 Last week, threat researcher and malware reverse-engineer Marco Giuliani wrote up a fairly technical description of a bootkit — a rootkit that infects the master boot record of the hard drive, making it very difficult to remove — called Popureb. Marco’s report made it clear that the bootkit does not require Windows users to format the hard drive and reinstall Windows from scratch, as Microsoft had initially claimed was required for victims of this drive-by infection.
Last week, threat researcher and malware reverse-engineer Marco Giuliani wrote up a fairly technical description of a bootkit — a rootkit that infects the master boot record of the hard drive, making it very difficult to remove — called Popureb. Marco’s report made it clear that the bootkit does not require Windows users to format the hard drive and reinstall Windows from scratch, as Microsoft had initially claimed was required for victims of this drive-by infection.
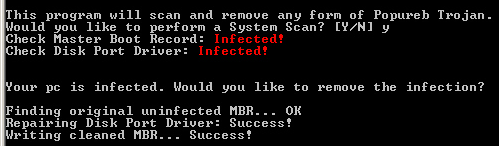
Andrea Allevi, one of our developers who works under Marco’s direction, subsequently wrote a tool that can remove the bootkit from an infected computer, which we’re releasing today to the public. We don’t offer technical support for the tool, but it’s fairly straightforward to use: Just launch it on a system infected with Popureb.E, using an account with Administrator privileges. It will ask your permission to clean the infected MBR, and once you say ‘yes’ it’ll do the rest. You’re welcome!



















you guys are the best!!!!!!!!!!!!
for me