Purveyors of rogue security products continue to bulk up their arsenal of stupid tricks, all of which are designed to induce either fear or frustration in victims. Increasingly, certain distributions of rogue antivirus include a payload that blocks the infected computer from receiving antivirus updates. That part isn’t new; Many Trojan installers drop a Hosts file onto the infected machine which effectively prevents the computer from reaching any Web site listed in the file. But malicious Hosts files are easy to identify and remove, because they’re always in the same location (C:Windowssystem32driversetc), and the minute you delete a malicious Hosts file, the computer can connect to the previously-blocked Website.
Purveyors of rogue security products continue to bulk up their arsenal of stupid tricks, all of which are designed to induce either fear or frustration in victims. Increasingly, certain distributions of rogue antivirus include a payload that blocks the infected computer from receiving antivirus updates. That part isn’t new; Many Trojan installers drop a Hosts file onto the infected machine which effectively prevents the computer from reaching any Web site listed in the file. But malicious Hosts files are easy to identify and remove, because they’re always in the same location (C:Windowssystem32driversetc), and the minute you delete a malicious Hosts file, the computer can connect to the previously-blocked Website.
This new dirty trick employs components of a commercial software firewall development kit, called WinpkFilter, the Windows Packet Filter Kit, from NT Kernel Resources. WinpkFilter isn’t inherently evil or even necessarily undesirable. It’s a set of tools that other developers can license to create small network filtering applications. But in this case, the malware author uses these tools to block access to the Web sites used by at least half a dozen antivirus vendors. We’re calling this malware Trojan-Netfilter; Some of the affected vendors call it either Liften or Interrupdate.
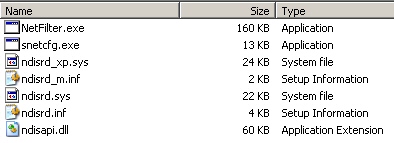
The installer of this low-key firewall, typically under 175KB, drops and installs the WinpkFilter files — ndisrd_xp.sys, ndisrd.sys, and ndisapi.dll — in the C:Windowssystem32drivers folder (for the .sys files) and C:Windowssystem32 (the DLL). All three files are clearly identified as version 3.0.5.1 of the NT Kernel Resources software. It also drops snetcfg.exe, a Microsoft-authored command-line network configuration tool that’s distributed in the Windows Server 2003 resource kit, and uses it to install the WinpkFilter components.
According to NT Kernel Resources’ Web site, the WinpkFilter software license ranges in price from $95 for an individual user, to nearly $3500 for a full development kit that includes source code.
The malicious component that runs the show is called, simply, Netfilter.exe. The installer drops it into the system32 folder and then creates a run key which causes it to start up with every reboot. The malicious package doesn’t work, however, until after a reboot, when the packet filtering drivers are loaded with Windows. After the reboot, anytime the Netfilter.exe application is running, it will block any attempt to connect to the affected update servers over the Internet.
WinpkFilter is an interesting package for the malware creators to use. It’s not widely known, but offers developers a lot of functionality. In this case, the driver looks for packets which contain specific domain names or the Web server folder paths used by some AV vendors, and if it sees those things in the network traffic, blocks the connection. The infected user only sees that their computer never was able to download the updates, though every other website is able to function properly.
We started seeing samples of Netfilter in the wild in early summer. It’s still getting pulled down by some Antivirus 2010 installers, but not as frequently as in the period from June through August.
Users of any of Webroot’s consumer or enterprise products can simply sweep for this spy and remove it, if it’s found. If you use another company’s antivirus product, and you see a file called Netfilter.exe running in your Task Manager, and you can’t download antivirus updates, try killing the Netfilter.exe process. If that instantly restores your ability to download updates, you can just browse to the location of that file and delete it.