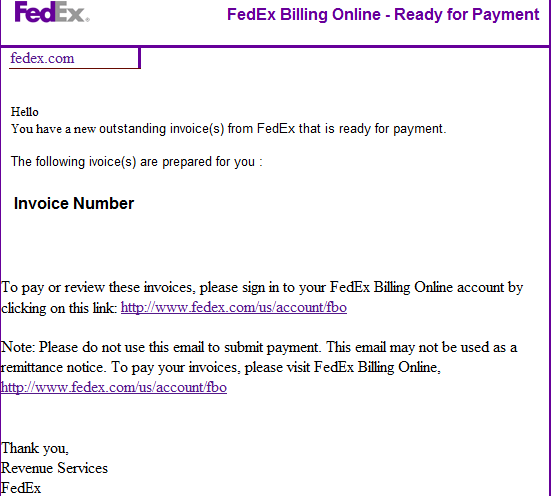
Over the past 24 hours, cybercriminals have launched yet another massive spam run, this time impersonating FedEx in an attempt to trick its customers into clicking on a malware and exploits-serving URL found in the malicious email.
More details:
Screenshot of the spamvertised email:
Screenshot of a sample Java script obfuscation:
Sample spamvertised URLs: hxxp://www.minskcityguide.net/fedinv.html; hxxp://blacklabelblogs.com/fedinv.html, hxxp://djl3.com/invdex.html; hxxp://arconcommercialfunding.com/wp-content/uploads/fgallery/fedinv.html; hxxp://greenbeltmo.org/fedinv.html; hxxp://upturnbar.com.br/wp-content/uploads/fgallery/fedinv.html
Sample client-side exploits serving URLs: hxxp://studiomonahan.net/main.php?page=2bfd5695763b6536 (200.42.159.6, AS10481; 206.253.164.43, AS6921); hxxp://gsigallery.net/main.php?page=2bfd5695763b6536 (208.91.197.54, AS40034)
Sample client-side exploits served: CVE-2010-1885
Responding to the same IPs is also the following malicious domain – mi-argentina.net.
Name servers part of the campaign’s malicious infrastructure:
ns1.correctcomfort.net – 46.4.145.164, AS24940
ns1.correctcomfort.net – 67.23.237.108, AS33182
ns1.correctcomfort.net – 173.234.9.17, AS15003
ns1.correctcomfort.net – 184.154.103.253, AS32475
More malicious domains are using these name servers, such as, for instance:
centennialfield.net
dushare.net
bowerystore.net
blue-lotusgrove.net
cat-mails.net
nitor-solutions.net
correctcomfort.net
Detection rate for a sample Java script redirector: MD5: 32a74240c7e1a34a2a8ed8749758ef15 – detected by 8 by 41 antivirus scanners as JS/Iframe.FR; Trojan-Downloader.JS.Iframe.dbe; JS/Exploit-Blacole.hd
Upon successful client-side exploitation, the campaign drops MD5: f9904f305de002ad5c0ad4b4648d0ca7 – detected by 23 out of 40 antivirus scanners as Trojan.Win32.Obfuscated.aopm; Worm:Win32/Cridex.E and MD5: 0e2c968865d34c8570bb69aa6156b915 – detected by 24 out of 42 antivirus scanners as Worm.Win32.Cridex.jb
The first sample phones back to 195.111.72.46:8080/mx/5/B/in/ (AS1955) and to 87.120.41.155:8080/mx/5/B/in (AS13147), and the second sample initiates DNS queries to droppinlever.pro; lambolp700tuning.ru and it also produces TCP traffic to 146.185.220.32 on port 443, as well as to 192.5.5.241 again on port 443.
