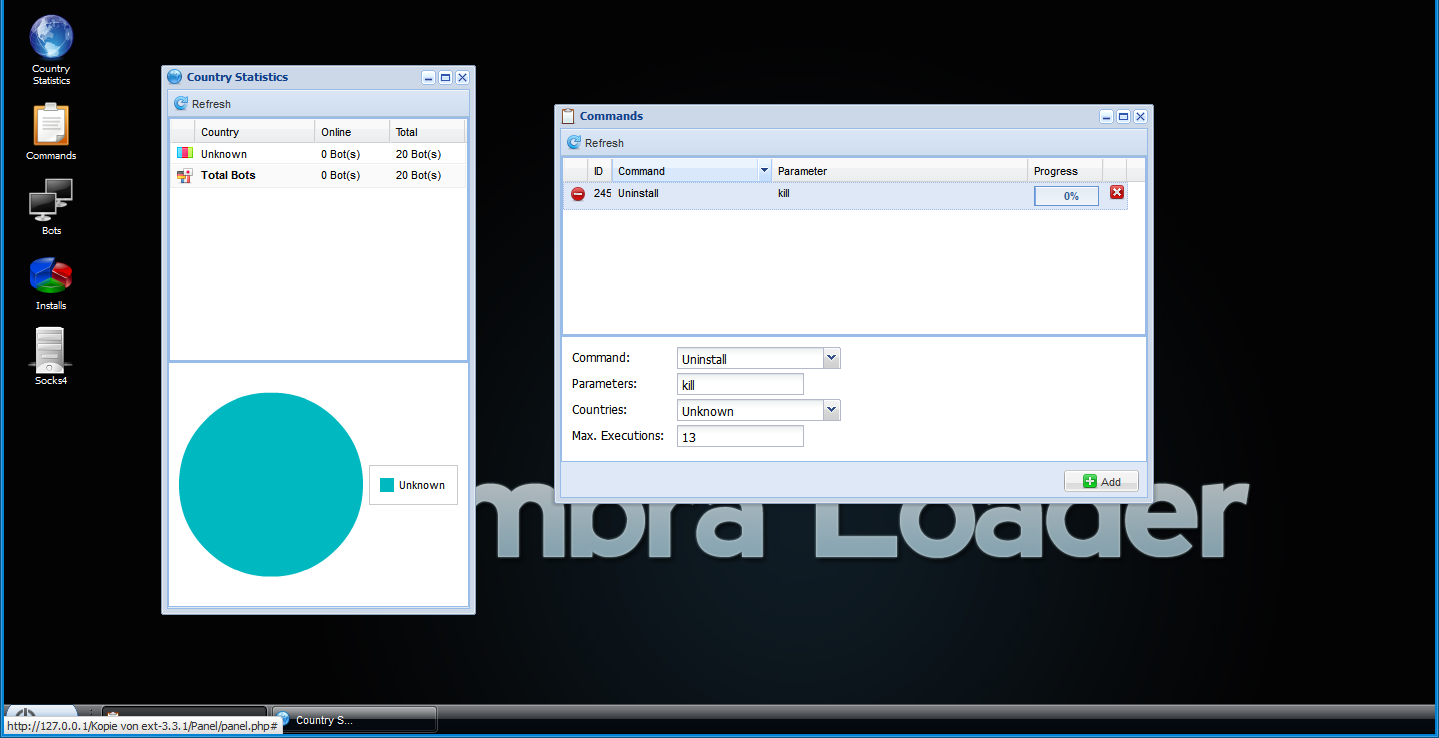
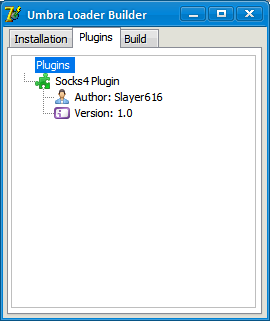
Screenshots of Umbra Malware Loader’s command and control interface:
Some of its core features include:
Changelog:
[+] Webpanel-Layout
[+] Installs
[+] Bots
[+] Builder with Plugin support
[+] Webpanel-Autoinstaller[*] Unicode-compatible
[-] Plugincommand (use Builder/update function for plugins)
What’s particularly interesting about the Umbra Malware Loader is its modular nature, namely malicious attackers can easily introduce new features while using some of the already coded plugins, next to the ones offered as a managed service.
Today’s modern malware is released in DIY fashion; it’s highly customizable, it’s localized in multiple languages, it comes with detailed instructions and HOWTO’s, and most importantly additional features including coding a new one from scratch, are available as a managed service.
Webroot’s security team is currently in a process of analyzing the Umbra Malware Loader. Details will be posted as soon as new data is gathered.
Related posts:
- A peek inside the PickPocket Botnet
- A peek inside the Cythosia v2 DDoS Bot
- Inside a clickjacking/likejacking scam distribution platform for Facebook
- Inside AnonJDB – a Java based malware distribution platforms for drive-by downloads
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Cool design of c&c.:)
I’ll be looking forward to the details that will be posted in the near future…This is what my partner was looking for because he had 28 sites to work right now…Seems like the fight is continualy doing the I’m number one, then the other is number one, then other…Thanks for keeping us in the fight…I want to win! Malware is a strange animal…Need deeper understanding…Seems like with your knowledge you’re able to carve a business out of it…thx