With the ever-decreasing entry barriers into the shady world of cybercrime, potential cybercriminals themselves may sometimes become the victims.
A recently intercepted fraudulent email sheds more light into the process of how cybercriminals attempt to scam novice cybercriminals, and also puts the spotlight on the QA (Quality Assurance) practices within the cybercrime ecosystem, each and every time a transaction or a transfer of fraudulently obtained assets is about to occur.
More details:
Sample screenshot of the spamvertised email:
What we’ve got here is a great example of an OPSEC-unaware (Operational Security) fraudster that’s actually exposing himself — instead of forwarding the risk to a third-party — by basically spamvertising tens of thousands of emails offering access to fraudulent obtained credit card data. Although he’s apparently targeting English speaking novice cybercriminals, the email also includes several sentences in Russian in an attempt to make his proposition more appealing to an unaware potential victim that’s about to purchase the non-existent assets.
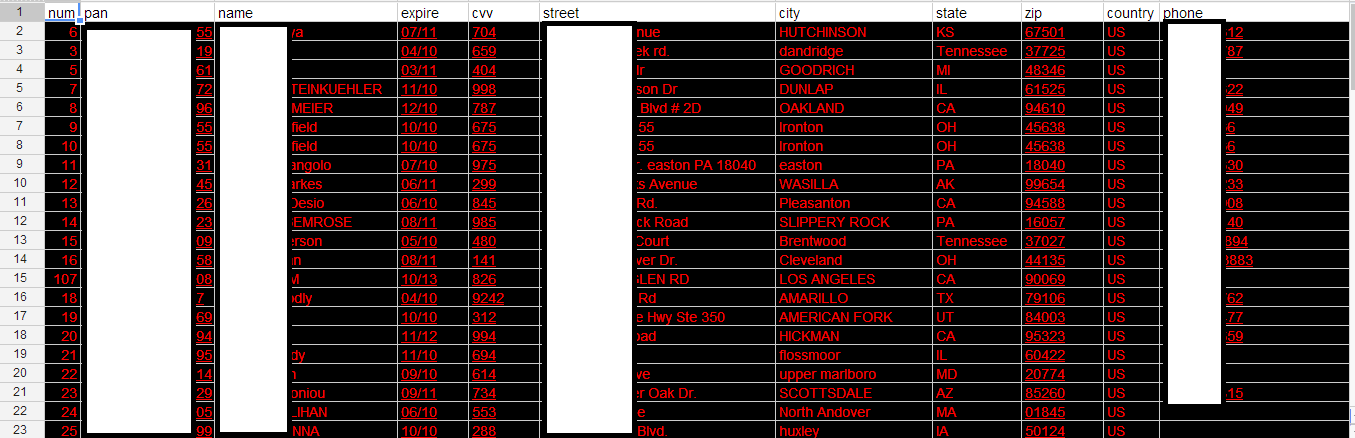
To further improve the authenticity of his email, he even attached a spreadsheet containing automatically generated credit card numbers+affected person’s personal data — such tools have been publicly available for over a decade — as well as another document supposedly containing Track1 and Track2 data.
Sample screenshot of the automatically generated bogus credit cards data found in the spreadsheet:
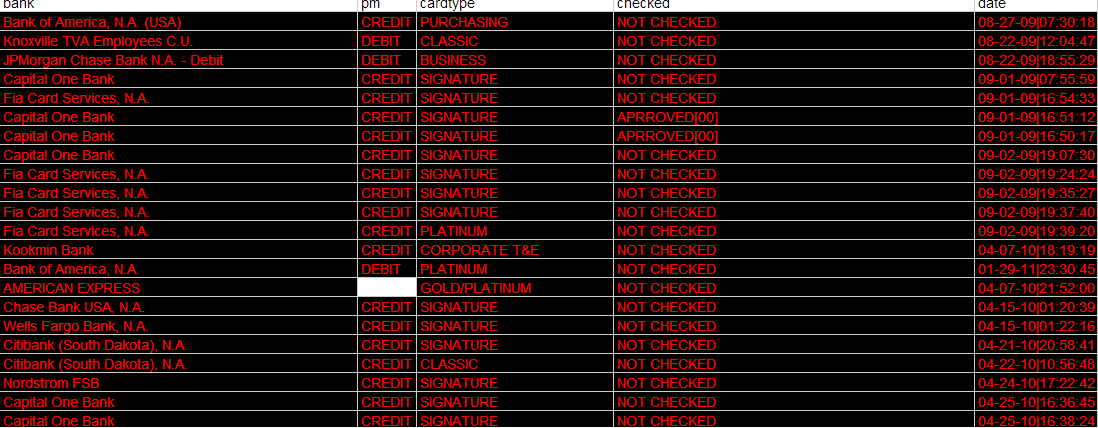
Second screenshot of the bogus data found in the spamvertised spreadsheet:
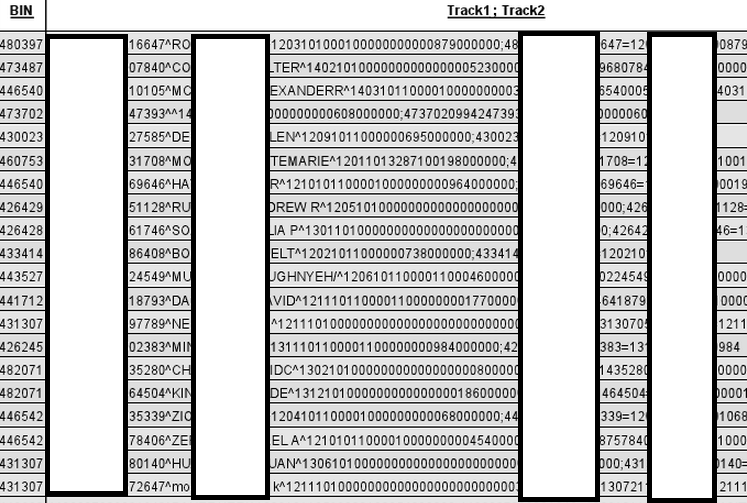
Sample screenshot of the bogus Track1 and Track2 data:
For years, cybercriminals have been exchanging these fraudulently obtained assets through cybercrime-friendly Web communities and E-shops (A peek inside a boutique cybercrime-friendly E-shop – part five; New Russian service sells access to compromised Steam accounts; Recently launched E-shop sells access to hundreds of hacked PayPal accounts; Exposing the Market for Stolen Credit Cards Data). These sources, both public and invite/vetted access only, attempt to prevent potential fraudsters — also known as rippers within the cybercrime ecosystem — from polluting a Web community’s database of fresh advertisements for newly available underground market assets. They don’t tend to pitch John Doe with tens of thousands of emails in mass advertising campaigns, at least not in the cases where they actually care about their OPSEC (Operational Security).
Although there will always be fraudulent schemes like the ones profiled in this post, over the years, experienced cybercriminals have successfully applied basic QA (Quality Assurance) practices which have resulted in an increased quality of the underground market propositions and less propositions from unverified sellers who try to defraud experienced cybercriminals.
Is the tactic of having a cybercriminal attempt to scam a potential cybercriminal a trend or a fad? It’s an every day reality that we’ll continue monitoring.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








If you can’t trust a perp, who can you trust?