 Tomorrow morning, Blizzard Entertainment (the publisher of the wildly popular World of Warcraft franchise) will kick off another BlizzCon to show off their latest projects and directly interact with their fanbase. World of Warcraft will likely take center stage at the convention, which has become the venue of choice for Blizzard to unveil their newest expansion pack for the enormously popular online role-playing game.
Tomorrow morning, Blizzard Entertainment (the publisher of the wildly popular World of Warcraft franchise) will kick off another BlizzCon to show off their latest projects and directly interact with their fanbase. World of Warcraft will likely take center stage at the convention, which has become the venue of choice for Blizzard to unveil their newest expansion pack for the enormously popular online role-playing game.
Here at Webroot we have our fair share of past and present WoW players. So we’re quite tuned in to the malware that plagues WoW and other online games. As the gaming market continues to grow at an amazing rate, so does the real-money value of (and the virtual currency stored in) game accounts used in association with those games.
Earlier this summer we shared with our readers the top ways that threats get introduced into online games and the best ways to avoid them. With Blizzcon just hours away, and the WoW servers ramping up for the surge in imminent logons to follow, we thought we’d revisit the issue to ramp up security awareness by sharing some of the more atrocious malware variants we’ve seen hitting the WoW gaming community.
Password-stealing Trojans are what we’re really talking about here. Most WoW players that we’ve talked to have “a friend” who somehow got infected by a Trojan and subsequently had their account compromised. For some, this just means that their characters were stripped of all equipment, money, and bank items. For others who may have been in a leadership position within an established guild (a player-organized social group) the account’s thief may have stolen as many items and/or as much money as possible from the guild’s shared bank.
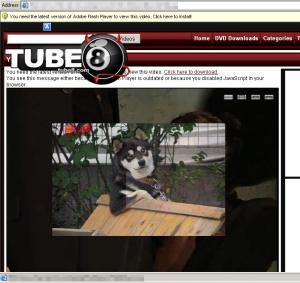
More people are likely to be interested in knowing what happens next. The image below shows the page you will arrive at when following one of these links (even as the URLs vary, the pages to which they link are effectively the same (We’ve employed Chilldog to censor the porn content).
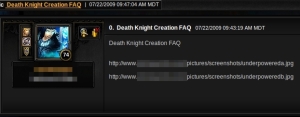
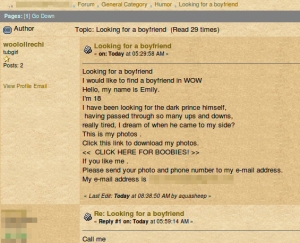
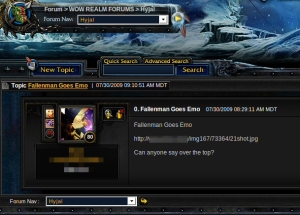
These so-called “keylogger posts” on the WoW message boards are one of the most common ways these manipulative, password hungry malware writers deliver malicious ploys to WoW players. While many WoW veterans wouldn’t be distracted by the crude tactics of these posts, there are plenty of people (and maybe even some orcs) who just can’t resist that juicy drama—or really want to learn more about their Death Knight.
As you can see (even through the “censorship”), the page emulates the appearance of a flash video-based porn site. The pages leech some of the graphics from that site, but every single link on the page links to the malware installer. This simple social engineering trick, so commonly used of late by Koobface to fool Facebook users, still manages to convince users to execute the malware installer in order to view the video.
Misled gamers who download and run the flash “installer” won’t see any obvious difference on their computers to indicate that they are infected. At this point, the Trojan is ready to start stealing login credentials. These infections are often fairly simple in their configuration, though as with all malware there are versions out there which are much more complex. The installer executable simply drops a DLL file onto the victim’s hard drive, typically to System32 or another Windows subdirectory, which performs the keystroke logging then sends that data to the phisher behind the scam. The installer also modifies the Registry so the file loads with every startup.
While there is some indication that these account credentials are often phished specifically for gaming account information, there is nothing to prevent these individuals from applying those same login credentials, or logging additional ones, to other Web sites accessed by the infected individual. When that happens, this kind of crime easily transforms from a nuisance into major identity theft.
Come back tomorrow for tips and advice that will help you avoid these kinds of scams.



















I hate these bastards. They get into your details to easily.
Sometimes you are just tempted to see “what-that-post-is-all-about”.
Happened to me once last year and I struggled like hell to get my PC cleaned up again.
It is like when someone steals your wallet. It is not the money they take, but the hassle of canceling and replacing everything.
There is no need for the Authenticator. You just have to use common sense, but it is still a numbers game. Send to a million people and you will get a 1000 fools to give you there pass :p. Just be smart 🙂