Need a compelling reason to perform search engine reconnaissance on your website, for the purpose of securing it against eventual compromise? We’re about to give you a good one.
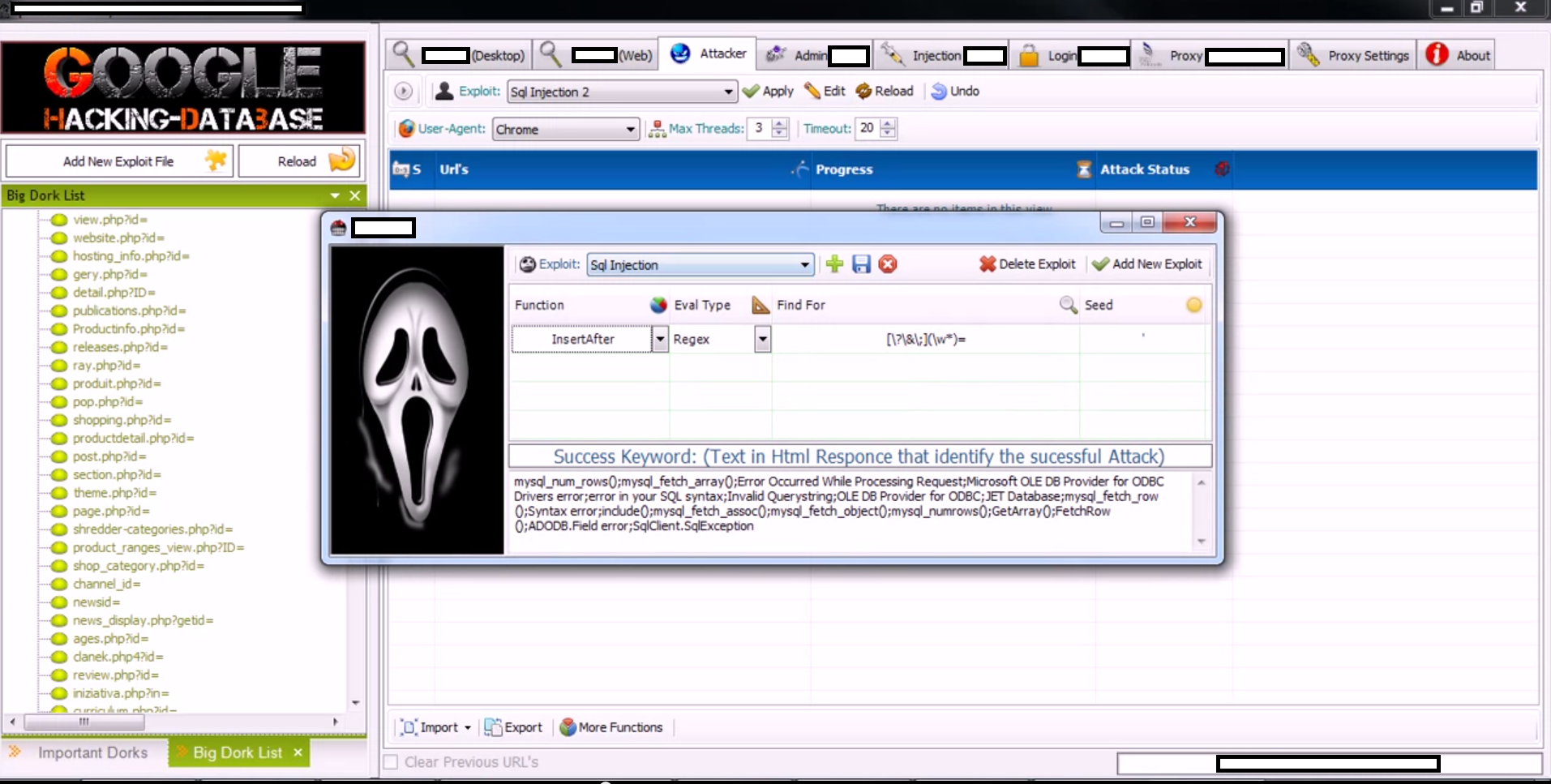
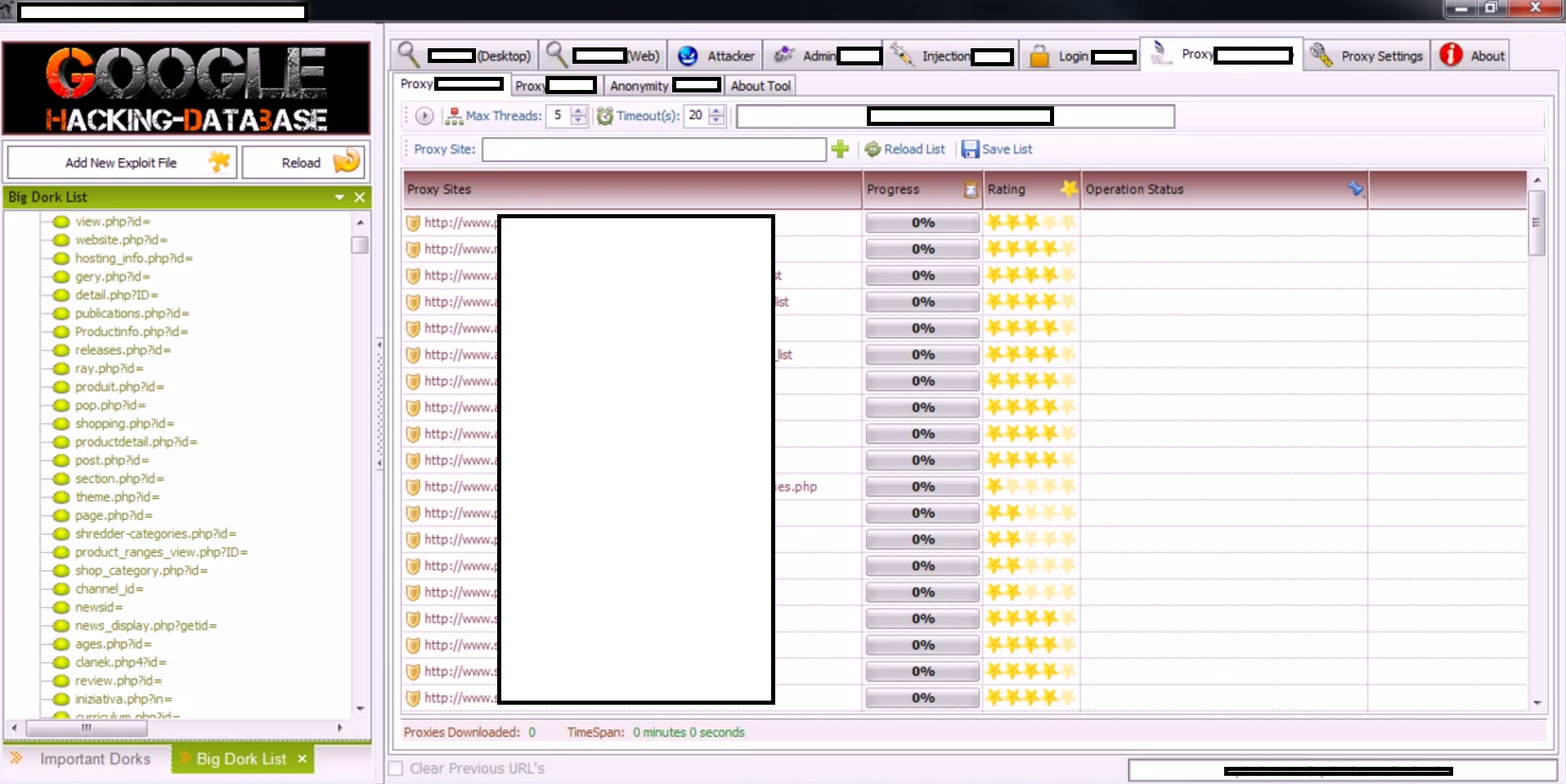
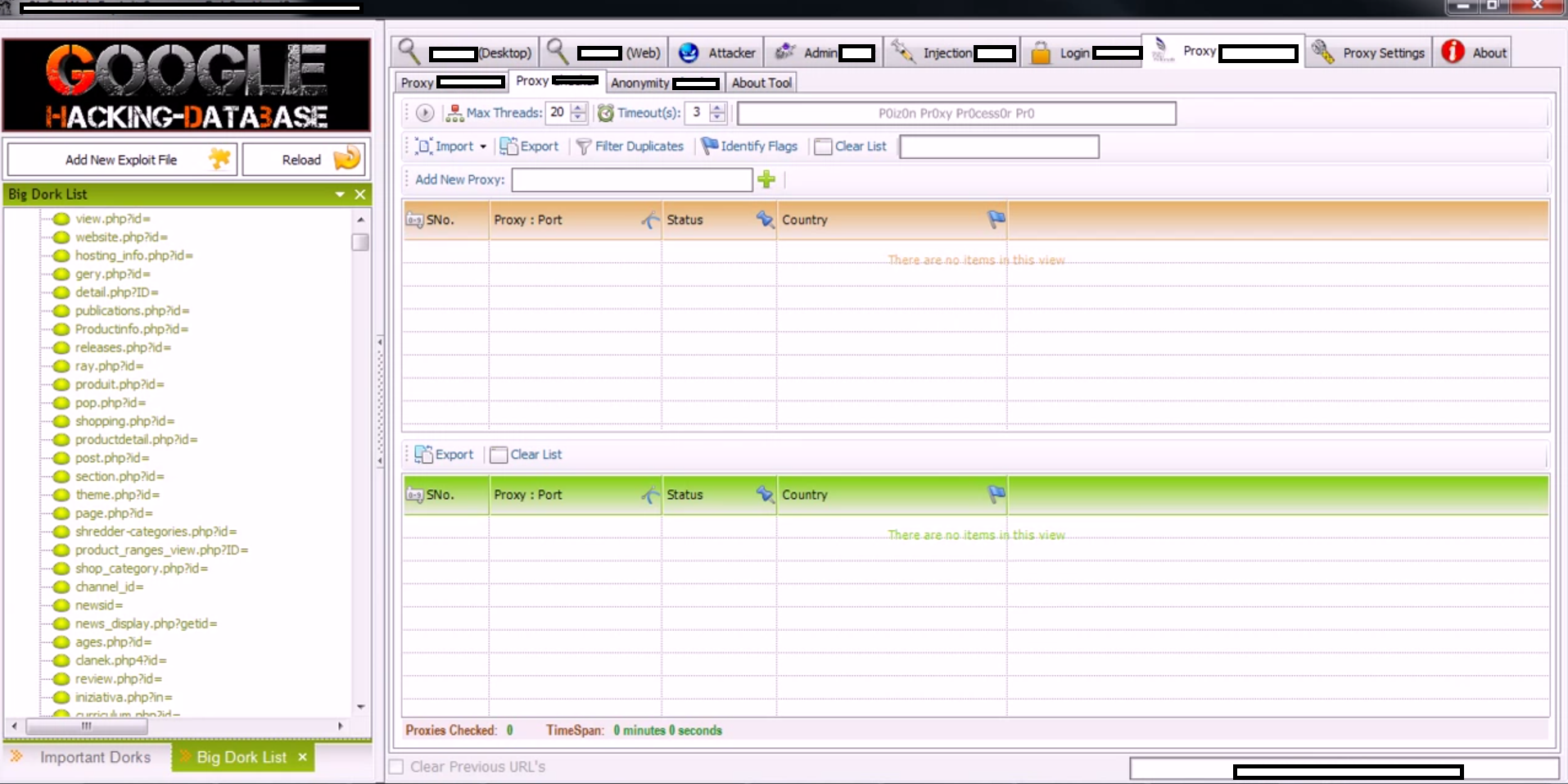
A new version of a well known mass website hacking tool has been recently released, empowering virtually anyone who buys it with the capability to efficiently build “hit lists” of remotely exploitable websites for the purpose of abusing them in a malicious or fraudulent fashion. Relying on Google Dorks for performing search engine reconnaissance, the tool has built-in SQL injecting options, the ability to add custom exploits, a proxy aggregation function so that no CAPTCHA challenge is ever displayed to the attacker, and other related features currently under development.
More details:
Sample screenshots of the DIY mass Web site hacking tool in action:
The tool works both on the desktop as a stand alone application, but can also be integrated within popular browsers in an attempt to fool the search engines into thinking that it is legitimate traffic. It can also automatically detect remotely exploitable websites and exploit them entirely based on the preferences set by the malicious attacker using it.
