By Dancho Danchev
On the majority of occasions, Cybercrime-as-a-Service vendors will sell access to malware-infected hosts to virtually anyone who pays for them, without bothering to know what happens once the transaction takes place.
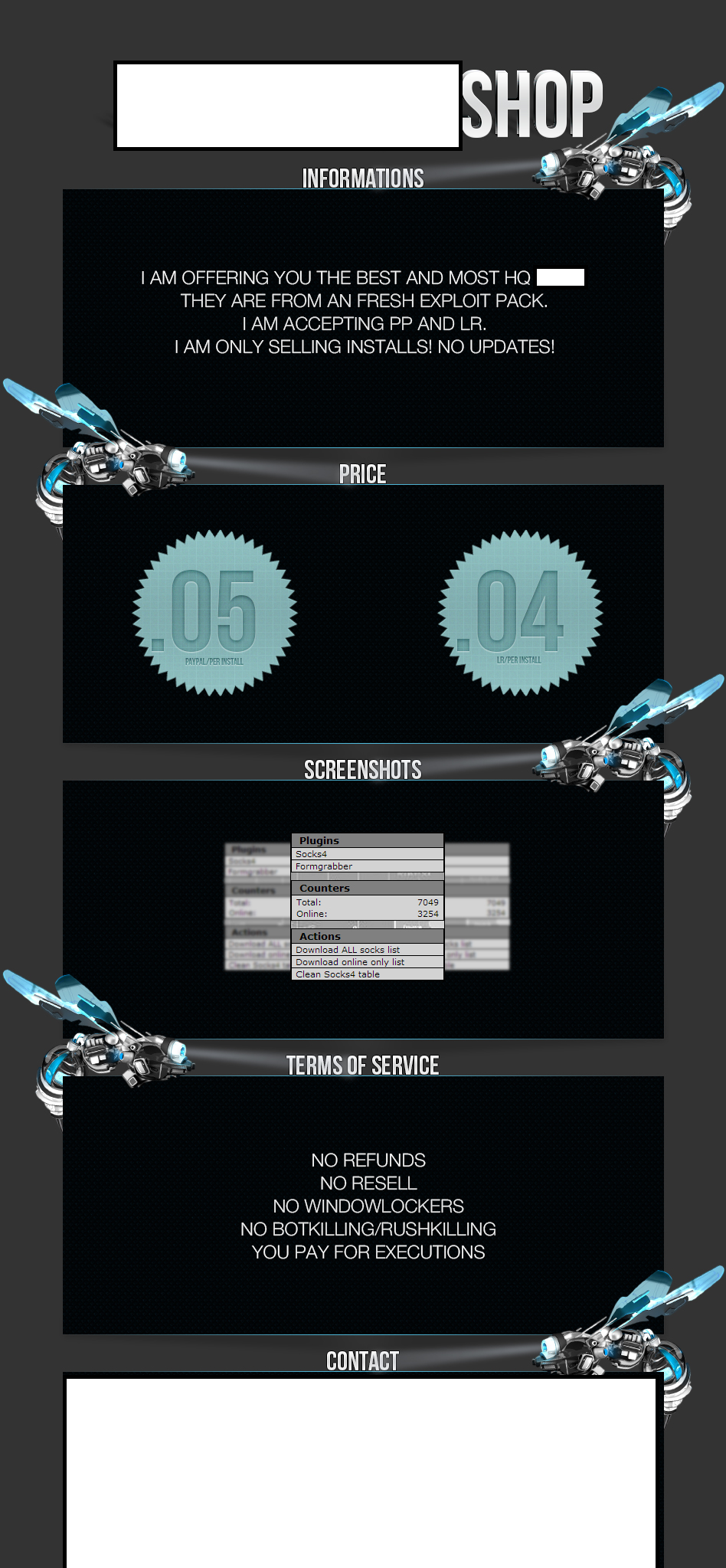
A newly launched E-shop for malware-infected hosts, however, has introduced a novel approach for calculating the going rate for the hacked PCs. Basically, they’re selling actual malicious binary “executions” on the hosts that the vendor is managing, instead of just selling access to them.
A diversified international underground market proposition? Check. A novel approach to monetize malware-infected hosts? Not at all. Let’s profile the actual market proposition, and discuss in-depth why its model is flawed by design.
More details:
Sample advertisement of the E-shop offering access to malware-infected hosts:
Taking advantage of a Web malware exploitation kit, the proposition’s author has featured a sample screenshot showing what we believe is just a sampled snapshot of the malicious activity that he’s responsible for. The TOS (Terms of Service) also explicitly forbids the potential monetization of the hosts through ransomware, as well as the removal of competing malware on the affected hosts. It’s worth emphasizing on the fact that the E-shop owner seems to be undermining his own efficiency model, as in order for him to enforce the TOS, he’d have to ‘verify” each and every malware sample supplied to him for ‘execution’.
Moreover, by forbidding the use of competing bot ‘killers’, he reserves his right to continue controlling the malware-infected host, either ‘milking’ it as a cash cow, or using it as a tool for occupying a related market segment within the cybercrime ecosystem, largely thanks to the fact that he has full control over the user’s PC. This (isolated) practice can be best described by an article published in 1968 on the Tragedy of the Commons, in this particular case, a situation where two cybercriminals will have access to a predefined pool of money to steal from — the second having actually paid for his access in this case — resulting in un-materialized revenue streams that could be directed in just one direction.
Furthermore, a potential cybercriminal and a customer of the service, would never pay for, let’s say, three executions of three separate binaries on the same host. He’ll basically purchase one execution, and take advantage of the matryoshka malware concept, ultimately delivering his payload in a cost-effective way, while using this particular service. Now that’s of course unless the vendor stars verifying that as well, for a second time undermining the logic behind the proposition and the TOS.
We’ll continue monitoring the development of this service, and post updates as soon as new pricing schemes get introduced.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.