 The body’s barely cold from last week’s BlizzCon, but the script kiddies who write phishing kits have been hard at work putting their best foot forward, crafting account-stealing code that targets gullible WoW players who want an early peek at the just-announced Cataclysm expansion. These Catphish pages, linked off of YouTube video postings that offer promises of early, exclusive access to the expansion, lift graphics and design characteristics directly from the pages hosted by Blizzard, the publisher of the WoW franchise.
The body’s barely cold from last week’s BlizzCon, but the script kiddies who write phishing kits have been hard at work putting their best foot forward, crafting account-stealing code that targets gullible WoW players who want an early peek at the just-announced Cataclysm expansion. These Catphish pages, linked off of YouTube video postings that offer promises of early, exclusive access to the expansion, lift graphics and design characteristics directly from the pages hosted by Blizzard, the publisher of the WoW franchise.
Unfortunately for the script kiddies making and hosting the pages, they’re making some of the most boneheaded mistakes imaginable.
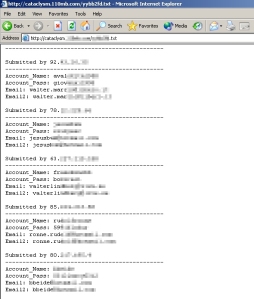
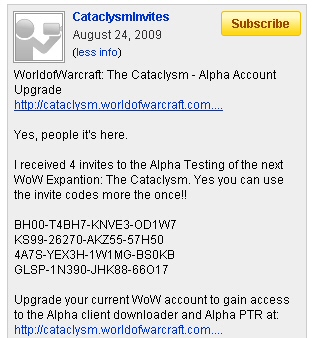
Take, for example, this page. The creator of this page was so eager to get his l33t phishing site posted on his favorite message board, he forgot to take a close look at what he was including with his phish kit. It includes not only log files containing links to the live site where he’s hosting this phishing scam, but also to a site where he’s hosting another phishing scam intended to steal a promotional code given to WoW fanatics as a bonus after they paid to watch BlizzCon streamed live to their computer.
In this case, it appears he posted the FTP update logs, which include the username he uses at his Web hosting service, as well as usernames and passwords he (presumably) entered into the phishing page to test its effectiveness. Also, word to the wise, phish-kiddie: don’t host your background images in the “New_login_phiser/New_phiser_images” directory. It’s kind of obvious.
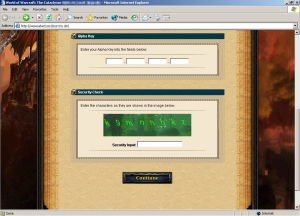
But I guess we’re not looking at the sharpest tack in the box. Not like this guy: He downloaded a very slick-looking page that is designed to steal the license key, username, and password from players. It even includes something that looks like a Captcha as a “security check” — but of course, the captcha text of “k9mnnhkz” is always the same. So is the default title text in the phish kit’s source code, which is how I found this page, just by Googling the title.
In fact, it doesn’t matter what text you enter into the captcha field — it still pushes you to the page where it asks for your account name, password, and email address. Oh, and it looks like the guy who put this page up also forgot to change the name of, or protect, the text file where the phish kit records all its stolen passwords.
Then there were the two different people who wrote applications that mimic the login screen for WoW. One, written in Visual Basic, displays a faithful reproduction of a login screen but lacking the animated background graphics. Another, written in Visual C++, uses an embedded Flash animation to reproduce the login screen’s animation. Both apps even helpfully include their source code, which was incredibly gracious of the creators. Having that source makes it far easier for us to write malware detections for this spy. Thanks, guys!
One of the phisher creators “obfuscated” his phishing page’s PHP code by churning it through a mill that first encodes the text in Base64, then scrambles all the alphabetic characters in the file with Rot13 (!), then wraps up the final package in a gzip compressed file. It’s pretty effective at turning code into gobbledygook. Here’s what it looks like:
And here’s what the same “code” looks like after about 15 seconds of computer time:
What’s ultimately depressing about all of this is that, as amateur-hour as these attempts may be, they’re still shockingly effective at capturing the account information of gullible gamers. Take a look at this screenshot, posted by a phisher creator, purportedly showing a Gmail account full of stolen credentials.
So, the bottom line appears to be the same old story: If something seems too good to be true — in this case, either a free upgrade to the Cataclysm expansion pack, or free game time codes — it probably is. If you steer clear of these and other forgeries, you’re less likely to have to endure an extended wait while the Blizzard fraud support department sorts out your stolen account details.
Special thanks to Threat Researcher and master Catphisher-hunter Curtis Fechner.