Deja vu! We’ve already seen numerous malicious campaigns phoning back one of these command and control servers, 87.120.41.155:8080/mx/5/B/in in particular. Campaigns known to have also used the same C&C server:
- Intuit themed ‘QuickBooks Update: Urgent’ emails lead to Black Hole exploit kit
- Spamvertised ‘Wire Transfer Confirmation’ themed emails lead to Black Hole exploit kit
- Spamvertised ‘Fwd: Scan from a Hewlett-Packard ScanJet’ emails lead to Black Hole exploit kit
- Spamvertised ‘Federal Tax Payment Rejected’ themed emails lead to Black Hole exploit kit
- Cybercriminals spamvertise bogus greeting cards, serve exploits and malware
- Cybercriminals impersonate Intuit Market, mass mail millions of exploits and malware serving emails
Responding to 87.120.41.155 are also the following malicious C&C servers:
cpokemnothviik.ru
insomniacporeed.ru
Related name servers part of the campaign’s infrastructure:
ns1.cpokemnothviik.ru – 171.25.190.249, AS57683
ns2.cpokemnothviik.ru – 94.63.147.95
ns3.cpokemnothviik.ru – 171.25.190.250
ns4.cpokemnothviik.ru – 94.63.147.96
ns1.insomniacporeed.ru – 62.213.64.161, AS15756
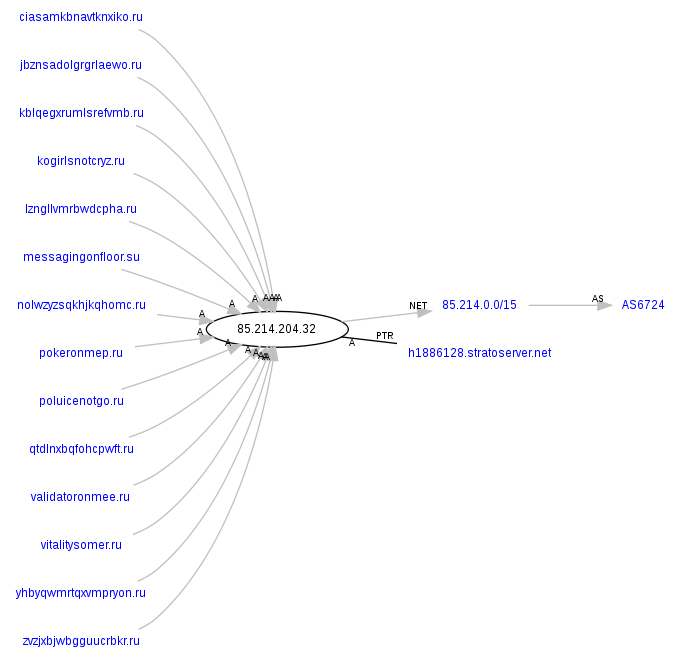
ns2.insomniacporeed.ru – 85.214.204.32, AS6724
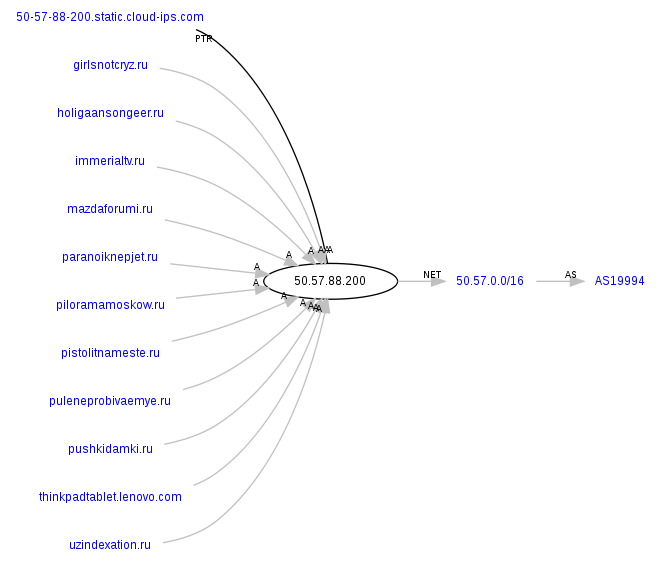
ns3.insomniacporeed.ru – 50.57.88.200, AS19994
ns4.insomniacporeed.ru – 184.106.189.124, AS19994
ns5.insomniacporeed.ru – 50.57.43.49
Responding to three of these IPS (85.214.204.32, 50.57.43.49 and 50.57.88.200 in particular) are also the following malicious domains, part of the campaign’s infrastructure:
ciasamkbnavtknxiko.ru
jbznsadolgrgrlaewo.ru
kblqegxrumlsrefvmb.ru
kogirlsnotcryz.ru
lzngllvmrbwdcpha.ru
messagingonfloor.su
nolwzyzsqkhjkqhomc.ru
pokeronmep.ru
poluicenotgo.ru
qtdlnxbqfohcpwft.ru
validatoronmee.ru
vitalitysomer.ru
yhbyqwmrtqxvmpryon.ru
zvzjxbjwbgguucrbkr.ru
girlsnotcryz.ru
holigaansongeer.ru
immerialtv.ru
mazdaforumi.ru
paranoiknepjet.ru
piloramamoskow.ru
pistolitnameste.ru
puleneprobivaemye.ru
pushkidamki.ru
uzindexation.ru
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.