A newly launched underground market service, aims to automate the unethical penetration testing process, by empowering virtually all of its (paying) customers with what they claim is ‘private exploitation techniques’ capable of compromising any Web site.
More details:
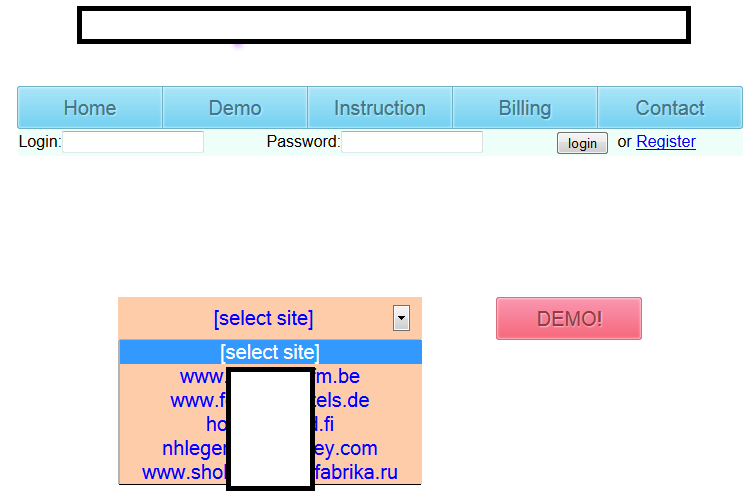
Sample screenshots of the DIY automatic Web site hacking service+colors of the displayed output:
- the service offers a demo of the hacking process for several (vulnerable) Web sites
- the price for scanning a single Web site is $5, and if a scanned Web site can be hacked using the service, the price becomes $50
- the instructions of the service state that – “We don’t touch our (country’s) Web sites, and our law enforcement doesn’t touch us”
- the service doesn’t utilize Google for finding vulnerable Web sites on a mass scale, instead it allows the cybercriminal to manually enter the Web site about to get unethically pen-tested
- even if the service cannot automatically hack into the Web site (based on what the service claims are private techniques for exploitation) the specially displayed output is supposed to increase the probability for a successful compromise
- the service also offers consultation for hacking into any given Web site, with the prices varying between $1000 to $50,000
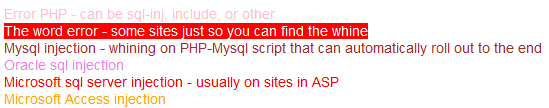
- the service successfully detects Microsoft SQL Server, Oracle, MS Access
The current inability of this boutique service to cause widespread damage by empowering its customers to amass Web site hacking capabilities through search engine’s reconnaissance/predefined list of targets, will inevitably minimize its impact within the cybercrime ecosystem.
The commercial availability of DIY Google Dorks Web site exploitation tools, the existence of stealth Apache modules, and sophisticated exploitation platforms, have greatly contributed to the development of new market segments within the cybercrime ecosystem. And with their effectiveness in terms of scalability and ‘innovation’ throughout the entire cybercriminal ‘assembly line’, they will continue to act as a major driving force, capturing a decent market share of malicious activity online.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.