Remember the email hacking for hire service which Webroot extensively profiled in this post “Email hacking for hire going mainstream“?
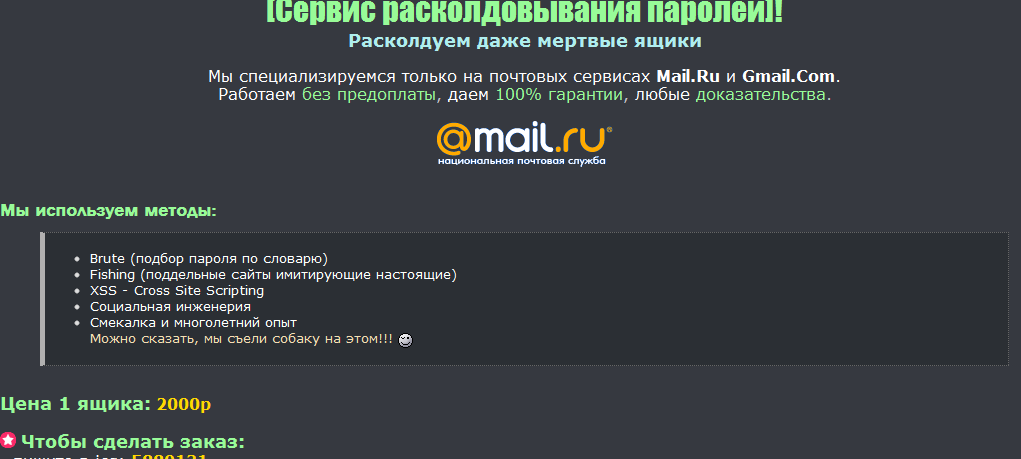
Recently, I stumbled upon another such service, advertised at cybercrime-friendly web forums, offering potential customers the opportunity to hack a particular Mail.ru and Gmail.com email address, using a variety of techniques, such as brute-forcing, phishing, XSS vulnerabilities and social engineering.
More details:
The overall availability of such services in the wild, is an indication of a growing trend, namely the combination of managed cybercrime-friendly services perfectly positioned as outsourcing vendors within the cybercrime ecosystem. Thanks to the general availability of DIY email hacking tools that brute-force an attackers way into an email address account, next to the availability of phishing templates for each and every major provider of free Web-based email, cybercriminals have all the necessary tools to accomplish their objective — hacking into an email account.
What’s particularly interesting about this particular service, is the fact that, the vendor is also offering to teach potential customers how to protect their email accounts from such hacking attempts.
More details on the service:
Important:
- Anonymity is guaranteed
- We work 20 hours a day – possible to work through the guarantor forum▬ accept wholesale orders (50 boxes), the price of individual
- As soon as your order is ready, we ourselves will contact
- BL on webmoney 88 .
How we work:
1) After receiving an order , we will first consider whether there is such a case, if he is not banned by accident, and whether it is possible to find an answer to your secret question. Write the box in the list of orders. (We always know how much time passed since the Order). . .
2) If the mailbox exists and is not banned, we put it on the brute . Speed is not mega fast, but steadily worked without a glitch. This process just takes about two days. But if the password is simple, it conjures faster.. . .
3) After checking all the available relevant databases passwords, we are sending the victim of a clever fake ~ with different chips. For his fakie, we only use the bulletproof hosting , which makes our service is 100% invulnerable!. . .
4) If the brute and the fake does not work, we try to get in touch with someone , find out all of its vulnerabilities and password to get other opportunities.. . .
5) In the case of a successful outcome (as is often the case), we tested, we can show you that access to the box really is, you rejoice and are going to pay. After we give you the password. help to go to the mailbox anonymously , to advise how to make your box does not rested …
Statistics:
- During 2011 it was the spell of more than 600 boxes
- On average, each client receives a 3.2 is what you need!
- Fakes several times productively Brutus
- Those who ordered once, often order again!90% is in the mail boxes @ py (all other orders is Google, Yandex, Rambler, ukr.net etc)
- Girls 5-6 times more likely to fall for the fake than boys.
- Often bought boxes Tipo 4463833@mail.ru, 8862200@mail.ru
- Most of the passwords: passwords and digital numbers, combined with a login / name, as well as the numeric password with the letter at the beginning or end (eg a845930), among them also there – phone numbers, dates of birth, common passwords (1234567890 etc .), occasionally caught passwords sbrutit which is very difficult, for example – Pzky266Pkv
Just how easy is it to hack someone’s email, anyway? Pretty easy, at least according to third-party research, which evaluated the strength of the passwords, and the easy to guess secret questions using a sample of active Web users.
Thankfully, in February, 2011, Gmail introduced two-factor authentication, followed by Yahoo! Mail in December 2011, making in increasingly harder to hack into someone’s email.
Webroot advises end and corporate users to be extra vigilant for potentially outsourced email hacking attempts against their personal and corporate email addresses.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.