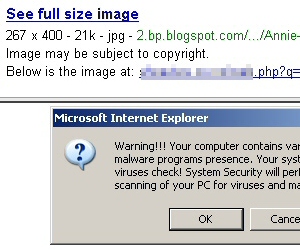
 Searchers beware: Those photos of celebrities or funny cat pictures that turn up in your Google image search results might not be photos at all, but fake antivirus alerts. Evidence appears to indicate that a similar scam to one we blogged about last November may be working its way up the Google food chain into other forms of search results.
Searchers beware: Those photos of celebrities or funny cat pictures that turn up in your Google image search results might not be photos at all, but fake antivirus alerts. Evidence appears to indicate that a similar scam to one we blogged about last November may be working its way up the Google food chain into other forms of search results.
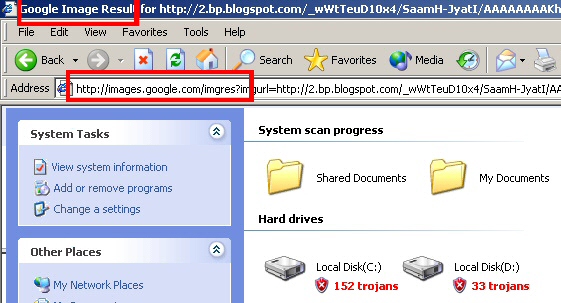
While searching for photos of Annie Wersching, an actress who recently joined the cast of the TV show 24, we stumbled into one of these javascript-enabled fakealert browser traps. Oddly enough, when you click one of these bogus linked pictures in the Image Search results frame, the original Google search frame remains at the top of the page. The fakealert runs in the lower part of the page, closing the Google search pane but retaining the Google URL in the browser’s Address Bar.
Throughout the day we’ve been looking for links such as these; Each malicious URL we found funnels the browser into the same fakealert, which itself leads to the same rogue antivirus product. Each time we revisited the site, we ended up with what was essentially the same equally nasty rogue antivirus application, sometimes in a different skin, sometimes with a different name. Early in the day we were pulling down something called Total Security. By the afternoon, the tool’s name had morphed to become Security Tool.
The rogue’s behavior on an infected system is obnoxious in the extreme. It hides the desktop by covering everything over with its own wallpaper, and blocks your ability to right-click the desktop, so it’s more difficult to revert the desktop’s appearance by changing your Display Properties settings. It also disables the scroll wheel on the mouse, then blames that behavior on a massive infection it claims has taken over your PC. It prohibits most Internet-capable applications, or even tools like the Task Manager, from running, in the guise of its “firewall” component. Of course, it’s all smoke and mirrors, an attempt to convince you to spend from $50 to $90 on completely ineffective, utterly useless former-Soviet snake oil.
The fakealert spins up in the lower pane of the Image Search page; When it runs, it immediately closes the upper pane of the results window. Unfortunately for Google, the way the fakealert runs make it appear to originate from Google’s server, even though it’s running from elsewhere.
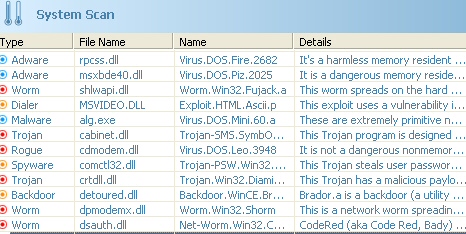
The scripted fakealert page redirects the browser to download an installer about 1MB in size. The installer, in this case, delivered something called Security Tool. Tool, indeed. It claims there were dozens of malicious files on our completely clean testbed.
The rogue also interferes with the execution of standard applications, like Internet Explorer.
And also prohibits other Internet-capable apps from making connections, using excuses that might appear plausible but are nothing but a load of malarkey.
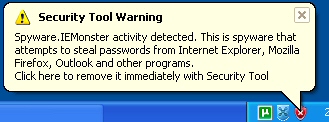
But could you really call it a rogue antivirus if it didn’t claim that Spyware.IEMonster was trying to eat you up? Don’t worry, it’s got that covered, too.
Remember our previous advice when it comes to these kinds of fakealerts. The moment you see something like this appear, hit Alt-F4 on your keyboard to immediately terminate the browser you’re using. You might have to click “Cancel” on a dialog box, but just keep telling the fakealert no, and it’ll eventually run its course, and stop asking. Killing the browser will prevent the fakealert from appearing, and keep you from inadvertently downloading something you’d later regret. You can always find your way back to the pages you need to use.





















I am possative I have this. How do I get rid of? Not computer savey
Use a good, reputable antivirus and antispyware product, and keep it up to date.
I have this on my computer…I didn’t have time to deal with it yesterday so my idiot boyfriend thought he was doing me a favor and paid $49.95 and downloaded the thing and now “miraculously” it works again. How do I get rid of this now?
I have absolutly no flipping idea what is good and what is bad. Holy Similitude-so i have come to the conclusion that “whatever happens, happens and i can’t control much and therefore, i can’t stress about it.”
Holy fatalistic outlook, Batman. You can, however, make sure your existing antivirus — whatever it is — is up to date and fully protecting your computer.
Great article Andrew – thanks. Very few articles (if any) I’ve seen detail how this thing gets on your computer – as an IT Admin, I’ve only seen the end result – and always get, ‘I just don’t know HOW it got on my computer’. I’ve seen these on nearly a dozen computers between 3 different clients – and one week had 6+ infections of this to deal with. Been trialing Webroot’s Websecurity Cloud-based product and really love it so far. Hoping it can stop a lot of these rogue antiviruses – as they’re almost (if not) as bad as the real thing since they essentially disable the computer by hooking into ANYTHING you try to run (even command prompt, task manager as you mentioned, etc.). System Restore (via XP or better) is a good way to quickly ‘remove it’ – then follow up with good spyware and antivirus scans to completely clean it. Wish things like this were going away – but it seems to be the trend for the moment among the scumware trojan writers out there. Hoping they all get infected by their own bug! 🙂
Got a fakealert by clicking on an image of Vitamin Water. I said what the heck! I ended up running Webroot full sweep while it was flashing and was able to close it eventually an put it into quarantine. I will now use alt-F4 when I run into trouble. I also us system mech. to clean up errors.