 We spotted an interesting behavior from a Trojan dropper that belongs to a family of malware named Ponmocup. The file, update.exe (MD5 89f4ea9f0240239e0d97f202d22af325) leaves behind a payload that, among other things, modifies the Hosts file on infected computers to prevent users from visiting popular Bittorrent sites, including The Pirate Bay.
We spotted an interesting behavior from a Trojan dropper that belongs to a family of malware named Ponmocup. The file, update.exe (MD5 89f4ea9f0240239e0d97f202d22af325) leaves behind a payload that, among other things, modifies the Hosts file on infected computers to prevent users from visiting popular Bittorrent sites, including The Pirate Bay.
It’s an odd behavior for several reasons. We don’t see many Trojans modify the Hosts file anymore because such modifications are so easily reversed. But more to the point: Why would a criminal care whether anyone else be able to browse The Pirate Bay, a Web site known to host torrents of pirated, copyrighted material? And why also block Mininova, which changed its content model more than a year ago and no longer hosts copyrighted files? None of these things make sense.
It seems at first blush like the act of someone who fancies himself a copyright vigilante, sophisticated enough to build a custom tool such as this, but who isn’t smart enough to know which sites to block.
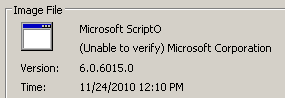
The Trojan originates from the followme.name domain, hosted in Russia. In addition to this domain, more than half the other domains hosted on the same IP address, 80.87.199.17, are known to Brightcloud as sites used for the distribution of malware, so it’s fair to say the lousy reputation is deserved. The Trojan’s properties identify it as something called Microsoft ScriptO version 6.0.6015.0, and in fact there really is a Windows component of that name and version number, used in Windows XP service pack 2, but the real component is a digitally signed DLL named scripto.dll about 57 kb in size; The Trojan is an unsigned 326 kb executable.
Once executed, it pauses, then drops and executes a payload executable with a name that changes each time the installer is run (MD5 aa14f39ee9c1907ab604f8e2a702f81b). The installer sets the permissions for the payload so that only the payload itself can do anything to itself, but those permissions are also easily bypassed in the Security tab of the file’s properties sheet.
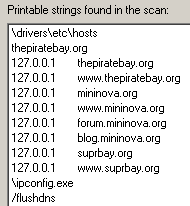
The payload isn’t particularly sophisticated, with the solitary task of blocking three Bittorrent sites its goal. It’s this payload, which we classify to Trojan-Zoeken, that modifies the Hosts file then flushes the local DNS cache. The modified Hosts file contains the following lines, which on an infected system would prevent a user from browsing to any of these domains:
127.0.0.1 thepiratebay.org 127.0.0.1 www.thepiratebay.org 127.0.0.1 mininova.org 127.0.0.1 www.mininova.org 127.0.0.1 forum.mininova.org 127.0.0.1 blog.mininova.org 127.0.0.1 suprbay.org 127.0.0.1 www.suprbay.org
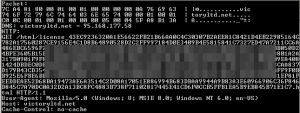
When this task is complete, it also contacts the victoryltd.net domain and sends a long query string to the server.
However, unlike most samples of Trojan-Zoeken we’ve seen, the file doesn’t download a mess of other payloads. On my test system it simply pegged the CPU and sat resident in memory, slowing the computer down and becoming a nuisance until I killed it with the Task Manager.
I haven’t devoted a great deal of time analyzing the Trojan, but it’s fair to say that if you find yourself unable to contact any of these sites, check your Hosts file for recent modifications, or just check to see if they’re actually online.



















is this trojan very dangerous? What are effects on the system? How to avoid it?
Trojan-Zoeken is a fairly serious downloader that can quickly bring down a lot of misery.
Ponmocup has only been a unique definition for a few months, and we only have a few samples. It appears to be a dropper which drops downloaders. See above.
Anti-piracy vigilantes possible. Maybe also something to do with the online advertising world?
Reducing traffic to a site essentially reduces the number of viewed advertisements that many torrent sites display (and rely on or profit from in some cases). It’s plausible that a competing torrent site could use malware in this way in hopes of forcing users to look for alternative sources (presumably their own).
Of course, the malware authors could have just coded the HOSTS file modifications to redirect users directly to those sites, but that might also call unwanted attention.