 If you’re a rock-and-roll star, anticipating the imminent arrival of a new recording contract from your lawyer, you can stop reading this post. If you’re not, I’m sorry to be the one to tell you, it was not your hours of practice playing Rock Band, or singing in the shower, that attracted the attention of the music industry. A spammed message, supposedly from a record company, which claims to have a contract attached, is (surprise!) malicious.
If you’re a rock-and-roll star, anticipating the imminent arrival of a new recording contract from your lawyer, you can stop reading this post. If you’re not, I’m sorry to be the one to tell you, it was not your hours of practice playing Rock Band, or singing in the shower, that attracted the attention of the music industry. A spammed message, supposedly from a record company, which claims to have a contract attached, is (surprise!) malicious.
The contract, in this case, is no contract at all, but a Trojan that can brick your computer if you run the file inside the Zip archive attached to the message.
We’ve been watching our favorite spam-propagated malware, Trojan-Downloader-Tacticlol (aka Oficla, Sasfis, Fregee, or Losabel). This is its new, extra stupid come-on of the moment. The message appears to come from Rock Out Records and says, in part:
“We have prepared a contract and added the paragraphs that you wanted to see in it. Our lawyers made alterations on the last page. If you agree with all the provisions we are ready to make the payment on Friday for the first consignment. We are enclosing the file with the prepared contract.”
In our tests of the Trojan, it pulls down a number of malicious payloads, some of which modify key Windows files responsible for the operation of the computer. As a consequence of the infection, your computer may not be able to boot up, instead leaving you stuck with a blue screen of despair.
Your first red flag would be the first word in the name of the Zip attachment, which is spelled conract — I’m pretty sure that, for a lawyer, misspelling the word contract is a flogging offense.
The fact that the filename also contains the date the message was sent in European day.month.year format might also raise eyebrows.
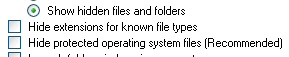
But the real danger sign is the fact that the Zip archive contains a file that has a Microsoft Word document icon, with a suffix of “.doc.exe,” which is one of the oldest stupid malware tricks there is—the fake file suffix dodge. For some reason, Microsoft felt it was necessary to ship operating systems set up so that the OS itself hides the true file extension of everything on the computer. You can turn off this inane feature, which does more harm than good, by clearing the Hide extensions for known file types checkbox in the Folder Options dialog in Windows Explorer.
When we ran the file on a testbed PC (it doesn’t set itself up properly on a VM), it pulled down half a dozen payloads, including Trojan-Pushu (aka Pushdo), a spambot, which immediately began attempting to spam Microsoft’s Hotmail, AOL Web mail, and Web.de (a German Web portal and mail host). This particular Pushu sample also modifies the Windows network card driver file Ndis.sys, which lets it communicate to its command and control server unimpeded by the Windows firewall.
Ironically, the Pushu payload sounds like it’s also themed along the lines of the music business.The payload’s name is “audiop2psound.dll” and it hooks into any running process on the infected machine.
But the worst part about this Tacticlol installation was the aftermath. Once I had collected my research data and logs, and copied them to another drive, I rebooted the machine to see what would happen next. As a result of a system modification, the PC would bluescreen the minute I powered it on. The machine was rendered unable to boot, even into Safe Mode.
Whether this was a deliberate consequence of the infection, or an accident the result of poor quality assurance by some dumb malware coder, doesn’t matter. The box was bricked. Reimaging the hard drive was the only way I could bring the hard drive back to life. Fortunately for our customers, our detections for these spies have been updated, so the File System Shield will block them as soon as they’re written to your hard drive.




















How about getting an e-mail about winning the lottery, needing help with millions of a late African president or how about a Russian company that needs help collecting from a U.S. company?
Recently I got an e-mail written in such poor English only matched by the request – passport photocopy, SSN, full name, bank account number and full address.
Are there people that actually fall into such a bad trap?