 Yet another new phishing campaign targeting users of Facebook struck over the Halloween holiday weekend. After scammers began filling inboxes last week with bogus “Facebook update” attachments, this weekend we saw a different group at work. Employing URLs with random domain names registered under the .eu top-level domain, the campaign looks similar to messages distributed in a recent series of phishing campaigns that attempt to convince the user that the mail comes from a legitimate source, such as the FDIC, IRS, HMRC (the UK’s tax authority), your IT department, or any of several well-known banks.
Yet another new phishing campaign targeting users of Facebook struck over the Halloween holiday weekend. After scammers began filling inboxes last week with bogus “Facebook update” attachments, this weekend we saw a different group at work. Employing URLs with random domain names registered under the .eu top-level domain, the campaign looks similar to messages distributed in a recent series of phishing campaigns that attempt to convince the user that the mail comes from a legitimate source, such as the FDIC, IRS, HMRC (the UK’s tax authority), your IT department, or any of several well-known banks.
The email messages, which use a forged From: address that makes the message appear to originate from the legitimate facebookmail.com domain, and were timed for just after Facebook’s highly publicized changes to its homepage had just gone live, clearly indicate that the phishers were going for the jugular. When you follow the link, you’re presented with a login dialog identical to that used by Facebook. Once you enter your password into that form, you’re presented with a page titled “Account Update” where you’re prompted to download and execute something called the Facebook Update Tool.
The messages read, in part:
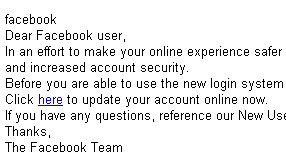
In an effort to make your online experience safer and more enjoyable, Facebook will be implementing a new login system that will affect all Facebook users. These changes will offer new features and increased account security. Before you are able to use the new login system, you will be required to update your account.
…followed by the typical tease to “click here” and a link-that-doesn’t-lead-where-you-think-it-will. The URLs in the message begin with “www.facebook.com” but that’s part of the ruse: The full URL is www.facebook.com.(some random letters).eu followed by a query string that includes a long string of numbers and the recipient’s email address (see example).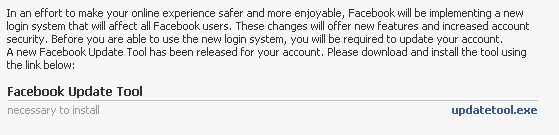
In the past, links formatted in precisely the same way led directly to pages hosting versions of the Trojan-Backdoor-Progdav (aka Zbot) keylogger. That’s also true in this case. So the bad guys don’t just want your Facebook password. They want all of your passwords.
We’ve seen a lot of this style of phishing campaign just in the past few weeks and if history serves as a guide, the small number of links in the spam messages we received over the weekend will likely be followed by dozens more versions, each with a distinct URL. Facebook users would be well advised to refrain from following the links in the message; If you suspect that you’ve inadvertently fallen victim to this dirty trick, change your Facebook password immediately — from another computer.



















Ugh, not another one. I work for Thawte and we’re thinking that keylogging and phishing scams will only get more popular as the holidays draw near and people become willing to type their personal info into online boxes to ensure that presents arrive at their destinations on time. It’s quite unfortunate that Facebook and Twitter don’t have extended validation ssl implemented, since the loss of “green” in fake urls would be a pretty good tip off. Either way the advice above is excellent, and one should also never use the same password for multiple sites and applications if they can help it — one slip could give hackers access to everything.