by Dancho Danchev
With DDoS extortion and DDoS for hire attacks proliferating, next to the ever decreasing price for renting a botnet, it shouldn’t come as a surprise that cybercriminals are constantly experimenting with new DDoS tools.
In this post, I’ll profile a newly released DDoS bot, namely v2 of the Cythosia DDoS bot.
The Cythosia DDoS bot is available for a free download at selected cybercrime-friendly online communities.
Some of its core features include:
# Runs on Win2k – Win7 / x86 and x64
~ Limited/Guest/Administrator Acconts
# Various Autostart Names and Entries
– Main Functions:
+ Download & Execute
+ Update– Distributed Denial of Service Functions
+ Syn
~ 20 Bots can kill little Sites
~ Customizeable Port & Strength(Http, Sql, Gameserver)
+ UDP
~ Perform attacks on homeconnections
~ Highly customizeable
+ HTTP
~ Multithreaded GET Requests – Generates Traffic as hell
~ Keeps GET Requests open– Socks5 Proxy
+ Opens Port with UPnP if router supports it
+ Redirects all TCP requests multithreaded -> very good speed
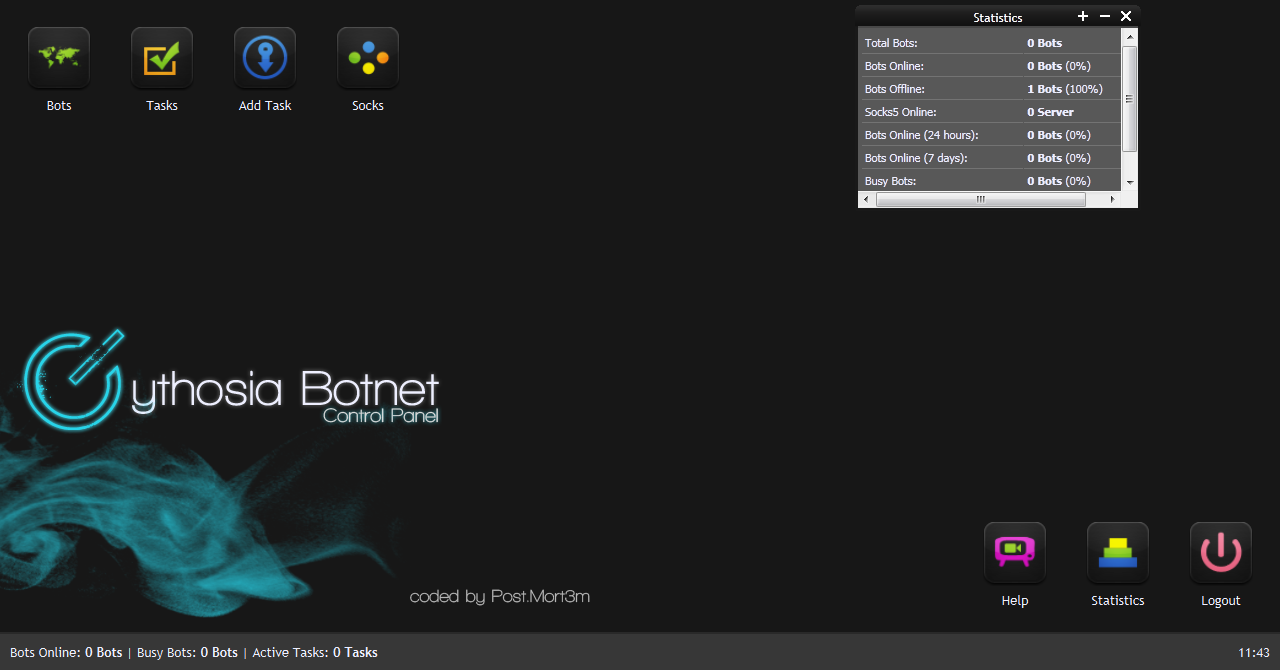
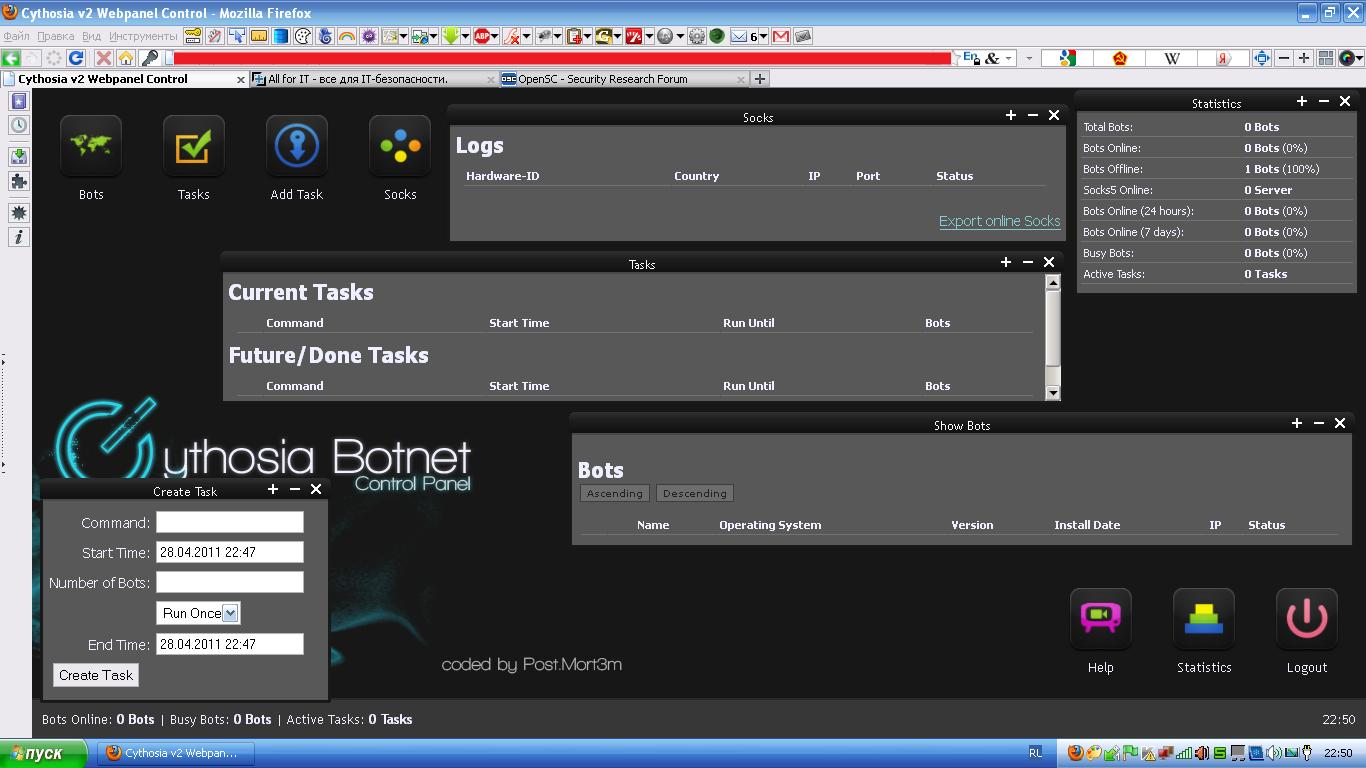
+ Configureable Username and Password– Control Panel
+ Nice looking Ajax Panel
+ Hardcoded Password -> secure
+ Taskmanagement System
+ Export Online SOCKS5 LIST
The DDoS bot supports SYN flooding, UDP flooding and HTTP flooding, and is highly customizable.
What’s particularly interesting is its support for Socks5 Proxies. These very same proxies will eventually be converted into anonymity services allowing cybercriminals the opportunity to mask their online activities. Thanks to such DIY DDoS bots such as Cythosia, the price for anonymizing a cybercriminal’s activities is constantly decreasing, and so is the price for launching a commissioned DDoS attack.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.