Everyone uses Amazon! At least that’s what the cybercriminals are hoping. Cybercriminals are currently spamvertising millions of emails impersonating Amazon.com Inc. in an attempt to trick end and corporate users into clicking on the malicious links found in the emails.
More details:
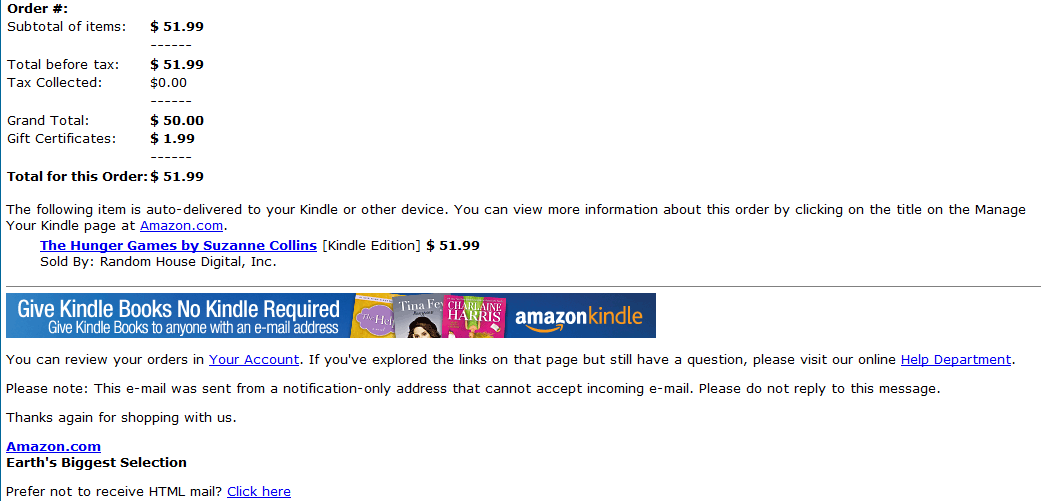
Screenshot of the spamvertised email:
Sample subjects: Your Amazon.com Kindle e-book order confirmation; Your Amazon.com order confirmation
Sample spamvertised compromised URls: hxxp://www.archos5.com/wp-content/themes/twentyten/enoz.html; hxxp://bambizilla.com/wp-includes/enoz.html; hxxp://save20discout.com/wp-content/plugins/social-stats/omaz.html
Client-side exploits serving URls: hxxp://kidwingz.net/main.php?page=614411383eef8d97; hxxp://cool-mail.net/main.php?page=640db37c90c88306
cool-mail.net responds to 84.106.114.97, responding to the same IP are also the following domains lifelovework.net; homeofficecaptioning.ru. Name servers courtesy of ns1.grapecomputers.net with the following domains also using the same name server as cool-mail.net – grapecomputers.net; kidwingz.net; itscholarshipz.net; homeofficecaptioning.ru; kidwingz.net responds to 208.91.197.54.
Both domains attempt to exploit client-side exploits served by the BlackHole web malware exploitation kit, Exploits CVE-2010-1885 in particular.
Upon successful client-side exploitation the campaingn drops MD5: c23dab8cff55155f815639d7072de21a detected by 31 out of 42 antivirus scanners as TROJ_CRYPTOR.TH; Trojan.Generic.KD.644812, and and MD5: 49f91a1597bc4dd25d3d23302125dae7 – detected by 5 out of 41 antivirus scanners as PWS-Zbot.gen.xs
Upon execution the samples create the following registry entry, next to creating a new process:
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] KB00121600.exe = “”%AppData%KB00121600.exe” so that KB00121600.exe runs every time Windows starts
Next, the samples phones back to 85.214.204.32 on port 8080, hxxp://85.214.204.32:8080/zb/v_01_b/in/ in particular.
