Cybercriminals have resumed spamvertising the Intuit Direct Deposit Service Informer themed malicious emails, which we intercepted and profiled earlier this month. While using an identical email template, the cybercriminals behind the campaign have introduced new client-side exploits serving domains, which ultimately lead to the latest version of the Black Hole Exploit Kit.
More details:
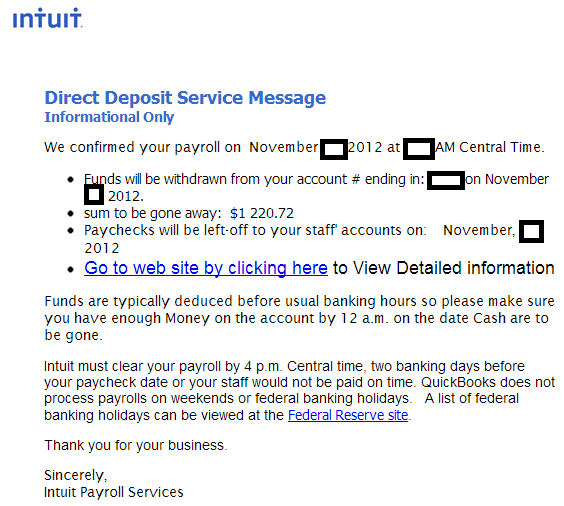
Sample screenshot of the spamvertised email:
Sample spamvertised compromised URLs: hxxp://purebodyaromatherapy.com/wp-content/plugins/akismet/intuipayr.html; hxxp://mori-system.com/wp-content/plugins/akismet/intuipayr.html; hxxp://unlimitedleverage.com/wp-content/plugins/akismet/intuipayr.html; hxxp://oktoberfestkids.com/wp-content/plugins/akismet/intuipayr.html; hxxp://myfaircredit.com/wp-content/plugins/akismet/intuipayr.html; hxxp://car-rental-24.com/wp-content/plugins/akismet/intuipayr.html; hxxp://frdmd.com/wp-content/plugins/akismet/intuipayr.html; hxxp://m-sters.com/wp-content/plugins/intuipayr.html; hxxp://purebodyaromatherapy.com/wp-content/plugins/akismet/intuipayr.html; hxxp://forletteredwords.com/wp-content/plugins/akismet/intuipayr.html; hxxp://ivanaldavert.com/wp-content/plugins/akismet/intuipayr.html; hxxp://uznay-kak.com/wp-content/plugins/akismet/intuipayr.html; hxxp://choosehomefengshui.com/wp-content/plugins/akismet/intuipayr.html; hxxp://oktoberfestkids.com/wp-content/plugins/akismet/intuipayr.html; hxxp://leahsbeautyconcepts.com/wp-content/plugins/akismet/intuipayr.html
Client-side exploits serving URL: hxxp://cosmic-calls.net/detects/mixing-evened-quits-spot.php
Malicious payload dropping URL: hxxp://cosmic-calls.net/detects/mixing-evened-quits-spot.php?xpu=2w:31:33:1o:1g&ftzajz=3a&jlzjamgn=1k:2w:32:30:1n:1h:33:31:2v:2w&xlxsjzzi=1n:1d:1f:1d:1f:1d:1j:1k:1l
Sample client-side exploits served: CVE-2010-0188
Malicious domain name reconnaissance:
cosmic-calls.net – 108.171.243.172, AS40676 – Email: samyidea@aol.com, used to respond to 75.127.15.39
108.171.243.172
Name Server: NS1.CHELSEAFUN.NET
Name Server: NS2.CHELSEAFUN.NET
We’ve already seen these name servers in related and recently launched campaigns by the same cybercriminal/gang of cybercriminals – “‘Payroll Account Holded by Intuit’ themed emails lead to Black Hole Exploit Kit“; “‘Your Discover Card Services Blockaded’ themed emails serve client-side exploits and malware“.
Upon successful client-side exploitation, the campaign drops MD5: 896bae2880071c3a63d659a157d5c16f – detected by 33 out of 44 antivirus scanners as Worm:Win32/Cridex.E.
Upon execution, the sample phones back to hxxp://203.172.238.18:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/ (AS23974, Ministry of Education, Thailand). The following domain has also responded to this IP in the past: phnomrung.com (Name server: ns1.banbu.ac.th – currently responding to 208.91.197.101).
