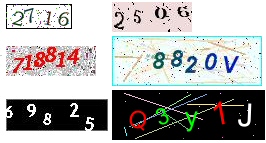
 A new Trojan quietly circulating in the wild uses components from a commercial optical character recognition (OCR) application to decode captchas, those jumbled-text images meant to help a website discern human activity from automated bots.
A new Trojan quietly circulating in the wild uses components from a commercial optical character recognition (OCR) application to decode captchas, those jumbled-text images meant to help a website discern human activity from automated bots.
The OCR-using captcha breaking tool is just one component of the Trojan. Its main purpose appears to be to fill out contest entries, online polls, and other forms relating to marketing campaigns originating in the US, and it uses the OCR-cracking software in order to read the captchas and submit the form entries, on pages where the website presents a captcha to the user.
And this is not just any captcha-cracka, but a Swiss Army Knife of sorts. The maker of the “Advanced Captcha Recognition Engine” tool, based in China, claims that the tool is capable of bypassing more than 30 different captcha systems, including those used by Yahoo, MSN, and some of the largest portal sites and banks in China.
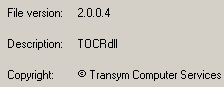 The captcha decoding tool itself is a kludge, marrying some bespoke files and components expropriated from an older version of a commercial optical character recognition (OCR) suite called TOCR. The UK-based company that makes the TOCR software, Transym Computer Services, also licenses its components to third parties, though it’s not clear they knowingly have a relationship with the Chinese captcha cracker maker, nor were they aware that parts of their engine was repurposed for sale to Chinese malfeasants. The files appear to have been stolen or pirated, and used without Transym’s knowledge.
The captcha decoding tool itself is a kludge, marrying some bespoke files and components expropriated from an older version of a commercial optical character recognition (OCR) suite called TOCR. The UK-based company that makes the TOCR software, Transym Computer Services, also licenses its components to third parties, though it’s not clear they knowingly have a relationship with the Chinese captcha cracker maker, nor were they aware that parts of their engine was repurposed for sale to Chinese malfeasants. The files appear to have been stolen or pirated, and used without Transym’s knowledge.
The Trojan is actually a nasty beast; It replaces the legitimate Windows file which handles the System Restore function with its own downloader component. This replacement ensures that the downloader runs every time the computer reboots; If the rest of the Trojan is already installed, it simply reports back a version number to its command and control site, then shuts down.
Once installed, the Trojan retrieves long, complex instructions from a central server, usually indicating the website to be tested and the form data to be entered. Quietly, at a rate of about once every 15 minutes, it connects in the background to the targeted website, attempts to fill in the form, returns the results of its OCRed form data to its command and control server, and waits for new instructions.
The Trojan also monitors any active web pages, and has functionality that steals not only passwords, but the entire contents of web-based shopping order forms. For that reason, we’ve decided to classify the Trojan as a password stealer, and not just a downloader or ad-clicker. We’re calling it Trojan-PWS-Lanci.
The websites it connects to are of the “vote for your favorite (fill in the blank) and you could win a free iPod”-esque variety that pop up on the Internet from time to time. I usually ignore these kinds of come-ons, which typically start with you providing an email address along with your “vote,” and end with your inbox filling with spam.
The benefit of all these fraudulent signups or customer survey submissions appears clear: not only do the Trojan’s creators get to test their product’s effectiveness in the real world, but it may be that, judging by the pages this weapon-of-mass-subscription visited, they stand to win one of the free $500 gift cards being offered as a promotion on most of the sites they target.
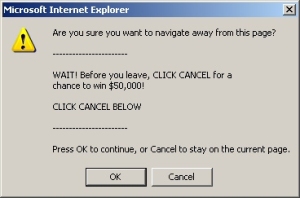
Of course, they didn’t anticipate some of the behaviors by their targeted websites. One site popped a visible warning dialog onto the desktop when the Trojan attempted to move on to another site. I suppose a completely extraneous warning like this, coming out of the blue on an idle PC, is a good indication to the victim that something funny is going on.
Little does the Trojan’s creator know that the only prize he’s likely to win is a free trip to the file quarantine.



















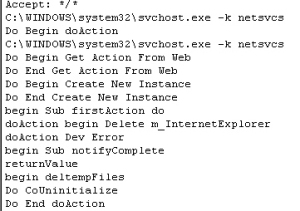


I wondered why I was getting so many of those offers.
The screenshots of those ads were taken directly from the pages the Trojan pulled down. But all of these pages were visited using a browser instance that was running in the background. With the exception of the last Internet Explorer error dialog at the bottom of the post, the user of an infected system would not see anything unusual, because the instance of Internet Explorer that was running had no visible windows. We did see them because we monitor the network traffic, and capture all the files that come over the wire.
Thanks for sharing such nice technical information with snaps. So we can easily understand it. I like your way which you listed here to learn. Thanks dude.