It was a particularly busy weekend for spammers, especially the creepy, evil ones who are trying to steal information (as opposed to the merely scungy pill vendors and their ilk). Webroot’s Threat Research team has recently seen a glut of phishing messages which, like most, purport to come from banks and ask you to update your account information. But unlike most phishing messages, which contain a link to a Web site, these phishing messages include an attached HTML file which, in essence, puts the phishing page right on your hard drive.
It was a particularly busy weekend for spammers, especially the creepy, evil ones who are trying to steal information (as opposed to the merely scungy pill vendors and their ilk). Webroot’s Threat Research team has recently seen a glut of phishing messages which, like most, purport to come from banks and ask you to update your account information. But unlike most phishing messages, which contain a link to a Web site, these phishing messages include an attached HTML file which, in essence, puts the phishing page right on your hard drive.
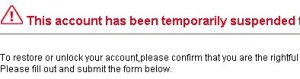
When launched, the HTML file renders a sparse but effective phishing form in the browser. The pages warn the victim that “This account has been temporarily suspended for security reasons” and ask the victim to “confirm that you are the rightful owner of this account” — by providing the “bank” with a wide range of personally identifiable information they should already have, and never would ask you to provide through a Web-based form in the circumstances described in the message.
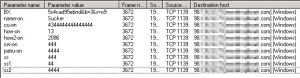
 These pages also pull graphics from the banks’ Web sites–activity that, when it comes from a phishing site hosted on a server not belonging to the targeted bank, typically alerts the banks to phishy behavior. Because the graphics are loaded only once, from the desktop of the targeted victim, the banks can’t put a stop to it before it’s too late.
These pages also pull graphics from the banks’ Web sites–activity that, when it comes from a phishing site hosted on a server not belonging to the targeted bank, typically alerts the banks to phishy behavior. Because the graphics are loaded only once, from the desktop of the targeted victim, the banks can’t put a stop to it before it’s too late.
The messages are effective not just because of the social engineering aspect, but because they are able to sneak past some defenses like filters. Some spam filters might overlook the email messages because the messages don’t contain a link, and anti-malware blockers might not flag the messages as malicious because the plain-vanilla HTML in the attached file isn’t an executable Trojan horse.
On the other hand, having the source code to the phishing page makes my job that much easier. All I have to do is fill in a form with bogus data, and I’m able to see the destination (as illustrated above) where the form submits the data. Someone thought they were being really clever. Thanks for handing me the keys to the kingdom, dumb phishing guy.
In addition to bank phish email, we also saw over the past weekend a lot of old spam scams. Among these, we saw a new twist on the (now old) IRS/HMRC tax evasion warning messages.
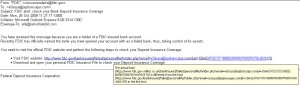
The new messages appear to come from the Federal Deposit Insurance Corporation (FDIC) with a subject line that reads “FDIC alert: check your Bank Deposit Insurance Coverage.” The email reads (in characteristically tortured English) that “Recently FDIC has officially named the bank you have opened your account with as a failed bank, thus, taking control of its assets.”
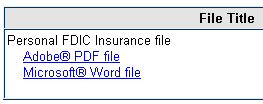
Maybe you never should have opened that account at Bank of Guido, but if BoG is FDIC insured, there’s no need to check your coverage. Certainly there’s no need to “Download and open your personal FDIC Insurance File” as the message suggests. The FDIC doesn’t even have “insurance files” on every depositor in an insured bank. That would be ridiculous. And yet, it helpfully offers you an Adobe PDF or Microsoft Word “version” of your “Personal FDIC Insurance File.” Gee, thanks.
Thus, the victim clicks a link, and thus, ends up on a page where they are asked to download a Trojan. The Trojan, when executed, thus infects the victim’s PC with Trojan-Backdoor-Progdav (aka Zbot), and thus, the victim has a Really Bad Day.
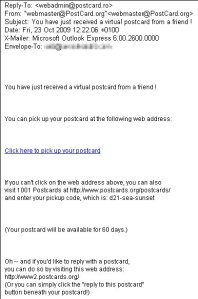
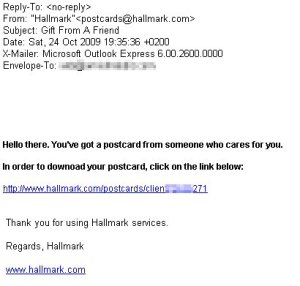
Some of the other scammy spam messages that enjoyed a busy weekend included some “shipping confirmation” spams (with DHL again the targeted shipper), the old “Western Union has some money for you” spoof, and the “you’ve received a postcard/greeting card” Trojan-delivery spam messages.
In this case, we were told that we “got a postcard from someone who cares for” us. Aww, gee whiz. Stuff like that makes my research testbed all warm and fuzzy. The payloads are generic backdoor Trojans that use IRC to communicate. We know how to care for IRC Trojans, too. We care for them with extreme prejudice.