More MD5s are known to have phone back to the same command and control C&C server in the past:
MD5: aa9b1b6037afaceee96c888c948a20fe – detected by 14 out of 42 antivirus scanners as Trojan.Generic.KDV.647512
MD5: 49f91a1597bc4dd25d3d23302125dae7 – detected by 5 out of 41 antivirus scanners as PWS-Zbot.gen.xs
MD5: 734aadd62d0662256a65510271d40048 – detected by 9 out of 42 antivirus scanners as Troj/DwnLdr-KAY
MD5: a444a9a941c1f0d28e5c3de711f04a3c – detected by 14 out of 42 antivirus scanners as Trojan.Generic.KD.647627
MD5: 3c87e446ccee826a4707d47f268d705d – detected by 25 out of 42 antivirus scanners as W32/AutoRun_Spy_Banker.P
MD5: cf6f40f1ce37fd8edefc447f68a88e1f – detected by 32 out of 42 antivirus scanners as Trojan.Win32.Yakes.aemo
MD5: 179c9ac5c2540a9bca5c0908e589a768 – detected by 28 out of 42 antivirus scanners as Troj/Bckdr-RLT
MD5: 83db494b36bd38646e54210f6fdcbc0d – detected by 33 out of 42 antivirus scanners as PWS-Zbot.gen.aae
MD5: 462210ddded90ea065829766797b42b7 – detected by 32 out of 42 antivirus scanners as Trojan-Dropper.Win32.Dapato.adpv
MD5: 712be7239b0e7e47869798658dabd4d0 – detected by 30 out of 42 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.emi
It’s worth emphasizing on the command and control (C&C) IP – 85.214.204.32. Responding to 85.214.204.32 are the following name servers:
ns3.pistolitnameste.ru
ns3.puleneprobivaemye.ru
ns2.spbfotomontag.ru
ns3.pushkidamki.ru
ns3.hamlovladivostok.ru
ns3.saprolaunimaxim.ru
ns2.uzindexation.ru
ns2.holigaansongeer.ru
ns3.paranoiknepjet.ru
ns2.piloramamoskow.ru
ns2.girlsnotcryz.ru
Historically, the following domains were also responding to the same IP, part of the botnet’s infrastructure:
cvredret.ru
cxredret.ru
opiumdlanaroda.ru
porosenokpetya.ru
garemonmystage.ru
horoshovsebudet.ru
hmvmgywkvayilcwh.ru
wfyusepaxvulfdtn.ru
wiwwkvjkinewgycb.ru
hjpyvexsutdctjol.ru
hbirjhcnsuiwgtrq.ru
axwiyyfbraskytvs.ru
skjwysujlpedxxsl.ru
sumgankorobanns.ru
ngdvmtwodjjuovsnfj.ru
vjcuiqecxaomkytb.ru
vaopxjiaphevkfpqdo.ru
yhbyqwmrtqxvmpryon.ru
qtdlnxbqfohcpwft.ru
jfhxihwykiuwfknoni.ru
kblqegxrumlsrefvmb.ru
hngajjkuknzwdliqfj.ru
hdylanfzmfngwbwxnc.ru
gizosuxwpeujnykjye.ru
jlkjsxdsvtkygouiix.ru
nolwzyzsqkhjkqhomc.ru
wbgguucrbkrkjftn.ru
usepaxvulfdtnwiwwk.ru
eoicszuwkjskhvki.ru
mceglkuyhzvzjxbj.ru
Historical OSINT on the name servers involved in the campaign, and the botnet’s infrastructure in general:
ns1.girlsnotcryz.ru => 62.213.64.161
ns2.girlsnotcryz.ru => 85.214.204.32
ns3.girlsnotcryz.ru => 50.57.88.200
ns4.girlsnotcryz.ru => 184.106.189.124
ns5.girlsnotcryz.ru => 50.57.43.49
ns1.hamlovladivostok.ru => 62.213.64.161
ns2.hamlovladivostok.ru => 62.76.189.62
ns3.hamlovladivostok.ru => 85.214.204.32
ns4.hamlovladivostok.ru => 50.57.88.200
ns5.hamlovladivostok.ru => 41.66.137.155
