By Dancho Danchev
Our sensors recently picked up a Web site infection, affecting the Web site of the Ministry of Micro And Medium Enterprises (MSME DI Jaipur). And although the Black Hole Exploit Kit serving URL is currently not accepting any connections, it’s known to have been used in previous client-side exploit serving campaigns.
Let’s profile the campaign, list the malicious URLs, associate them with previously launched malicious campaigns, and provide actual MD5s for historical OSINT preservation/attribution purposes.
More details:
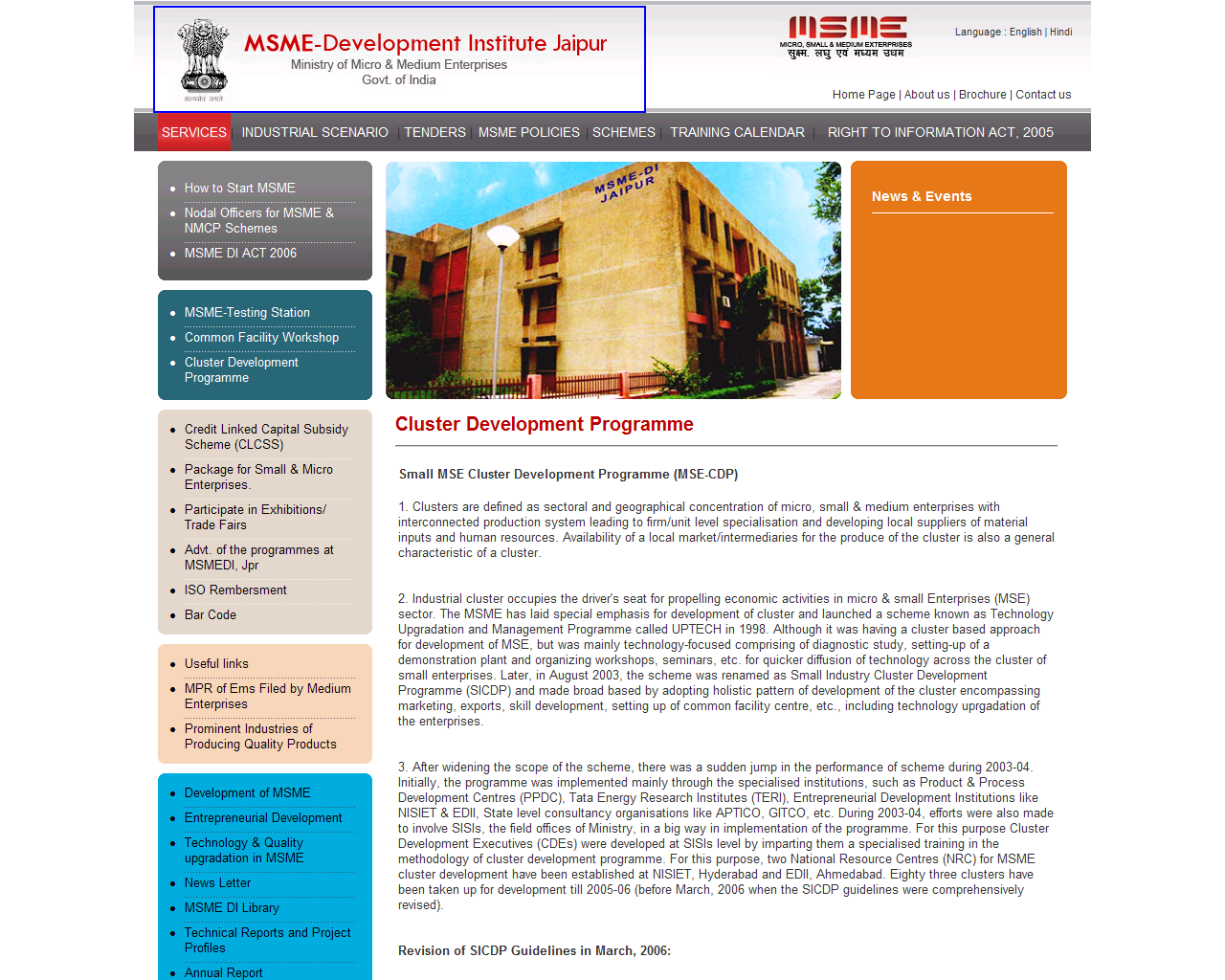
Sample screenshot of the affected Web site:
Sample screenshot of the malicious script detected on the Indian government Web site:
Sample compromised URLs:
hxxp://sisijaipur.gov.in/cluster_developement.html
hxxp://msmedijaipur.gov.in/cluster_developement.html
Detection rate for the malicious script: MD5: 44a8c0b8d281f17b7218a0fe09840ce9 – detected by 24 out of 47 antivirus scanners as Trojan:JS/BlacoleRef.W; Trojan-Downloader.JS.Iframe.czf.
