By Dancho Danchev
Over the past year, we observed an increase in publicly available managed TDoS (Telephony Denial of Service) services. We attribute this increase to the achieved ‘malicious economies of scale’ on behalf of the cybercriminals operating them, as well as the overall availability of proprietary/public DIY phone ring/SMS-based TDoS tools.
What are cybercriminals up to in terms of TDoS attack tools? Let’s take a peek inside a recently released DIY SIP-based (Session Initiation Protocol) flood tool, which also has the capacity to validate any given set of phone numbers.
More details:
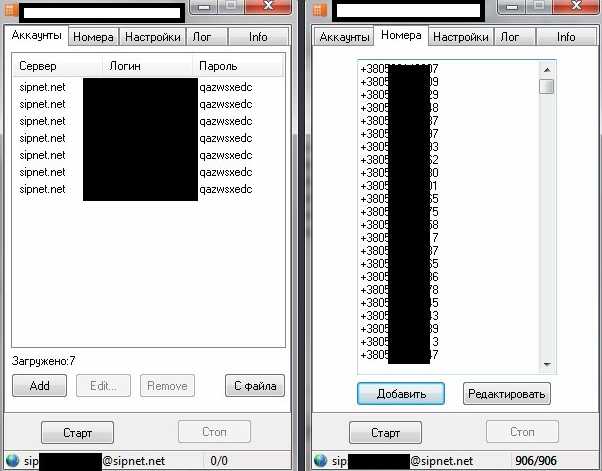
Sample screenshot of the DIY SIP-based TDoS tool/number validity checker:
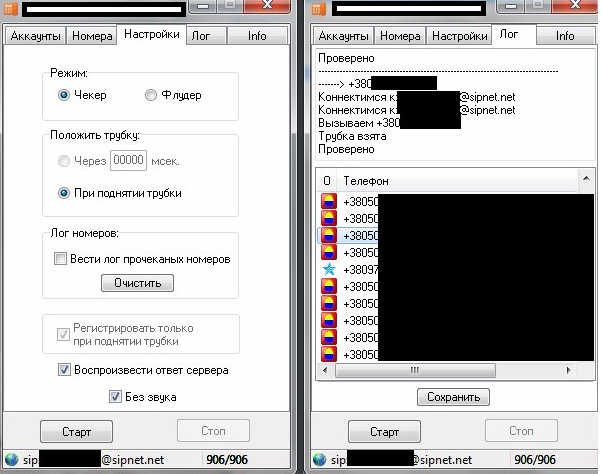
Second screenshot of the DIY SIP-based TDoS tool/number validity checker:
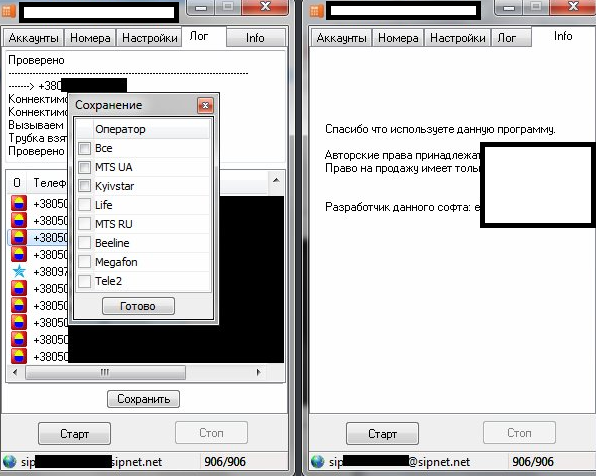
Third screenshot of the DIY SIP-based TDoS tool/number validity checker:
The tool can flood any given number based on the preferences of its users, can work with multiple SIP accounts, has built-in ‘auto-correct’ feature for the list of mobile/phone numbers, as well as logging capabilities. The example offered by the tool’s author, appears to be using a service called SIPNET.
The price varies between $35-$60 depending on the features you’d like to purchase it with. However, in its current forum, the tool fails to delivery the necessary features to cause a widespread adoption across the cybercrime ecosystem, vendors of TDoS in particular.
Since the tool’s developer is publicly acknowledging that he’s working on a Pro version, we’ll make sure to keep an eye on the next version, and it’s potential among the cybercriminals using it.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Crear un facebook http://crearun.net/