Throughout 2012, we intercepted two malicious campaigns impersonating Verizon Wireless in an attempt to trick its customers into clicking on links pointing to fake eBills.
It appears that cybercriminals are back in the game, with yet another Verizon Wireless themed malicious campaign, enticing users to click on the malicious link found in the email. Once users click on the link, they’re automatically exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
More details:
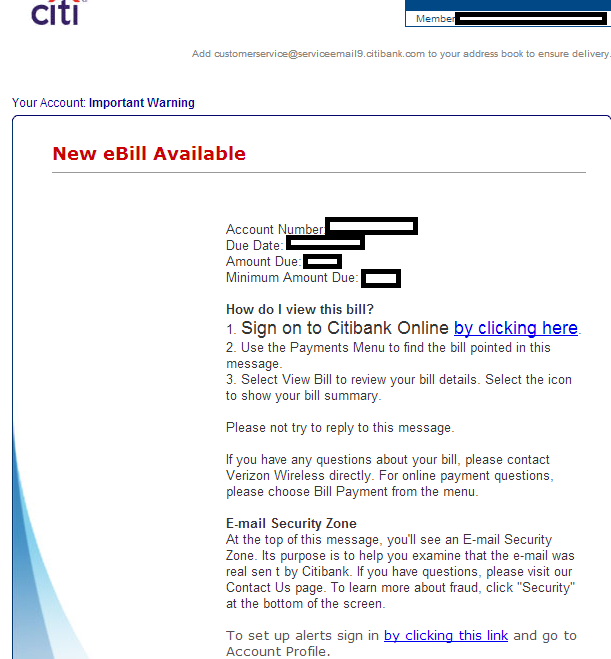
Sample screenshot of the spamvertised email:
Sample email subjects: Fresh eBill is Should Be Complete. From: Verizon Wireless; Your Recent eBill from Verizon Wireless
Sample spamvertised compromised URLs:
hxxp://primarycareconferences.com/wp-content/plugins/zojfvaoluwh/eBill_detalls.html
hxxp://pricesalebestsusu-2.com/wp-admin/eBill_ready.html
hxxp://dullarrows.com/wp-content/plugins/zgnosegetua/eBill_ready.html
hxxp://palm-paper.com/wp-content/plugins/zueijlwqwpe/eBill_ready.html
hxxp://tobash.com/wp-content/plugins/zyefqyehoum/eBill_ready.html
Sample client-side expoits serving URL:
hxxp://proxfied.net/detects/inform_rates.php
Malicious domain name reconnaissance:
proxfied.net – 59.57.247.185 – Email: colorsandforms@aol.com
Name Server: NS1.AMISHSHOPPE.NET – Email: solaradvent@yahoo.com
Name Server: NS2.AMISHSHOPPE.NET – Email: solaradvent@yahoo.com
We’ve already seen the same name servers used in the following previously profiled malicious campaign – “Fake ‘Citi Account Alert’ themed emails lead to Black Hole Exploit Kit“.
Responding to 59.57.247.185 are also the following malicious campaigns part of the campaign’s infrastructure:
sessionid0147239047829578349578239077.pl
latticesoft.net
africanbeat.net
eaglepointecondo.biz
eaglepointecondo.info
eaglepointecondo.org
hfeitu.net
labpr.com
winterskyserf.ru
Upon successful client-side exploitation, the campaign drops MD5: ce367f8e8fa4be25ef80baf5f4aff5c4 – detected by 26 out of 45 antivirus scanners as Worm:Win32/Cridex.E.
Although the cybercriminals didn’t bother coming up with a visually appealing email template impersonating Verizon Wireless like we’ve seen in the previously profiled Verizon Wireless themed campaigns from 2012, they continued to rely on the same malicious infrastructure used in the previously profiled Citi themed malicious campaign, indicating poor QA (Quality Assurance) on their behalf.
We’ll continue monitoring the campaign, and post updates as soon as new development emerge.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.