The Tacticlol downloader, responsible for a lot of infections over the past year, propagates in two ways: via drive-by downloads, and as a .zip archive attached to messages. Maybe the spam filtering companies finally caught on to the trick, or maybe the Tacticlol distributors are just trying to mix it up, but the latest sample to come over the transom has me scratching my head.
The Tacticlol downloader, responsible for a lot of infections over the past year, propagates in two ways: via drive-by downloads, and as a .zip archive attached to messages. Maybe the spam filtering companies finally caught on to the trick, or maybe the Tacticlol distributors are just trying to mix it up, but the latest sample to come over the transom has me scratching my head.
Like most others, this sample came attached to an email made to look like a message that UPS would never send. Once again, the message tries to convince the recipient that the attached file is a shipping label the recipient needs to open and print before he or she can “receive the parcel.” And, as always, the attachment contains an executable installer for the Trojan.
Dear customer Your parcel has arrived at the post office on October 9. Our Driver was unable to deliver the parcel to your address. To receive a parcel you must go to the nearest UPS office and show your mailing label. Mailing label is attached to this letter. You need to print mailing label, and show it in UPS office to receive the parcel. Thank you for your attention. UPS International Services.
But this time, instead of sending a .zip archive with a .zip extension, they sent a message with a .zip archive that has a .jpg extension. And, yeah, that just doesn’t work.
The file isn’t a JPEG image file. If you try to open it in a browser or an image editor, the editor simply errors out and tells you it isn’t an image file, and the story ends right there. I’m sure some Russian malware distributor has been double-facepalming over the waste of a perfectly good scam. Social engineering: You’re doing it wrong.
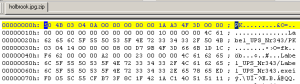
However, if you’re a curious malware researcher, you just open the file in an editor and see the PK in the file header, and realize you’re dealing with an archive. (“PK” — as in PK-Zip — is always the first two characters in a .zip archive.)
Confirming this using a tool like GT2, I could see the file name of the real payload inside the archive looks achingly familiar: Label_UPS_Nr343.exe
They’re still using “Nr,” the abbreviation (нр) for the word “number” (номер, phonetically nomer) in Russian. Come on, guys, could you at least pretend you’re trying? Make that a triple facepalm for this social engineering dropout’s demonstration of willful ignorance. Demonstration no. 1, even.
I’m not sure exactly how a non-researcher would end up infected. Most smart people would realize that, even if UPS was sending them a letter, the freight shipper would never refer to their own depot as “the post office” as this message does. And even if the user didn’t simply delete the message, and tried in vain to open an archive dressed up as an image file, the computer would only warn you about the file being the wrong type, and quit trying to open it.
Fortunately, I’m not so easily dissuaded, and I like to break stuff. In my next post, I’ll describe some of the awesomely annoying malwarey goodness that came from this one downloader.