By Dancho Danchev
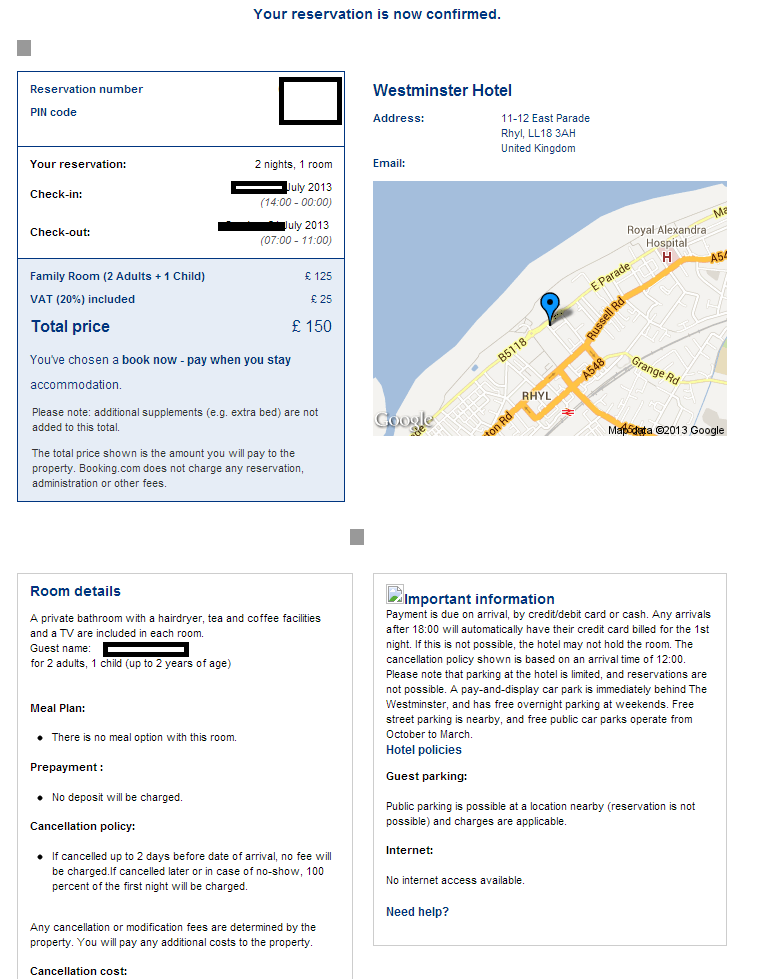
Cybercriminals are currently mass mailing tens of thousands of fake emails impersonating the Westminster Hotel, in an attempt to trick users into thinking that they’ve received a legitimate booking confirmation. In reality through, once the socially engineered users execute the malicious attachments, their PCs automatically join the botnet operated by the cybercriminals behind the campaign.
More details:
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment – MD5: 7eed403cfd09ea301c4e10ba5ed5148a – detected by 6 out of 47 antivirus scanners as Trojan-PSW.Win32.Tepfer.nprd.
The UPX compressed executable creates an Alternate Data Stream (ADS), starts at Windows startup, and creates the following Mutexes:
3161B74B4743E1643757A7220636106970144646
CTF.TimListCache.FMPDefaultS-1-5-21-1547161642-507921405-839522115-1004MUTEX.DefaultS-1-5-21-1547161642-507921405-839522115-1004
It then phones back to the following C&C server:
hxxp://62.76.178.178/fexco/com/index.php
We’ve already seen the same C&C directory structure in the previous profiled ‘Fake ‘Vodafone U.K Images’ themed malware serving spam campaign circulating in the wild‘ campaign.
