How easy is it to create an undetected piece of malware these days? Too easy to be true!
With more DIY malware botnets and DIY malware generating tools continuing to leak at public cybercrime-friendly forums, today’s novice cybercriminals have access to sophisticated point’n’click malware generating tools that were once only available in the arsenal of the experienced cybercriminal.
In this post, I’ll profile a recently leaked DIY malware generating tool, discuss its core features, and emphasize on its relevance in the context of the big picture when it comes to ongoing waves of malicious activity we’ve been monitoring over the years.
More details:
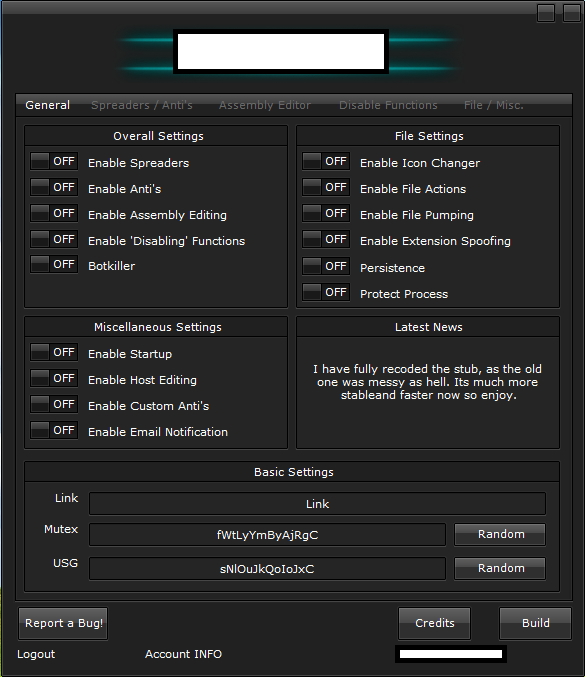
Sample screenshot of the leaked DIY malware generating tool:
The malware generating tool allows potential cybercriminals to tailor their newly generated malware to their specific needs. If they want it to start spreading, they can just turn on the spreading option. If they want it to use targeted attacks, they can choose LAN spreading. They can also enable the option to prevent various antivirus solutions from successfully detecting it, as the malware will detect their presence on the affected hosts, and will either block it, or kill the running processes for the applications of these vendors.
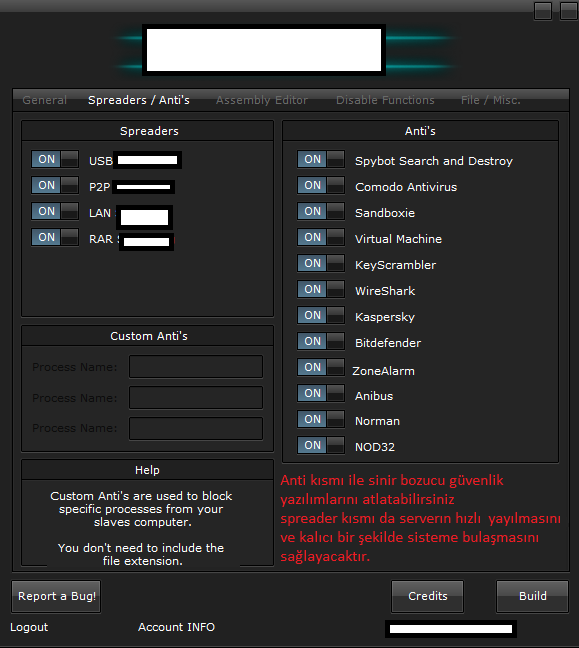
Second screenshot of the leaked DIY malware generating tool:
The DIY tool currently can spread over USB, P2P, LAN, and through RAR files. It is also targeting the following anti-malware tools:
- Spybot Search and Destroy
- Comodo Antivirus
- Sandboxie
- Virtual Machine
- KeyScrambler
- WireShark
- Kaspersky
- Bitdefender
- ZoneAlarm
- Anubis
- Norman
- NOD32
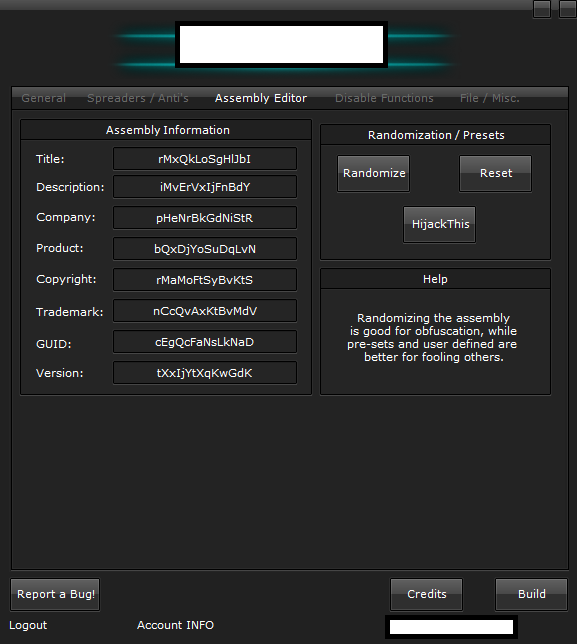
Third screenshot of the leaked DIY malware generating tool:
The tool also allows complete randomization of key components of the malware, so that every time a new piece of malware is generated, it will use different code obfuscation pre-sets.
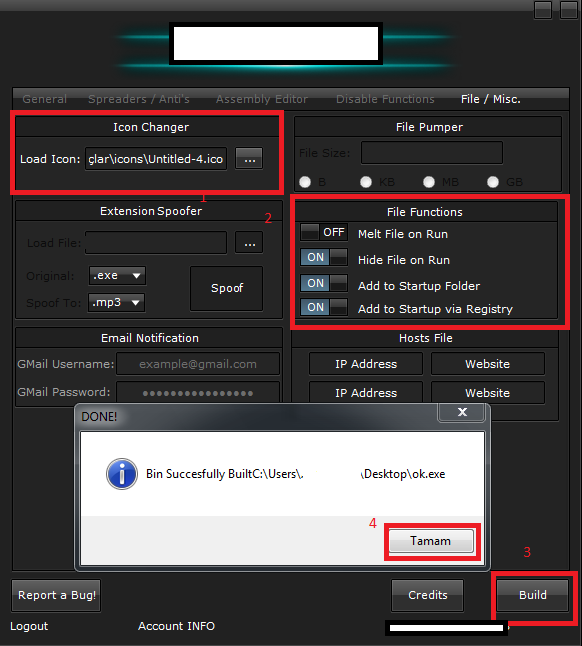