Malicious domain names/redirectors reconnaissance:
888-move-stuff.com – 50.63.202.21 – Email: van2move@yahoo.com
888movestuff.com – 208.109.181.190 – Email: van2move@yahoo.com
jobbelts.com (redirector/C&C) – 98.124.198.1 – Email: aanelli@yahoo.com
More malicious domains are known to have been responding to the same IP in the past (98.124.198.1):
adventure-holiday-specials.com
appraisingla.com
arc-res.com
a-to-z-of-barbados.com
bookmarkingdemonx.com
ceointerns.com
charityairsupport.org
csepros.com
dominateseowithwordpress.com
enum365.com
jobbelts.com
karenbrowntx.com
rankbuilder2.net
seopressors.org
stopchasingmoney.com
thefamily4life.org
ventergy.com
The following MD5s are also known to have phoned back to the same (redirector/C&C) IP (98.124.198.1) in the past:
MD5: f2d01514d0d2794ed78876d01e0e04db
MD5: 799134d350b8842af52fe5d60de2912b
MD5: 8b9f907c1e4e2554f53e31847873fd39
MD5: f7217bb8839e81e912aa0f90da009381
MD5: fc25c21aeb34b8044a50b705a7f3196c
MD5: 4d7b516d5e9fcded471d3d90b8d81ee8
MD5: d185e2e05a9fdea22273c34509f705cc
MD5: 93d796d5a99c36a3e85d308198c1633e
MD5: 25d77181324ccabe860a43178cbdabc9
MD5: f3c1a408991d1677bf18b53ef8dc9694
MD5: e5e893be23ac2e08fc2e7ac66f019b10
MD5: 092382c436b32eba275c07777c40a9a0
MD5: ca64138f14218b983bf26454855578f6
MD5: 88ddb2d8b49bd83ecafe224f94f34fd6
MD5: 858e08cf6941e51a095dcf353efc631c
MD5: 48ea9ba54a567ec83980ed33f0a6f443
MD5: af4ebdb68cfff1a740128d9267722842
MD5: d4d2d0d4786862441437bad647cbbe33
MD5: 5ac3fbf4117f20e6fe044e775fdf093d
MD5: 5ac4ae6eaa0e0c2902493161bbcc19b2
MD5: 42c6545a6d47ebe2e82d5de82acfd1e9
MD5: 221c235bc70586ce4f4def9a147b8735
MD5: 52bad082f4832c5ae5a55a1bcbcd9e85
MD5: 2ceeadcad588907a6e15432919bc4034
MD5: 4b3297a1160535a2c0daf12b18c98b24
MD5: 8a2ae3d73915066ab17602d3030d5210
MD5: 6721e76f1e3d2115bdc9f80b19ea2559
MD5: d610ee9403d278fd5e1f73b4f84c09ef
MD5: 3ab818111067dfa92f0127ffdcc35023
MD5: 76134ec61934a3e6a902321ea3cf1f4e
MD5: 6392e74b4089434e37a8057abd1c3412
MD5: 1b0939a3c6949889beb8cb76b166cbbf
MD5: b34fbe260547ec3b0b8fb459fcf30771
MD5: cd0f1f5f7bebbfc789dac4d5557ff863
MD5: d45390bac7ee591fef142dcd5c52b904
MD5: ffd80b49d09f9c5eaa73cf8f4fa7c32b
MD5: 35880e82794d19468089e80d906ec39a
MD5: 91de2d4993680d0daa3e511b1641a175
MD5: 4655088575b11b204a06acd39f7b5630
MD5: e9e8c72208fcaabcec7562b6e1676af6
MD5: 490c91d8c16c8d6c73734ce11c444593
MD5: ff0a9c71518e2278cb8dad27881465b3
MD5: a0a9617cdd0bf84dd5d07add2deabf40
MD5: 4e6d21171b58826dfb0bd3476482c5ac
MD5: e5c0574f3c9e48fe85f544bf9c39937a
MD5: fb25f19c93fe035391f195a52ae07971
MD5: 77bb37ad859d4c433bbb217e5d6a41f7
MD5: 47810e1cbd0ca2bbeed4c02edeaa9b4c
MD5: fd90feeed1cf8e7c0d65a544cb4a3e35
MD5: f545e564afb8716a7666e094b14b0468
MD5: e751dd91e840c107edf70f29ef691b0a
MD5: 6f78620dbb70ffac24b9527f10e77902
MD5: 17c9528ea10a6ccc8057cb2cd2dbbe29
MD5: 59bae82ba7a09511b99e3675bc03a3f7