ns6.hamlovladivostok.ru => 50.57.43.49
ns1.puleneprobivaemye.ru => 62.213.64.161
ns2.puleneprobivaemye.ru => 62.76.189.62
ns3.puleneprobivaemye.ru => 85.214.204.32
ns4.puleneprobivaemye.ru => 50.57.88.200
ns5.puleneprobivaemye.ru => 41.66.137.155
ns6.puleneprobivaemye.ru => 50.57.43.49
ns1.pushkidamki.ru => 62.213.64.161
ns2.pushkidamki.ru => 62.76.189.62
ns3.pushkidamki.ru => 85.214.204.32
ns4.pushkidamki.ru => 50.57.88.200
ns5.pushkidamki.ru => 41.66.137.155
ns6.pushkidamki.ru => 50.57.43.49
ns1.spbfotomontag.ru => 62.213.64.161
ns2.spbfotomontag.ru => 85.214.204.32
ns3.spbfotomontag.ru => 50.57.88.200
ns4.spbfotomontag.ru => 184.106.189.124
ns5.spbfotomontag.ru => 50.57.43.49
ns1.piloramamoskow.ru => 62.213.64.161
ns2.piloramamoskow.ru => 85.214.204.32
ns3.piloramamoskow.ru => 50.57.88.200
ns4.piloramamoskow.ru => 184.106.189.124
ns5.piloramamoskow.ru => 50.57.43.49
ns1.insomniacporeed.ru => 62.213.64.161
ns2.insomniacporeed.ru => 85.214.204.32
ns3.insomniacporeed.ru => 50.57.88.200
ns4.insomniacporeed.ru => 184.106.189.124
ns5.insomniacporeed.ru => 50.57.43.49
ns1.norilsknikeli.ru => 62.213.64.161
ns2.norilsknikeli.ru => 85.214.204.32
ns3.norilsknikeli.ru => 50.57.88.200
ns4.norilsknikeli.ru => 184.106.189.124
ns5.norilsknikeli.ru => 50.57.43.49
ns1.mazdaforumi.ru => 62.213.64.161
ns2.mazdaforumi.ru => 85.214.204.32
ns3.mazdaforumi.ru => 50.57.88.200
ns4.mazdaforumi.ru => 184.106.189.124
ns5.mazdaforumi.ru => 50.57.43.49
ns1.immerialtv.ru => 62.76.41.3
ns2.immerialtv.ru => 62.213.64.161
ns3.immerialtv.ru => 195.88.242.10
ns4.immerialtv.ru => 41.66.137.155
ns5.immerialtv.ru => 83.170.91.152
ns6.immerialtv.ru => 85.214.204.32
ns1.opimmerialtv.ru => 62.213.64.161
ns2.opimmerialtv.ru => 85.214.204.32
ns3.opimmerialtv.ru => 50.57.88.200
ns4.opimmerialtv.ru => 184.106.189.124
ns5.opimmerialtv.ru => 50.57.43.49
ns1.pokeronmep.ru => 62.76.41.3
ns2.pokeronmep.ru => 62.213.64.161
ns3.pokeronmep.ru => 195.88.242.10
ns4.pokeronmep.ru => 41.66.137.155
ns5.pokeronmep.ru => 83.170.91.152
ns6.pokeronmep.ru => 85.214.204.32
ns1.poluicenotgo.ru => 62.76.41.3
ns2.poluicenotgo.ru => 62.213.64.161
ns3.poluicenotgo.ru => 195.88.242.10
ns4.poluicenotgo.ru => 41.66.137.155
ns5.poluicenotgo.ru => 83.170.91.152
ns6.poluicenotgo.ru => 85.214.204.32
ns1.uiwewsecondary.ru => 62.76.41.3
ns2.uiwewsecondary.ru => 62.213.64.161
ns3.uiwewsecondary.ru => 195.88.242.10
ns4.uiwewsecondary.ru => 41.66.137.155
ns5.uiwewsecondary.ru => 83.170.91.152
ns6.uiwewsecondary.ru => 85.214.204.32
ns1.validatoronmee.ru => 62.213.64.161
ns2.validatoronmee.ru => 195.62.52.69
ns3.validatoronmee.ru => 62.76.191.172
ns4.validatoronmee.ru => 41.66.137.155
ns5.validatoronmee.ru => 83.170.91.152
ns6.validatoronmee.ru => 85.214.204.32
ns1.vitalitysomer.ru => 62.213.64.161
ns2.vitalitysomer.ru => 195.62.52.69
