 Here’s a mind-bender for you to ponder over the holidays: What do diva musician Beyonce, the massively-multiplayer game World of Warcraft, the anime series Naruto, and Libertarian politician (and failed presidential candidate) Ron Paul have in common?
Here’s a mind-bender for you to ponder over the holidays: What do diva musician Beyonce, the massively-multiplayer game World of Warcraft, the anime series Naruto, and Libertarian politician (and failed presidential candidate) Ron Paul have in common?
I couldn’t guess what you might come up with, but we’ve found a drive-by download attack that delivers malware, using these disparate icons as a hook to convince Web surfers to click malicious links. The hack attempt was discovered by a Threat Research Analyst who also happens to be a Ron Paul fanatic (and I do mean fanatic — that’s a photo of his truck parked out back). While doing his daily search for Ron’s latest words of wisdom, he encountered a cleverly crafted campaign to manipulate search results which originated with Twitter feeds suddenly lighting up with links supposedly pointing to YouTube videos.
A large number of Twitter accounts tweeted messages like “YOUTUBE RON PAUL – BEST NEW VIDEO – WATCH NOW” or “YOUTUBE NARUTO CHAT ROOM 1 | BEST NEW VIDEO | WATCH NOW” — you get the idea — all within a short amount of time. Each of those screaming teasers was accompanied by a URL shortened using the bit.ly (and to a lesser extent, TinyURL.com) service; The bit.ly URLs pointed to a (now deleted) hidden subdirectory on the website of Stage Time magazine, an online only, stand-up-comedy industry publication (neither YouTube nor Stage Time was, knowingly, involved in the hack — they were victims as well). And the many first-time visitors to that site found their computers in a world of hurt shortly after following one or another of those links.
 The malicious pages on Stage Time hosted PHP scripts that pushed down several new malware samples; The scripts exploited security vulnerabilities in older versions of Adobe Flash and Adobe Reader, loading maliciously crafted SWF and PDF files in order to force the browser to pull down and run malicious executables which had virtually no detection across the spectrum of antivirus vendors. Some of these samples were droppers, others were downloaders; In either case, the drive-by payloads left the PC in a very bad state.
The malicious pages on Stage Time hosted PHP scripts that pushed down several new malware samples; The scripts exploited security vulnerabilities in older versions of Adobe Flash and Adobe Reader, loading maliciously crafted SWF and PDF files in order to force the browser to pull down and run malicious executables which had virtually no detection across the spectrum of antivirus vendors. Some of these samples were droppers, others were downloaders; In either case, the drive-by payloads left the PC in a very bad state.
Drive-by downloads such as these serve to illustrate a point I can’t emphasize enough: No matter how careful you might think you are, one wrong click can lead to an infection. In the case of this drive-by, the malicious website attempted to load first an Adobe Flash video, then a PDF file, which tricked the browser into downloading more malware. Now more than ever, browser plug-ins like Flash and Adobe Reader need to be kept up to date. For additional protection, you can disable Javascript in Adobe Reader; in this case, it would have stopped the initial infection in its tracks.
The Twitter component of this search engine manipulation trick acted as a “force multiplier” — not only did Twitter followers pick up on the links, but Twitter feed services like Tweetmeme also picked up on the problem and, inadvertently, linked to the malicious page.
A lot of Twitter feeds posted links like these, all within a short amount of time. It’s not clear exactly how the malware distributors accomplished this, but most of the Twitter user accounts appear to have been compromised.
Following the links left computer users in a world of hurt. Just the act of opening the malicious PDF file caused my test system to become infected with the Internet Security 2010 rogue antivirus app.
In the course of the infection, this rogue changes the desktop background to a puke-green color, planting a fake warning message in a black box at the center of the desktop.
It also drops several files to the system directory, some of which spawn popup warnings about an infection from the System Tray.
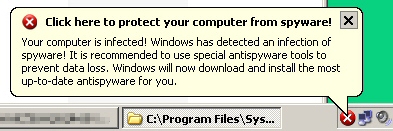
Others display a fake “scan” that, when it completes, reports that it has found 25 infections on the computer.
The fakealert also puts the kibosh on manual removal; It disables the Task Manager and screensaver, changes the desktop to a Web page named “critical_warning,” and sets registry keys that prevent changes to the Active Desktop or wallpaper (the fakealert). It also creates a user account on the infected machine, named “console,” which it uses to make other changes to the system.
The good news is that Webroot easily removes all the rogue security tools, and can block the malicious PDF file if you stumble upon a drive-by Web page and your browser attempts to load it. The bad news is that the malware distributors can make this a very unhappy holiday for you if you find yourself infected. The best thing you can do to protect yourself is follow our common sense guidelines: Keep your operating system, programs, and antivirus definitions up to date; Disable Javascript in Adobe Reader and in your browser (the NoScript add-on to Firefox makes this easy). Flash and Adobe Reader are especially prone to abuse by malicious sites, but any networked application or browser plugin could potentially be a target.

























You had my hopes up for a minute that superstar singers had started finding “libertarian genius” attractive 🙂