We’re also aware of the following MD5s that are known to have phoned back to C&C servers with the same directory structure:
MD5: e136d344f16fad04449371bc641072ac
MD5: dd3fae4474960e066d75dea5a076d717
MD5: 9acfbac6cbbdcdb267253da6b2bfd211
MD5: c197bfbe2bd9f5a633403dc4a808f783
MD5: 3f4c9b8fec2d9b14190fc7c67769d09b
MD5: 4e148480749937acef8a7d9bc0b3c8b5
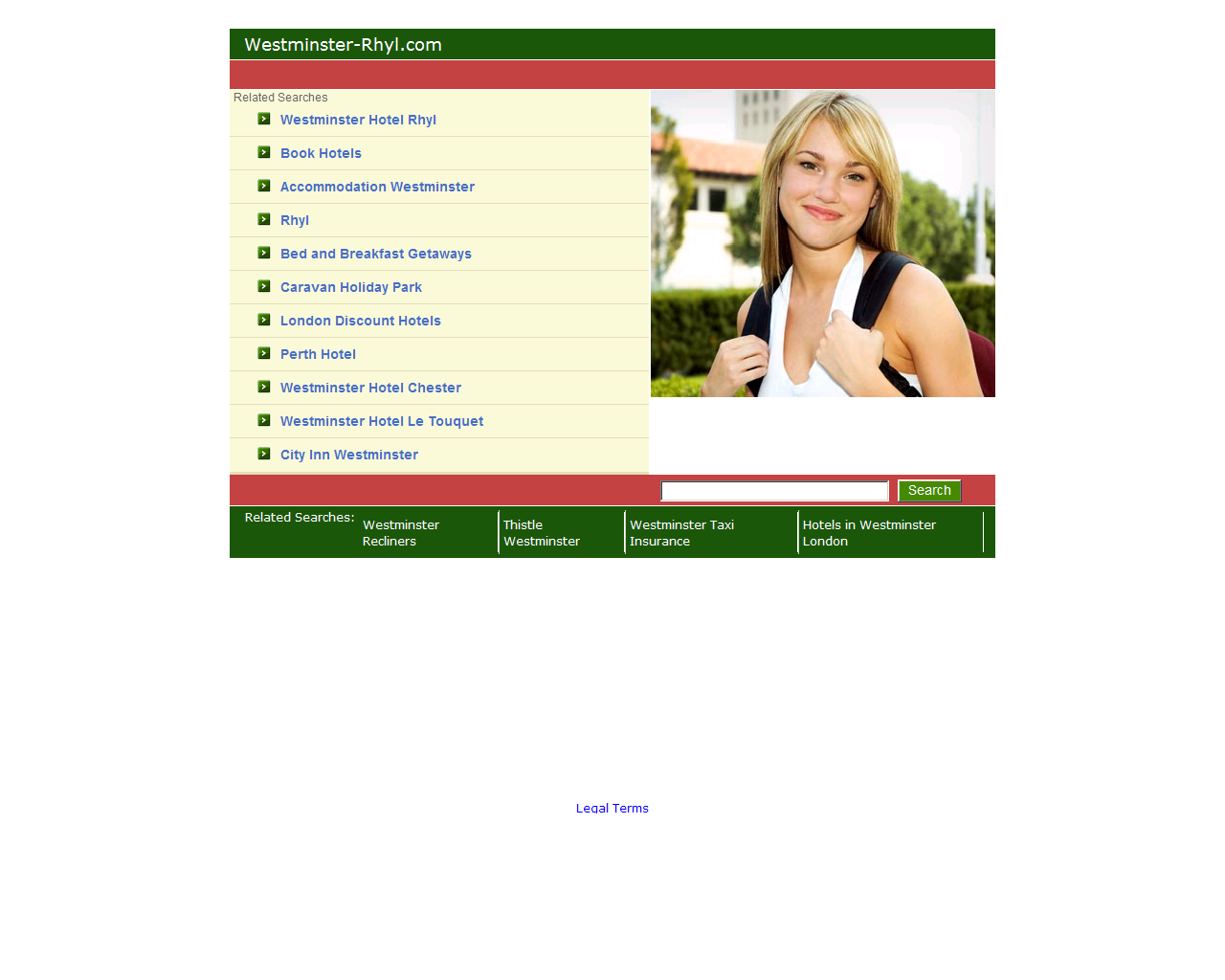
While we were investigating this campaign, we also found out that, apparently, the Westerminster Hotel in Rhyl, Denbighshire, did not renew their primarily domain name (westminster-rhyl.com – 64.74.223.31), allowing opportunistic ‘domainers’ to quickly snatch it. Not surprisingly, we also detected malicious activity with multiple malicious software phoning back to the current hosting IP of the Web site of the Westerminster Hotel in Rhyl, Denbighshire.
Sample MD5s known to have phoned back to the same IP (64.74.223.31):
MD5: 4c44d9999c5062bb20251a7f3a5203b4
MD5: 27f48e921f0fe53a270b9190ed78c40e
MD5: 625c9a1345a087aad55d623afae580c0
MD5: 9e8df7554a735c018ab5867990c9d7ca
MD5: f5af385b41a2dfe1a79aea56fc8dad25
MD5: 9fa3f95de82a9a35300cbf2dd84432e8
MD5: 8f85ce9b0e37aad6c27983b9e5d5c20d
MD5: c145b1758319eaa72afb7d9001f30ed8
MD5: f284db86e53fd34ead97665f57f4de91
MD5: ba8e24446a964ef02e2fc4a857629e0b
MD5: 95dd5fbbf85ced862365acfcc01b9d18
MD5: 7e0228ea687f43f5572c6f771e8d121a
MD5: 8eb2de143ca02a14a30a8b451faabe54
MD5: 10e954d6715f7be0e9d82cc7739b7294
MD5: 6c99fea06f9a40d955634682e237fcf2
MD5: 8a511b36ec769393a8b8866be8a8227b
MD5: 4a659643f5ead3955c2dc99a11ecd98c
MD5: 3fb9b91f4c972a5588dbcd192bfd7b8f
MD5: 461f0338ed27771cd948034868a90fb0
MD5: 3575a0214f81f087c21c784a21e0369e
MD5: 7797ae2b8697930eaed33348647b409b
MD5: 339c342ae864099a731afdbc1b941fb3
MD5: 90f1387a390e2cc443a1df898f863f90
MD5: 946044879ad2058a11f05111a2e6a921
MD5: 8ce6639b9aa6b97e9dbec5cdea9d9c73
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.