 By now, you’ve most likely heard about how an ESPN reporter was victimized, and that a surreptitiously recorded video was distributed online. You may also have read that malware distributors were taking advantage of the high level of interest in this video to rapidly disseminate malware by convincing people to click links to malicious Web sites, including a fake CNN lookalike site, to watch said tawdry video.
By now, you’ve most likely heard about how an ESPN reporter was victimized, and that a surreptitiously recorded video was distributed online. You may also have read that malware distributors were taking advantage of the high level of interest in this video to rapidly disseminate malware by convincing people to click links to malicious Web sites, including a fake CNN lookalike site, to watch said tawdry video.
Well, that first wave of malware was almost identical to the distribution we saw when Farrah Fawcett died a few weeks ago. Web surfers were urged to click a link to download a picture of the late actress, and instead received an executable file which dropped, then downloaded, additional malware. Graham Cluley, who works for Sophos, pretty much nailed the story on his blog.
In our own research, we found the same things going on that he did: The piece of malware he describes (which we call Trojan-Downloader-Dermo) primarily engages in massive clickfraud, in which affiliates of advertising networks are paid each time someone clicks an advertisement in their browser. The software, in this case, is directed to “click” through hundreds of ads per minute. Occasionally, those “ads” exploit vulnerabilities in the browser to foist more malware onto the victim’s machine.
 But the malware distribution didn’t stop there. Seizing on the opportunity, another bunch of creep distributors of rogue antivirus products also began spreading the pain, using terms like “peephole video” to rank themselves high in search results. What we found was a rogue that not only lies about alleged infections on the victim’s computer, and features supposed endorsements from legitimate, respected technology publications — the award logos of PC World (and its UK counterpart PC Advisor), PC Magazine, and C|Net’s Computer Shopper grace its website — but spreads via a PDF file which exploits a relatively recently-disclosed vulnerability in Adobe’s Acrobat Reader software.
But the malware distribution didn’t stop there. Seizing on the opportunity, another bunch of creep distributors of rogue antivirus products also began spreading the pain, using terms like “peephole video” to rank themselves high in search results. What we found was a rogue that not only lies about alleged infections on the victim’s computer, and features supposed endorsements from legitimate, respected technology publications — the award logos of PC World (and its UK counterpart PC Advisor), PC Magazine, and C|Net’s Computer Shopper grace its website — but spreads via a PDF file which exploits a relatively recently-disclosed vulnerability in Adobe’s Acrobat Reader software.
The infection begins, in this case, with a PDF file that, suddenly and without us having to click anything, began downloading onto the research machine of one of our proactive research team while he was opening pages that ranked highly in search results containing the above terms and the reporter’s name. The file’s name was just “666.pdf” but it contained only scripting code that exploits two vulnerabilities in Adobe products, one of which only became public knowledge in March. The details of the vulnerabilities — which have already been fixed in the latest updates of these products — aren’t important. What is important is that users of unpatched Acrobat or Reader programs will find themselves infected within seconds if they open this PDF.
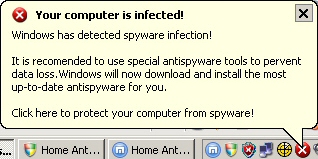
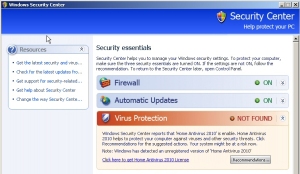
That’s because the PDF forces the computer to download and execute a malicious file. The malicious file installs what we call a Fakealert, or a program that simply displays bogus warning messages about virus infections on the computer. This one, classified to Webroot’s Softcashier Fakealerts definition, pops up warnings in the system tray, and deletes the legitimate Windows Security Center control panel, replacing it with its own version. The Fakealert, which reads as if it were written by depity Cletus, warns users “to use special antispywaretools to pervent data loss.” Ayup.
Beyond that, it also disables several key features in the affected computer, such as the Windows firewall, and reduces the overall security of the computer by changing Security Zone settings normally used by Internet Explorer to restrict the behavior of unknown scripts and ActiveX controls.
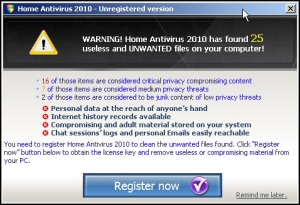
If you click any of the warnings that appear, the Fakealert downloads and installs the rogue, again, without warning or your consent. This one is called Home Antivirus 2010, but in all fundamental ways it’s no different from the rest of the rogues we see: It exists solely as a means to separate users from their hard earned money through deception and vague, poorly-spelled threats.
Fortunately, you don’t have to register the software to, as the Home Antivirus 2010 copywriter puts it, “remove useless or compromising material from your PC.” Webroot can handily remove this useless material from a compromised PC. Unfortunately for users, we can’t replace the deleted Security Center control panel. You’ll have to track down your Windows XP disc and follow the on-screen instructions that will appear from Windows File Protection to do that.
As for the reporter, we’re with Matt Hines on this — the notoriety surrounding how malware spread in response to this “event” is probably doing more to protect the victim’s privacy than a snowstorm of legal nastygrams.