Two MD5s are known to have phoned back to the same IP (203.172.238.18: )
MD5: 11AA0450551F89A17B4F2A66793D9408 – detected by 8 out of 44 antivirus scanners as Win32:Injector-AVZ [Trj]
MD5: f739f99f978290f5fc9a812f2a559bbb – detected by 23 out of 43 antivirus scanners as VirTool:Win32/CeeInject.EW
The main name servers used in the campaign, NS1.CHELSEAFUN.NET and NS2.CHELSEAFUN.NET, are also currently offering their services to the following malicious domains, participating in related campaigns:
performingandroidtoios.info (hxxp://performingandroidtoios.info/detects/ill_arise_pushed_addressing.php) – 199.59.166.108 – Email: cherilynn_yakibchuk192@cabacabana.com
headerandfooterprebuilt.pro (hxxp://headerandfooterprebuilt.pro/detects/quality_flyes-ticket_check.php) – 198.27.94.80 – Email: kee_mckibben0869@macfreak.com
fixedmib.net (hxxp://fixedmib.net/detects/fiscal_reduce.php) – 198.27.94.80 – Email: kessley_khouzam484@gh2000.com
We only managed to reproduce performingandroidtoios.info‘s malicious activity. Upon successful client-side exploitation, it drops MD5: fa762aba0abc5ed38a179fcaa6597033 – detected by 24 out of 44 antivirus scanners as PWS:Win32/Zbot.
Once executed, the sample creates the following files on the affected hosts:
MD5: 856A129FBAA3BBEF5B9F0FDDC6629C9D
MD5: 0B452576E3AEC9C0CBB1D68763F8AB44
MD5: 65EAFD7470C2122C519DBA22BF59B2D0
MD5: E56D76F26BD5976234B2D82984944334
The sample also initiates a DNS request to 0704271d3a758a87.com which is currently not responding. We also got additional MD5s that are known to have initiated similar DNS requests such as :
MD5: 9ed4ad1a26aa16aa4dd82ac9b785643e – detected by 27 out of 44 antivirus scanners as PWS:Win32/Zbot
MD5: 8b49e0df4e85f9a6fb6b14189a40b96b – detected by 28 out of 43 antivirus scanners as Trojan.Win32.Bublik.rmy
MD5: 76c6047e54d33e1ca5cfd8d589558d4b – detected by 4 out of 44 antivirus scanners as UDS:DangerousObject.Multi.Generic
MD5: 66561083053fb218e9e62f0a1ba545aa – detected by 28 out of 44 antivirus scanners as Trojan-Spy.Win32.Zbot.gjfd
MD5: 37e9d96104ba0c1b6ad6bdf700cf827c – detected by 27 out of 44 antivirus scanners as HEUR:Trojan.Win32.Generic
MD5: 0b22575888b4ee19452799025583b274 – detected by 29 out of 43 antivirus scanners as PWS:Win32/Zbot
MD5: 7e4de7064b069225a76654acff04e20d – detected by 18 out of 43 antivirus scanners as Trojan:Win32/Meredrop
MD5: 177b680098f710b81e6ef22bcae284b2 – detected by 34 out of 44 antivirus scanners as Trojan-Spy.Win32.Zbot.fdae
MD5: 76931198d990aee951f8e604794fe24a – detected by 27 out of 42 antivirus scanners as PWS:Win32/Zbot
MD5: c7c2e2c7613563298a6c68c0088e259f – detected by 9 out of 13 antivirus scanners as Trojan-Spy.Win32.Zbot
This isn’t the first time that cybercriminals have targeted Intuit’s customers. Go through related analysis of previously profiled malicious campaigns impersonating the company:
- ‘Payroll Account Holded by Intuit’ themed emails lead to Black Hole Exploit Kit
- ‘Intuit Payroll Confirmation inquiry’ themed emails lead to the Black Hole exploit kit
- Intuit themed ‘QuickBooks Update: Urgent’ emails lead to Black Hole exploit kit
- Cybercriminals impersonate Intuit Market, mass mail millions of exploits and malware serving emails
- Spamvertised Intuit themed emails lead to Black Hole exploit kit
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.