Its licensing comes in a hardware-based ID form. One license goes for $10 in Liberty Reserve currency, or $11 in Western Union transfer. The unlimited license doesn’t have a hardware-based ID restriction, and goes for $20 in Liberty Reserve, or $20 in Western Union transfer.
Efficiently abusing hundreds of thousands of websites through search engines reconnaissance is nothing new. In fact, it’s been an every day reality since the day market leading search engines started offering advanced search operators to be used. There are several ways through which a cybercriminal can efficiently exploit hundreds of thousands of legitimate Web sites:
- Search engine reconnaissance through DIY SQL/RFI (Remote File Inclusion) tools, or botnets – DIY tools and botnets performing these actions have been available on the underground marketplace for years, empowering novice cybercriminals with the capabilities to exploit insecurely configured websites, blogging platforms, domain portfolio managing tools, Web forums, as well as CMSs (content management systems).
- Use of data mined or purchased stolen accounting data – We’ve seen it in the past, and we continue seeing it in the present. Cybercriminals continue data mining malware infected hosts, looking for login credentials to be automatically abused with malicious scripts and actual executables getting hosted on legitimate websites in an attempt to trick a security solution’s IP reputation process.
- Active exploitation of server farms – A cybercriminal’s mentality is fairly simple as it has to do with efficiency. The higher the page rank of the infected legitimate website, the better, as the campaign will attract a lot of traffic. However, the high page rank also increases the probability of a successful detection by the security community. What would a cybercriminal do in this case? They’ll take advantage of the ‘Long Tail‘ concept, infecting as many low profile websites as possible. This is theoretically capable of achieving the same traffic volumes as if they were to infect a high page rank-ed website. One of the most recent tactics we’ve seen has to do with the practice of infecting all the domains parked at a specific (compromised) server, through commercially available Apache backdoors.
We’ll continue monitoring the development of this tool, and post updates as soon as new developments emerge, in particular, the introduction of features.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.

















Reblogged this on Whitehat News.
Does this version have support for google search appliances?