By Dancho Danchev
In 2013, the use of basic Quality Assurance (QA) practices has become standard practice for cybercriminals when launching a new campaign. In an attempt to increase the probability of a successful outcome for their campaigns — think malware infection, increased visitor-to-malware infected conversion, improved conversion of blackhat SEO acquired traffic leading to the purchase of counterfeit pharmaceutical items etc. — it has become a common event to observe the bad guys applying QA tactics, before, during, and after a malicious/fraudulent campaign has reached its maturity state, all for the sake of earning as much money as possible, naturally, through fraudulent means.
In this post we’ll profile a recently released desktop based multi-antivirus scanning application. It utilizes the infrastructure of one of the (cybercrime) market leading services used exclusively by cybercriminals who want to ensure that their malicious executables aren’t detected and that their submitted samples aren’t shared between the vendors before actually launching the campaign.
More details:
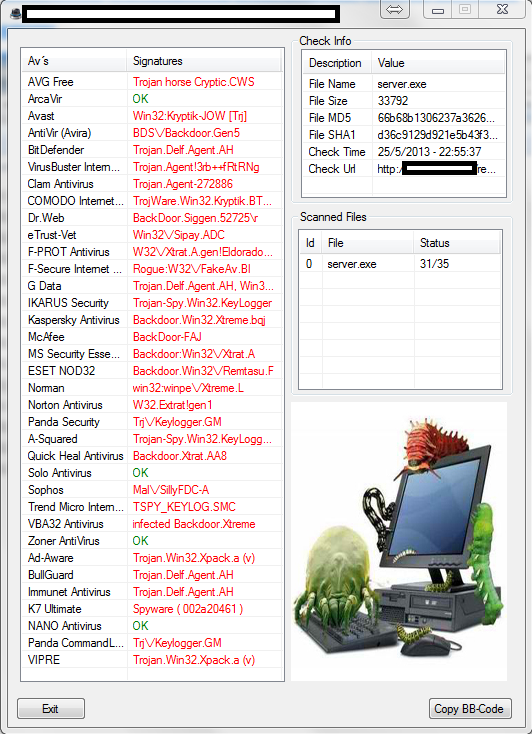
Sample screenshot of the desktop edition of the originally, Web-based, API-supporting cybercrime-friendly service:
Operating on the public Web since 2009, one of the most popular cybercrime-friendly underground alternatives to VirusTotal has been systematically evolving throughout the years. From the periodic introduction of new antivirus scanners to the introduction of anti-blacklist URL checking against the most popular public/commercially available databases, since 2010, its users can also take advantage of its API, and embed it within their campaigns/Web malware exploitation kits. Does the existence and public availability of the tool pose any significant threats?
Despite the fact that the (unofficial) desktop version is aimed to be a convenient way for a cybercriminal not wanting to access the Web interface of the service, it’s directly undermining the efficiency/bulk centered mentality of the API, imposing service limitations to the cybercriminal using it.
The existence of this service, and the community that’s apparently orbiting around it, greatly reminds us of the limitations of signatures-based antivirus scanning in 2013. Thanks to commercially available DIY malware crypting services, commercially available undetected DIY malware generating tools, as well as managed malware/ransomware services taking care of the detection process, cybercriminals are perfectly positioned to capitalize on the users’ false feeling of security and lack of situational awareness on the whole infection process.
To find out more about how Webroot is reinventing the antivirus, consider going through this paper.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.