By Dancho Danchev
With more Web-based DIY malware crypters continuing to pop up online, both novice and experienced cybercriminals can easily obfuscate any malicious sample into an undetected — through signatures based scanning not behavioral detection — piece of malware, successfully bypassing perimeter based defenses currently in place.
In this post I’ll profile a recently launched service, empowering virtually everyone using it, with the capability to generate undetected malware. I’ll emphasize on its key differentiation factors and provide sample MD5s known to have been crypted using the service.
More details:
Sample screenshot of the DIY Web-based malware crypting service:
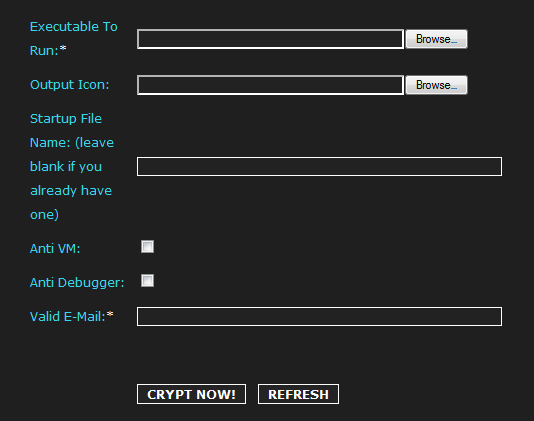
Second screenshot of the DIY Web-based malware crypting service:
Among the key features of this Web-based malware crypting service are the auto scanning of crypted files to showcase to the customer that the file is indeed not detected by the majority of antivirus solutions, support for x32 and x64 files as well as DLL’s, support for all versions of Windows from XP to Windows 8, and the ubiquitous support for anti VMware/anti debugging.
The price? $20, with the service vendor claiming that the file will remain undetected for more than 7 days. Now, how is he able to calculate that remains unclear, as once his customers start spreading the undetected samples, they’ll eventually end up hitting a security vendor’s sensor network, so it’s all up to the customer’s sensor evasion tactics, and not necessarily a service feature.
It’s also worth emphasizing on the fact that in its current form, the service doesn’t have the potential to disrupt the cybercrime ecosystem in an “innovative” way, largely thanks to the lack of API (Application programming interface) support, something we’ve seen implemented on competing services.
We’re currently aware of the following MD5s crypted using the service:
MD5: 8b9dbeb474375f703cb394c4b661122f
MD5: 7251862e224474899a2e60737cc745ef
MD5: de9ebb0bb5ee713e4815c35c64b14691
MD5: adf4df9e1383a99fe647eaa4b81ded13
MD5: 647627f810630ccdc7f30ddeca688d19
MD5: f1caa0212f85e8850b3a11234a2af1be
MD5: 5a2d1771acf1332c2b9ff93312ccd8b9
MD5: 2893f78fdf8245628473517317448acc
MD5: 4eb21fda1f060d228d54a7ef847db7c2
MD5: 625a17feba65dd924366a4b287551df1
MD5: f8470bb0d38a42e1311d7695bd5c6fb9
MD5: 9e0096694f0f5952ed0d2030dab23fbb
MD5: 8cd35dd0dc28d4832c9bdf84c6082acf
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.