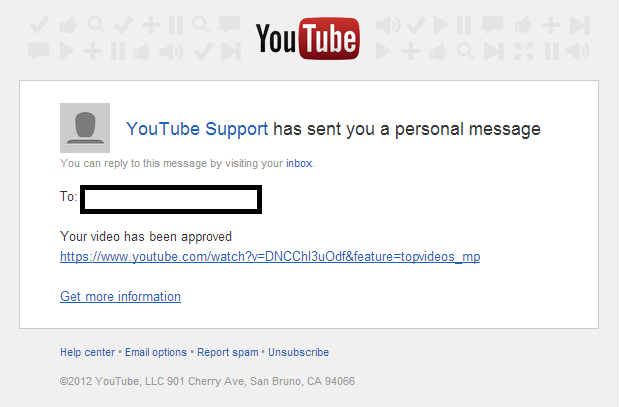
Pharmaceutical scammers are currently spamvertising a YouTube themed email campaign, attempting to socially engineer users into clicking on the links found in the legitimately looking emails.
Upon clicking on the fake YouTube personal message notification, users are redirected to a website reselling popular counterfeit drugs. The cybercriminals behind the campaign then earn revenue through an affiliate network.
More details:
Sample screenshot of the spamvertised email:
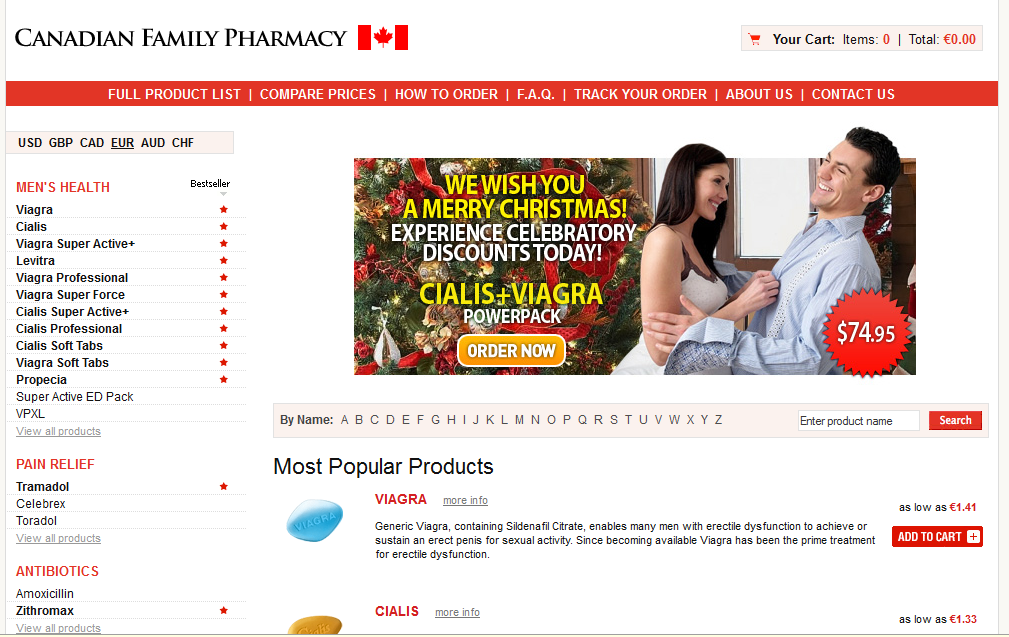
Once users click on the link found in the email, they’re redirected to the following holiday-themed pharmaceutical web site:
Spamvertised URL:
hxxp://roomwithaviewstudios.com/inherits.html
Landing URL:
hxxp://canadapharmcanadian.net – 109.120.138.155
The following fraudulent pharmaceutical sites have also been known to respond to the same IP (109.120.138.155):
tabletlevitripad.com – 95.58.254.74 – Email: hayes@ca4.ru ; Name servers: NS1.GENERICSWELLOCH.COM (93.99.136.42); NS2.XCILE.RU (61.177.184.98)
carewiski.com – Email: pawnbroker@carewiski.com
garciniaherbal.com – Email: sonseeahray@garciniaherbal.com ; Name servers: NS1.OMECT.RU (93.99.136.42); NS2.ZORNY.RU (61.177.184.98)
benghazilispharm.com – 84.22.104.123 – Email: cargreaves@benghazilispharm.com ; Name servers: NS1.BENGHAZILISPHARM.COM (58.42.251.237); NS2.BENGHAZILISPHARM.COM (221.207.50.84)
canadawelcanadian.com – Email: simeao@canadawelcanadian.com ; Name servers: NS1.CLUL.RU (93.99.136.42); NS2.TLAH.RU (221.207.50.84)
centprescription.com – 84.22.104.123 – Email: tremon@centprescription.com ; Name servers: NS1.CENTPRESCRIPTION.COM (93.99.136.42); NS2.CENTPRESCRIPTION.COM (60.28.145.226)
bloodgenerics.com – 84.22.104.123 – Email: milroy@bloodgenerics.com ; Name servers: NS1.BLOODGENERICS.COM (93.99.136.42); NS2.BLOODGENERICS.COM (125.16.213.251)
tabletgenerics.com – 95.58.254.74 – Email: brosilow@tabletgenerics.com ; Name servers: NS1.TABLETGENERICS.COM (125.16.213.251); NS2.TABLETGENERICS.COM (221.207.50.84)
drugenericsmeds.com – 84.22.104.123 – Email: moody@ppmail.ru ; Name servers: NS1.DRUGENERICSMEDS.COM (93.99.136.42); NS2.DRUGENERICSMEDS.COM (125.16.213.251)
drugherbalpills.com – 84.22.104.123 – Email: courtier@drugherbalpills.com ; Name servers: NS1.OHICS.RU (93.99.136.42); NS2.SIEW.RU (60.28.145.226)
Fortunately, during the time of testing the responsiveness of the site, it was desperately trying to remain online, which prevented the socially engineered users from initiating a transaction through it. However, this is sadly an isolated incident. According to recently published research, hundreds of thousands of US-based users click on links found in these types of fraudulent emails, and actually add counterfeit drugs to their shopping carts. The vibrant cybercrime ecosystem is in fact so advanced that, in order to stimulate the affiliate network participants into converting more traffic into actual customers, they even hold annual contests aiming to build a loyal community of network participants.
This isn’t the first time that we’ve intercepted attempts by pharmaceutical scammers to socially engineer potential customers into clicking on the links found in legitimately looking emails. In the past, we’ve found fake Google Pharmacies and emails impersonating YouTube and Twitter, as well as Facebook Inc., in an attempt to add more authenticity and legitimacy to their campaigns.
We expect to see more of these campaigns in 2013, with a logical peak over the next couple of days, so watch what you click on, don’t enter your credit card details on websites found in spam emails, and never bargain with your health.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







I guess that’s a problem for people who read advertising. I don’t open unsolicited links. I also quickly figure out that when I get an email that says your video was approved and I never uploaded one, then it has to be a scam.