By Dancho Danchev
Just as we anticipated in our previous analysis of a commercially available Bitcoin miner, cybercriminals continue “innovating” on this front by releasing more advanced and customizable invisible Bitcoin miners for fellow cybercriminals to take advantage of.
In this post, we’ll profile yet another invisible Bitcoin miner, once again available for purchase on the international cybercrime-friendly marketplace, emphasize on its key differentiation features, as well as provide MD5s of known miner variants.
More details:
Sample screenshot of the advertisement for the invisible Bitcoin miner:
Second screenshot of the advertisement for the invisible Bitcoin miner:
Sample screenshot of the DIY builder:
Some of the features include auto-starting capabilities, polymorphism, utilization of 15 pre-defined Bitcoin pools, the ability to kill competing Bitcoin miners, complete pseudo-randomization of multiple variables, as well as support for Socks proxy servers, allowing the cybercriminals behind it to add additional layers of anonymity to their campaigns.
The price for the builder, allowing a potential customer to generate unlimited number of builds, is $19.99, with the seller accepting Liberty Reserve, PayPal, and ironically, Bitcoin.
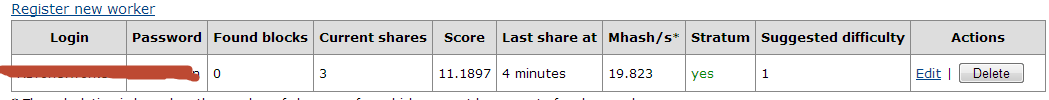
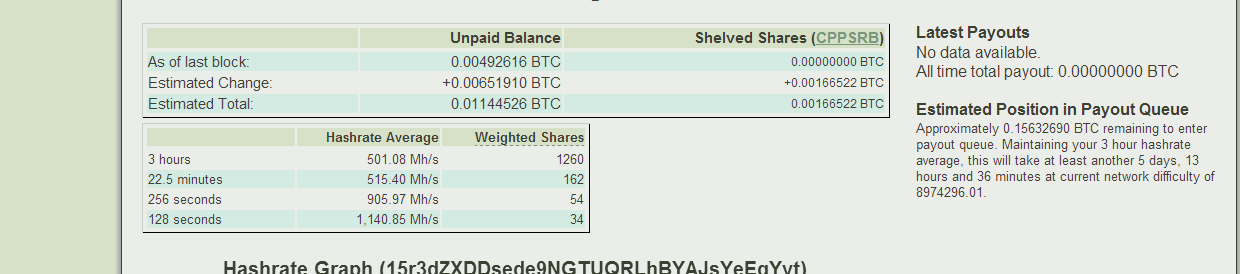
Sample screenshots provided by happy customers of the Bitcoin miner, proving that it works:
MD5s for known samples of this invisible Bitcoin miner:
MD5: b1d53fd86e56b3d6601edfed996f45f8
MD5: 3475dabb9c79a0059e2468332a1d0382
MD5: 432a139b85a1c68b54a8d89fdb79d79c
MD5: a9aa5523e9d2a0be7059891804e13667
Due to its commercial availability on the international cybercrime-friendly marketplace, we expect that this invisible Bitcoin miner will continue gaining marker share which in combination with its distinct set of features, in particular the Bitcoin miner killing feature, will inevitably result in systematic abuse on behalf of its customers.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.
















I am a webroot partner here in San Diego and can help you get subscriptions to any of the Webroot line of Cloud-based security products. Contracts and minimum requirements for annual subscriptions do apply, but you can inquire for a quote. Contact me wlolli at techassistinc dot com for more information. I am a Litecoin miner myself and I have BFL SC units on pre-order– just like many of you. Believe me– you will need cloud based proxy protection for your rigs.