By Andrew Brandt and Brenden Vaughan
 Our Advanced Malware Removal group reported seeing several cases of a rogue called Antivirus Center this past week. The rogue isn’t new – we began seeing samples of it last year – but has re-emerged as a threat.
Our Advanced Malware Removal group reported seeing several cases of a rogue called Antivirus Center this past week. The rogue isn’t new – we began seeing samples of it last year – but has re-emerged as a threat.
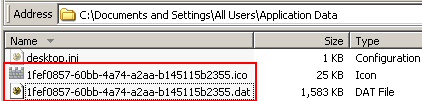
This rogue is characterized by a close mimicry of some aspects of Microsoft’s free Windows Defender product, including the use of a program icon that looks like a castle, as well as some distinctive characteristics of its active file components. For example, the rogue’s application consistently uses a naming convention that looks like a long string of random alphanumeric characters, with a .dat extension, located in the Application Data folder of the “All Users” profile. As we’ve written before, no programs should run from the Application Data folder, so anything in that location is automatically suspect.
That said, it’s still going through the same stupid rogue AV motions, with all the exaggerated detections and predictably hilarious bad grammar we’ve come to expect. Read on for more details.
The file’s name, while random, is readily identifiable because it always groups the random characters in the filename the same way. As you can see, the name of both the malware executable and its icon file use a group of eight characters, then three groups of four, then a group of 12 characters, each group separated by hyphens. This 8-4-4-4-12.dat pattern makes it very easy to spot, especially because it’s always in the “All Users” version of the Application Data folder.
Even the “purchase” process emulates the activation procedure used by Microsoft for Windows and other products. Though in the end, you’re still just led to a Web page where you’re asked to pay a whopping $80 for this sham (a $50 discount off previous frauds).
Antivirus Center also creates copies of itself in the current user’s Local SettingsTemp folder, named mv2.tmp and wrk3.tmp, as well as a copy of its icon named ins1.tmp. (The main rogue file in the screenshot below was renamed for the sake of clarity.)
If you click the Help menu within Antivirus Center, a compressed help file named hlp4.tmp.chm appears in the same Temp folder location. The “license” part of the help file tells you to head to Microsoft’s Web site and search for “Antivirus Center license terms” for more details. Needless to say, that would be a pointless exercise.
The rogue adds a run key for itself under the HKEY_CURRENT_USER hive. The rogue’s executable is actually a DLL, even though it uses a .dat extension, so the run key actually launches the legitimate Windows app rundll32.exe and passes the rogue’s filename as a parameter to rundll32.exe in order to launch the rogue.
If you find yourself infected with this rogue, start the computer in Safe Mode with Networking (the rogue won’t execute), and you should be able to perform a full sweep to remove it.
The only other registry entry it creates is a firewall exception for rundll32.exe, which allows the rogue to connect to its “buy the license key” Web site.
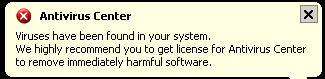
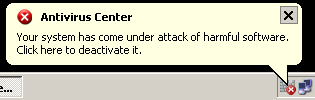
Here are some examples of the program’s active windows.
And these are some of the warning messages you’re likely to see. Keep offa my treats, rogue!
We highly recommend you deny the moronic criminals behind this junk their payday.


























I just got, I don’t know the term that’s appropriate, “vandalized” by this particular rogue today. Thank goodness that I have a brother who knows a bit about computers. He had me restart in safe mode and restore to a few days earlier, once done with that, delete my temp files and cookies, and then, run webroot. I had just done a scan manually this morning and got on Ratemyprofessor.com and it happened while on the site. It looked like it completely shut down WR and put itself in WR’s place. I couldn’t get to it to try to catch it.
Man.. these S.O.B’s got me! I don’t consider myself computer savy however I can always seem to troubleshoot through problems..Anyways I fell for this one and thought I share my story.. I went thru the WHOLE process of “buying this thing” luckily, I cancelled my card before they charged my account, but now I’m stuck with an error message when I try to open/uninstall it. Read the part said, “perform sweep on safe mode”, can anyone help me out and give me a step by step intructions? I know, I know **facepalm** right? Man, I dislike these Dbags and the ones that attacked PSN network as well..
@DU-du-dAH!
Sure thing.
1. Restart your computer.
2. As the computer begins booting, press the F8 key on your keyboard repeatedly until the startup menu appears.
3. Use the arrow keys on your keyboard to select ‘Safe Mode with Networking’ and hit enter.
4. Run a sweep with Webroot Antivirus to remove the rogue.
I really appreciate your having the info to help us with these evil attacks on our computer. However, why are you advising individuals to go into their Safe Mode to help eliminate viruses on their own when the computer professional I spoke to advised me this can cause a lot of damage to my computer since it is more complicated than it seems you are saying. He says we need a computer professional to do “Safe Mode With Networking” etc. It would be more helpful if you would make it clear that not every individual is qualified to do things to their computer without professional help. It sounded too easy to be true and I guess the virus attackers know this and that is why they have such horrible access to so many personal computers. If you know of any SAFE ways an individual can protect their computers from these attackers, it would be great to know. Thank you any way.
Starting your computer in Safe Mode is not dangerous to your computer in any way.