Fourth screenshot of the leaked DIY malware generating tool:
How important is the public leak of this tool in the context of the big picture?
One of the most common myths about today’s modern malware is that it’s being coded from scratch. The complete randomization in combination with managed crypting (source code, iFrame, JavaScript etc.) and server-side polymorphism results in massive exploitation campaigns that continue relying on outdated and already patched client-side vulnerabilities as infection vectors.
Don’t misunderstand me, coding malware for hire has been available as a service for years. However, much of today’s modern malware is being generated, rather than coded from scratch. Stuxnet, Duqu, Flame, Red October are all great example of cyber espionage campaigns where the attackers actually bothered to invest time and resources into coding the malware, utilizing novel infection vectors and zero day vulnerabilities.
These massively covered cyber sabotage/cyber espionage campaigns resulted in a myopia where people think targeted attacks are all about malware coded from scratch. That’s not the case on a large scale, as on numerous occasions in the past, factual evidence has been presented, indicating that the attackers relied on publicly obtainable RATs (Remote Access Tools/Trojans) that they basically obfuscated to fool antivirus scanners.
Bottom line – in 2013 you don’t need to know Assembly to generate undetected pieces of malware. You don’t need to utilize zero day vulnerabilities to infect tens of thousands of people on a daily basis. And in cases where you seek malicious innovation, coding malware for hire services are there to “take care”.
We expect that the entry barriers into the world of cybercrime will continue to get lower throughout 2013, contributing to today’s mature life cycle of the entire cybercrime ecosystem, and will continue posting updates providing factual evidence for this trend.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.