![]() As if we didn’t have enough to deal with this week — after a Microsoft patch Tuesday that brought with it a boatload of security updates for Windows, Office, Silverlight, Visual Studio, and other programs — some enterprising malware distributor is emailing around bogus tracking number malware dressed up in the icon of a PDF document, and that malware is downloading payloads named after the updaters that Windows Update retrieves during an update.
As if we didn’t have enough to deal with this week — after a Microsoft patch Tuesday that brought with it a boatload of security updates for Windows, Office, Silverlight, Visual Studio, and other programs — some enterprising malware distributor is emailing around bogus tracking number malware dressed up in the icon of a PDF document, and that malware is downloading payloads named after the updaters that Windows Update retrieves during an update.
The malware arrived into one of our spam collection points with an attachment named UPS_document.zip. Way to be original there, criminals. Inside the Zip file was an executable downloader named UPS_Document.exe. Upon execution, it retrieves at least three payloads, including a copy of SpyEye (a password stealing Trojan), a tiny agent sending profiling information about the infected system, and a fraudulent “rogue system utility” called (on my XP testbed) Windows XP Restore.
The rogue takes on much of the appearance of a previous Rogue of the Week, named Windows Recovery. In fact, Windows XP Restore looks to be a very slightly modified duplicate of that software. If you’ve been hit with either rogue, there are some cool free tools for you to download that will repair some of the damage; Read on for details.
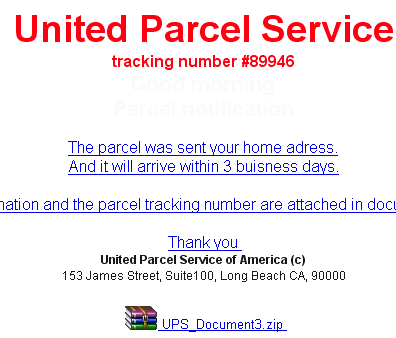
The message with the attachment looked slightly better than these sorts of spam usually do. The creators went to the trouble of generating an HTML mail message, though I don’t know why they bothered, because it’s not as if pretty formatting makes poor spelling look any better. It says:
United Parcel Service Tracking number #89946 The parcel was sent to your home adress. And it will arrive within 3 buisness days. More information and the parcel tracking number are attached in document below. Thank you United Parcel Service of America (c) 153 James Street, Suite 100, Long Beach CA, 90000
When you execute the UPS_Document program, it starts the ball rolling on a fairly serious infection.
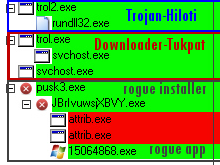
The first thing the installer does is pull down an 8704-byte downloader with the filename trol.exe, which we classify to the definition Trojan-Downloader-Tukpat. That downloader always renames itself svchost.exe initially, and copies itself into the Windows directory, but this file is not the same as the legitimate (much larger) svchost.exe that Windows uses to launch services.
After I rebooted the system, I noticed that the same downloader had made yet another copy of itself named KB171818.exe, which, when it’s listed alongside all the other running apps on the system, looks a lot like one of those Windows Update applications that patches your system. The number next to “KB” is always six digits, but randomizes each time you run it on a different machine.
The Tukpat downloader then retrieves at least three other payloads from the Web site miliardov.com. One of the payloads is always an installer for another downloader we call Hiloti; The other two are installers for SpyEye and the rogue. After executing each payload, one of the files triggers a bluescreen by crashing a Windows driver. When you reboot the box, it has been owned by the malware.
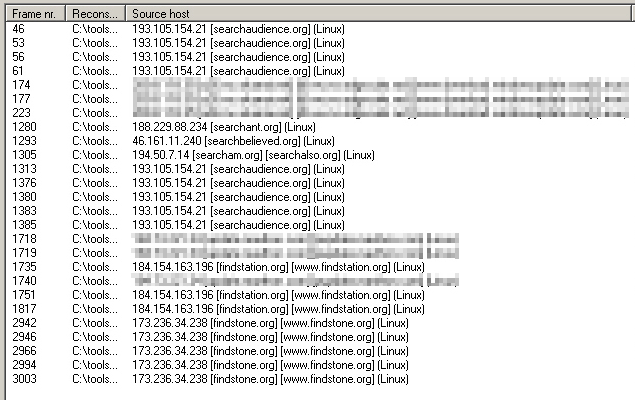
The SpyEye payload periodically (about three times an hour) sends an HTTP GET request to one of more than a dozen Web sites; The query string typically includes the IP address of the infected computer, as well as an “affiliate ID” and several other encoded parameters. The Web sites it contacts — with names like findsmell.org, findstation.org, searchbreeze.org, and clickcareful.org — redirect you to Google when you visit them directly.
The Windows XP Restore rogue immediately pulls the same stunts that Windows Recovery does, including:
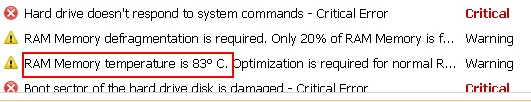
- A fake “scan” of the computer for “problems”
- hiding the desktop shortcuts and contents of the Start menu inside a subfolder of the %temp% folder (Got this problem? Use this tool to fix it)
- changing the attributes to the logged-in user’s profile folders as “super hidden”
- adding a registry key to prevent the user viewing “super hidden” files (Got this problem? Use this other tool to fix it)
- hijacks the system with a program that forces itself to be on top of all other windows on the desktop.
One wonders why they bother, until you see the price tag they stick on all this baloney. Eighty four point five dollars. Yeesh.
But at least it fixes this problem. Whew, what a relief. I guess this software really blows, after all.
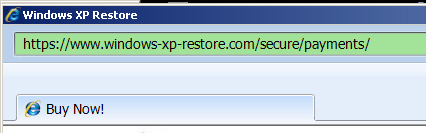
Also of note, the fake IE window in which the order form appears displays one URL:
But this is the real domain name of the payment processing service — the place where the credit card numbers go.
Does the rogue use Plimus or SecurePay, both legitimate payment processing companies, as clearinghouses for fraudulent purchases? I’m not sure, but I’m curious because the Plimus URL and SecurePay’s name appear inside the rogue application. I sent a message to Plimus earlier in the week, but they never responded.
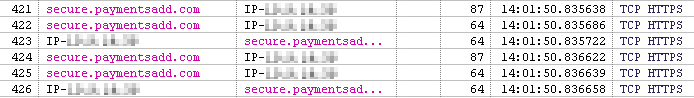
The Paymentsadd.com domain used for the transaction above was registered using a domain registrar based in China, and this is Google’s streetview of the “corporate headquarters” for this payment processor.
Yeah, I’m not buying it, either.