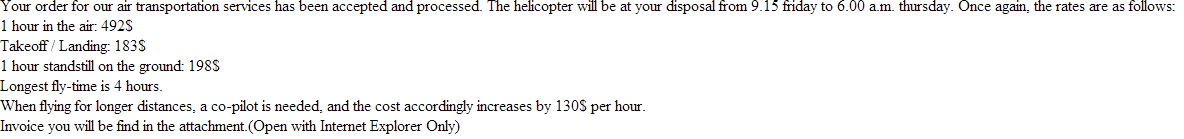Cybercriminals are currently mass mailing tens of thousands of emails, in an attempt to trick users into thinking that the order for their “air transportation services has been accepted and processed”. In reality though, once users execute the malicious attachments, their PCs will automatically become part of the botnet managed by the malicious actors.
More details:
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment: MD5: 97c9c3b4d50171a07305f91c1885ef9f – detected by 24 out of 43 antivirus scanners as Worm:Win32/Cridex.E
Once executed, the sample creates the following processess on the affected hosts:
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp1.tmp.bat””
C:Documents and Settings<USER>Application DataKB00927107.exe
C:DOCUME~1<USER>~1LOCALS~1Tempexp2.tmp.exe
C:DOCUME~1<USER>~1LOCALS~1Tempexp4.tmp.exe
C:DOCUME~1<USER>~1LOCALS~1Tempexp6.tmp.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp3.tmp.bat””
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp5.tmp.bat””
The following Mutexes:
LocalXMM00000340
LocalXMI00000340
LocalXMM00000530
LocalXMI00000530
LocalXMM00000630
LocalXMI00000630
LocalXMQ6C66A66E
LocalXMS6C66A66E
LocalXMR6C66A66E
LocalXMM000002BC
LocalXMI000002BC
LocalXMM000000A8
LocalXMI000000A8
LocalXMM000004A0
LocalXMI000004A0
LocalXMM000009A4
LocalXMI000009A4
LocalXMM00000A48
LocalXMI00000A48
LocalXMM00000EDC
LocalXMI00000EDC
The following Registry Keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCFBDC89D4
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTS25BC2D7B
Set the following Registry Values:
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> KB00121600.exe = “”%AppData%KB00121600.exe””
It then phones back to the following C&C servers:
37.59.36.93:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
94.23.6.95:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
64.186.148.92:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
213.214.74.5:8080/AJtw/UCyqrDAA/Ud+asDAA/
91.121.167.124/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
91.121.30.185/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
We’ve already seen one of the C&C IPs (213.214.74.5) in the following previously profiled malicious campaigns:
- ‘Your Kindle e-book Amazon receipt’ themed emails lead to Black Hole Exploit Kit
- Cybercriminals resume spamvertising ‘Re: Fwd: Wire Transfer’ themed emails, serve client-side exploits and malware
- Spamvertised BBB ‘Your Accreditation Terminated” themed emails lead to Black Hole Exploit Kit
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.