MD5: e4a01de23165ea57cf48746eadba3673
MD5: a3922f61be14c531afb12bfc11a0b44b
MD5: b046b9bed7785956fa3e1558e0afd471
MD5: 0140f83cff8d68440b08c1b32315c3a8
MD5: 7d9f5b6361b0699a291d34bd2bbd1ef1
MD5: 2035b5fb2e7ebbabc6d3d45c02a5deba
MD5: 0a7dd5ff56918b12d75f3d8eabf564d6
MD5: aef3b6defe975d62a8dd35a9cee86903
MD5: ce2caa00f0a84dbeef6d14ba21f266b7
MD5: 0e6024ad1bf070e50358a69db2591638
MD5: 6fc253744ee4c906ea918f86fc1f48e3
MD5: 1b38047c2ea9116cb0c1e6d2abce87ea
MD5: 3072ca7490c113770a71b9061618e72c
MD5: 6cbf399be3d49c7b8cc978f7438872fe
MD5: 3e457718647cf0c710828c95ea28a25c
MD5: 57c4e7d1710cba165c3e60f3fdea599e
MD5: feabf100e09c7c7b66f7c372dad9cb8a
MD5: f2cac6034a9083b40664e9214667c753
MD5: 3b16066f9253cc108b0471e8b09503a7
MD5: 34ced03f0c3526c40a7672c05a51dd7b
MD5: be6eff934e37d870fabe2a0e032b35a0
MD5: 76a3a098aeac3cd23c4658bd99b05b22
MD5: 4fee26033634100542d341140211ae62
MD5: a5e501121d9c77b1c5e3e8a3fdb90059
MD5: 4bf55b2dfc381304e4a5072e5b6a40b6
MD5: d8d3d43384ef8176c7b9be23c805fde9
MD5: 3a76404ad87c2650b1a5637fea02d50e
MD5: 3874e390bd8722988b4e531fc08f8e75
MD5: 8669106885799a18b5cf0b7f363f9f80
MD5: 3aafd629a67984b68fde3ee1933e905b
MD5: d27d37c01df70f2f045503ebfc6414a0
MD5: a4bb145882cda7dd6239394ece66f484
MD5: 36d9c2510d0181c52012c0f74f3a83be
MD5: e90fd0e9a481611c9f2c5441d724c77f
MD5: 1b1da73836cb7a92dc859e3c8a9dc9a9
MD5: 412d768b9a8825b59e0e156e12d97178
MD5: d038be577445db7a903c7ab5c6b30940
MD5: 2b91cfd5c51d0fa3ef87a15fa1b9df82
MD5: 3156619047726ed0aa1847382f533c61
The Black Hole Exploit Kit redirecting URL that’s currently embedded at the Indian government Web site is currently not accepting any connections. However, we know that on 2012-07-03 08:04:36, it was responding, and was indeed served malicious content.
Sample redirection chain:
hxxp://wwww.888-move-stuff.com/main.php?page=3081100e9fdaf127 -> hxxp://wwww.888movestuff.com/data/ap2.php -> hxxp://wwww.888movestuff.com/w.php?f=97d19&e=1
Upon successful client-side exploitation back then, it dropped MD5: 770cc2e2a184eaad0d79716f0baf9e48 – detected by 40 out of 46 antivirus scanners as Trojan-Ransom.Win32.Birele.vjr; PWS:Win32/Fareit.gen!C.
Once executed, the sample created the following Registry Key on the affected hosts:
HKEY_CURRENT_USERSoftwareWinRAR
As well as the following Registry Value:
[HKEY_CURRENT_USERSoftwareWinRAR] -> HWID = 7B 42 37 36 33 44 31 31 31 2D 41 45 45 37 2D 34 30 46 36 2D 41 38 41 31 2D 35 36 33 44 46 41 32 37 41 32 34 37 7D
It then downloaded additional malware from:
hxxp://euxtoncorinthiansfc.co.uk/pd.exe
hxxp://euxtoncorinthiansfc.co.uk/1689.exe
MD5: 34AC3D1AB72E67DF7D60B3BD11604B02
MD5: 76B2A3832CE39F81887FC3375AF60FC5
With the samples back then, phoning back to vnclimitedrun.in:443 (199.59.166.86). In 2012, the same IP was also seen in a malvertising campaign.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.