 After all the brouhaha surrounding the NYTimes.com website hosting ads which spawned rogue antivirus Fakealerts last weekend, I spent a considerable amount of time looking at so-called exploit kits this week. These are packages, made up of custom made Web pages (typically coded in the PHP scripting language), which perform a linchpin activity for malware distributors. Namely, they deliver the infection to the victim, using the most effective methods, based on parameters which help identify particular vulnerabilities in the victim’s browser, operating system, or applications.
After all the brouhaha surrounding the NYTimes.com website hosting ads which spawned rogue antivirus Fakealerts last weekend, I spent a considerable amount of time looking at so-called exploit kits this week. These are packages, made up of custom made Web pages (typically coded in the PHP scripting language), which perform a linchpin activity for malware distributors. Namely, they deliver the infection to the victim, using the most effective methods, based on parameters which help identify particular vulnerabilities in the victim’s browser, operating system, or applications.
There’s no indication that an exploit kit was used by the attackers in the NYTimes.com incident, but it easily could have gone that way. All an exploit kit needs in order to begin the process of foisting an infection is for a potential victim to visit its specially crafted Web page. The end result is what we call a drive-by download.
According to reports, the code injected into the Times website’s ad calls simply spawned another browser window, which in turn displayed fake alert and virus scan results messages. It wasn’t even a website hack; the site’s ad sales department were fooled into accepting a paid advertisement containing the code.
This time, that browser window was used to trick the site’s visitors into executing, and eventually buying, the rogue product. It could have been far worse.
After spending a day investigating a relatively new package, which calls itself (with a total lack of irony) the Liberty Exploit System, it’s easy to see how something like what was done on the Times website could have led news enthusiasts down a much deeper, scarier rabbit hole.
As a package, Liberty doesn’t have many parts, but it’s surprisingly effective. The malware distributors who use Liberty only have to put a few PHP scripts and a few malicious executables into a single directory on a Web server. As with other exploit kits, if one of the PHP scripts on the server detects an operating system and browser combination, or internet-capable application vulnerable to a particular kind of attack, it launches that attack. The result is, invariably, a malicious executable file running on the victim’s computer.
From a malware analysis standpoint, Liberty is interesting for a number of reasons. It’s not especially complex, and it uses specially-crafted Flash and PDF files which exploit vulnerabilities in Adobe Flash and Acrobat Reader, as well as targeting the browser itself, to download and execute a malicious payload. Under the right conditions, the entire process takes less than 15 seconds, once a browser loads the page, and is completely invisible to the user.
The Flash files that are part of the exploit display a black box wherever they’re embedded. No fancy animations or funny videos here. The PDF files contain photos of cellphones (shown below), or text taken from what appear to be from various technical textbooks about Java, or Windows.
You only see the text for a split second unless you disable JavaScript within Adobe Reader (which also neutralizes the exploit).
The use of exploits specifically targeting these two Adobe applications is significant: As Microsoft finds, and fixes, various security loopholes in the operating system and Internet Explorer, there are fewer effective targets. Third party applications like these, where automatic warnings don’t necessarily nag you every 15 minutes until you patch the application, tend to lag behind the update curve.
Liberty is also interesting because, while it may have been created by a sophisticated programmer, it’s deployed mainly by relatively unsophisticated, low level criminals who buy a license to use it, typically as a means to get their password stealing Trojan on a computer. In each case, the payload delivered by each installation of Liberty was unique to the server hosting that particular copy of the kit. We’ve seen generic phishing Trojans; downloaders, which then pull down additional payloads; and backdoor installers, which turn the infected machine into a zombie PC.
But, let’s face it, a lot of these guys running an instance of Liberty are just not the sharpest tacks in the box. As just one example, they have an uncanny tendency to leave default usernames and passwords in place. These passwords let them access an administrative panel on the malicious server.
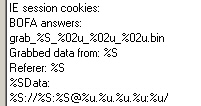
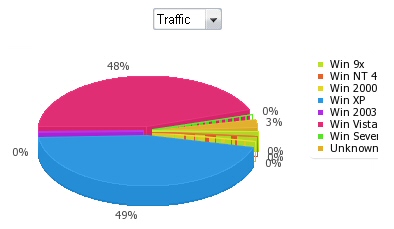
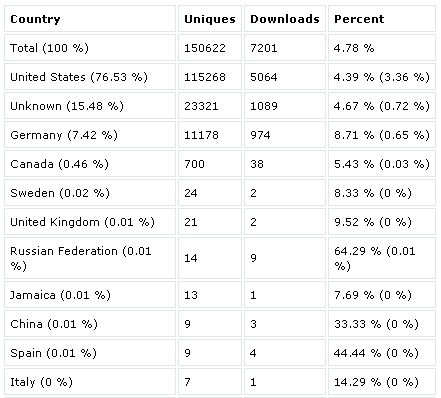
These information panels, while they don’t allow the distributor to control their network of infected systems, provide insight into the effectiveness of their distribution methods by providing helpful statistics about infected computers, broken down by geographic location, operating system version, and browser version.
Interesting stuff, indeed. Just how many machines were infected by a particular server? Take a look. They’re even helpfully organized by the country of origin of the victim.
The administrative control panel also displays a list of the referring URLs — these are the booby-trapped Web servers that redirect the browsers of unsuspecting visitors into the Liberty kit’s grasp. With a handy list of referrers at my disposal, it’s easy to set up URL blocks that prevent users of our consumer, corporate, or gateway client from being redirected into the trap.
Liberty, like so many other exploit kits, is just one component of a long string of parts which lead victims, inexorably, to infections; the cheese in the trap. Because it’s the step that directly leads to malware, it bears monitoring.
And it tells us something else: The bad guys will use all the tools at their disposal to steal — whether it’s money, passwords, or use of your computer — from you. Keeping Flash and Acrobat Reader updated denies them the use of these “gateway drug” applications to liberate your personal information.
Special thanks to our friends at MalwareDomainList for bringing this to our attention.





















My cousin says that I have a zombie program that sends him viagra info from me during the middle of the night. Is there anything that I can do?
Shut down your computer overnight, so it can’t send spam?
-=A