ns3.vitalitysomer.ru => 62.76.191.172
ns4.vitalitysomer.ru => 41.66.137.155
ns5.vitalitysomer.ru => 83.170.91.152
ns6.vitalitysomer.ru => 85.214.204.32
ns1.wiskonsintpara.ru => 62.76.41.3
ns2.wiskonsintpara.ru => 62.213.64.161
ns3.wiskonsintpara.ru => 195.62.52.69
ns4.wiskonsintpara.ru => 41.66.137.155
ns5.wiskonsintpara.ru => 83.170.91.152
ns6.wiskonsintpara.ru => 85.214.204.32
ns1.webmastaumuren.ru => 62.76.41.3
ns2.webmastaumuren.ru => 62.213.64.161
ns3.webmastaumuren.ru => 195.62.52.69
ns4.webmastaumuren.ru => 41.66.137.155
ns5.webmastaumuren.ru => 83.170.91.152
ns6.webmastaumuren.ru => 85.214.204.32
ns1.webmastersuon.ru => 62.76.41.3
ns2.webmastersuon.ru => 62.213.64.161
ns3.webmastersuon.ru => 195.62.52.69
ns4.webmastersuon.ru => 41.66.137.155
ns5.webmastersuon.ru => 83.170.91.152
ns6.webmastersuon.ru => 85.214.204.32
ns1.qvzhpiaswhqlswkjit.ru => 62.76.45.241
ns2.qvzhpiaswhqlswkjit.ru => 62.213.64.161
ns3.qvzhpiaswhqlswkjit.ru => 85.214.204.32
ns4.qvzhpiaswhqlswkjit.ru => 216.151.129.198
ns1.xspisokdomenidgmens.ru => 62.76.45.241
ns2.xspisokdomenidgmens.ru => 62.76.191.172
ns3.xspisokdomenidgmens.ru => 62.213.64.161
ns4.xspisokdomenidgmens.ru => 85.214.204.32
ns5.xspisokdomenidgmens.ru => 209.114.47.158
ns6.xspisokdomenidgmens.ru => 78.83.233.242
Go through related analysis on previously spamvertised malware-serving campaigns:
- Spamvertised ‘DHL Package delivery report’ emails serving malware
- Spamvertised ‘UPS Delivery Notification’ emails serving client-side exploits and malware
- Spamvertised bogus online casino themed emails serving adware
- Spamvertised ‘Scan from a Hewlett-Packard ScanJet’ emails lead to client-side exploits and malware
- Spamvertised CareerBuilder themed emails serving client-side exploits and malware
- Spamvertised Verizon-themed ‘Your Bill Is Now Available’ emails lead to ZeuS crimeware
- Spamvertised ‘US Airways’ themed emails serving client-side exploits and malware
- Spamvertised LinkedIn notifications serving client-side exploits and malware
- Spamvertised ‘Pizzeria Order Details’ themed campaign serving client-side exploits and malware
- Spamvertised ‘Your tax return appeal is declined’ emails serving client-side exploits and malware
- Spamvertised ‘Your accountant license can be revoked’ emails lead to client-side exploits and malware
- Spamvertised ‘Termination of your CPA license’ campaign serving client-side exploits
Webroot SecureAnywhere users are proactively protected from this threat.
Meanwhile, users are advised to ensure that they are not running outdated versions of their third-party software and browser plugins in an attempt to mitigate the risks posed by web malware exploitation kits exploiting outdated and already patched vulnerabilities.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.