In an attempt to aggregate as much traffic as possible, cybercriminals systematically abuse popular brands and online services. Next to periodically rotating the brands, they also produce professional looking email templates, in an attempt to successfully brand-jack these companies, and trick their customers into interacting with the malicious emails.
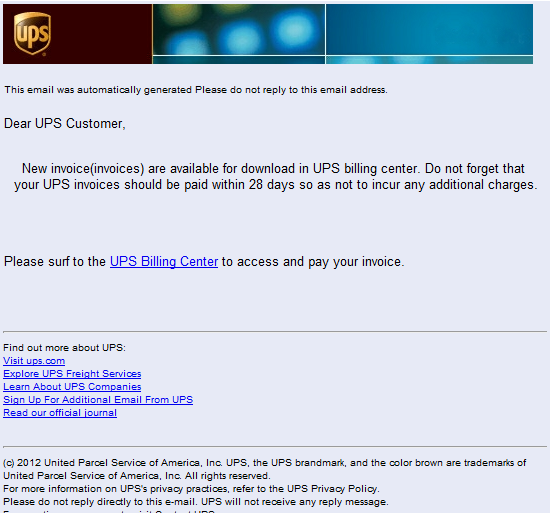
Today’s highlight is on a currently spamvertised client-side exploits and malware serving campaign impersonating UPS (United Parcel Service). Once users click on the links found in the malicious email, they’re automatically redirected to a Black Hole exploit kit landing page serving client-side exploits, and ultimately dropping malware on the exploited hosts.
More details:
Screenshot of the spamvertised email:
Upon clicking on the client-side exploits serving links, users are exposed to the following bogus “Page loading…” page:
Spamvertised URL: hxxp://218068.com/upinv.html
Client-side exploits serving URL: hxxp://proamd-inc.com/main.php?page=8cb1f95c85bce71b
Client-side exploits served: CVE-2010-1885
Upon successful client-side exploitation, the campaign drops MD5: 4462c5b3556c5cab5d90955b3faa19a8 on the exploited hosts. Detection rate: the sample is detected by 29 out of 41 antivirus scanners as Trojan.Injector.AFR; Worm.Win32.Cridex.fb.
This is the third UPS-themed malware serving campaign that we’ve intercepted over the past two months. Next to the malware serving campaigns impersonating DHL, we expect that we’re going to see more malicious activity abusing these highly popular courier service brands.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.