 As I reported yesterday, searches for information about the deaths of Michael Jackson or Farrah Fawcett were turning up links to malware. This came as no surprise to anyone, though the speed with which the links spread was astonishing: Within minutes of the first confirmation that Jackson had succumbed to a heart attack, the first malicious blog posts began popping up in search results. We’re continuing to monitor hundreds of malicious sites touting news of Jackson’s demise — and new malicious blogs are coming up as fast as the blog services can shut them off.
As I reported yesterday, searches for information about the deaths of Michael Jackson or Farrah Fawcett were turning up links to malware. This came as no surprise to anyone, though the speed with which the links spread was astonishing: Within minutes of the first confirmation that Jackson had succumbed to a heart attack, the first malicious blog posts began popping up in search results. We’re continuing to monitor hundreds of malicious sites touting news of Jackson’s demise — and new malicious blogs are coming up as fast as the blog services can shut them off.
The first site we encountered that referenced Jackson appeared to be a personal blog post hosted on Google’s own Blogspot service. However, we quickly determined that something wasn’t right with the post. Just visiting the page spawned a tornado of background and foreground browser activity — over 100 URLs, mostly called from ad-host Yieldmanager by an automated script hosted elsewhere, were pulled down in just the first three seconds after the page loaded; The list grew to 500 URLs by the time 32 seconds had elapsed.
To illustrate the speed that the scripts embedded in the malicious blog post were loading ads, I captured this short video, which shows the amount of activity in about 60 seconds of permitting the page to load. I can only guess that the volume of URLs was limited by the fact that I had to click through some dialog boxes that appeared during the test. Another interesting thing is that between the time I began the video and the time it ended, Google had terminated the malicious blog account — for the moment, at least. The last page to load in the video is a Google ‘404’ error message when I attempted to load the initial page a second time.
[vimeo http://vimeo.com/5329574]
Some of the sites loaded by these malicious scripts also used browser exploits to damage the test system.
In the previous post, I mentioned that the malware originating from links that were advertising downloads of Fawcett’s photo brought down a number of malicious payloads. A few of the sites contacted by the script hosted on the blog site promoted by the news of Jackson’s death were also contacted when I infected the test system with the malware pulled down from the pages that promoted downloads of Fawcett’s portrait. This morning, I continued following those leads to find out what would happen.
As I mentioned, one of the payloads of the initial Fawcett-promoted file is something we call Adware-Sabotch; Sabotch seems to be connected to the current spate of rogue antivirus fakealerts. In my test this morning, Sabotch initially began by performing a similar flood of URL connections in the background. Within a few minutes, Sabotch had loaded a rogue antivirus payload — an application that calls itself System Security. And this one really takes the grand prize for botching up PCs.
Once infected with System Security, the user’s desktop becomes modified into a full-screen warning message. Then, the commonplace “scan” window appears.
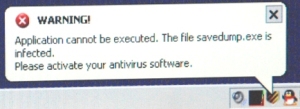
However, System Security also installs a component which interferes with the operation of almost all software on an infected PC: Once the rogue is entrenched, it simply won’t allow you to run any applications other than Internet Explorer or Windows Explorer. The program claims that any other application you attempt to load is “infected” and terminates the application before it can even start.
According to System Security, you can’t remove the product or disable its ability to block other applications unless you “activate” it (that is, fork over some dough). And this one’s a doozy. Check out the screenshot below. I have to apologize for the quality of the images below, because System Security was also blocking the software I use to take screenshots, so I had to use a camera to actually take a picture of the monitor.
So, for the low, low price of $80 (plus the pre-selected $30 “System Tuner” and $20 Lifetime Premium Support), you can have your PC back. Now, I’m not in law enforcement, but demanding that someone cough up anywhere from $50 to $130, or they don’t get to use the PC, sure sounds like straight up, bald-faced extortion to me. Isn’t extortion illegal?
One of the spies the “product” detected on my PC was none other than good old Spyware.IEmonster.D. Wait, haven’t I heard that one before?
Once I extracted all the actual system modifications from the machine, I also determined that other spies had infected the system as well. While the adware was contacting URLs, my copy of Adobe Reader fired itself up. In the post-infection analysis, I found that the adware contacted a site which then redirected to a malicious PDF file.
The file contained javascript that, when you open the PDF in a vulunerable version of Adobe Reader, pulls down still more malware.
In this case, the secondary infection was the Koobface worm.
For now, I think it’s safe to say, stick to the official news Web sites and stay away from fly-by-night, rumor mill blog posts. If you’re using any browser on Windows, I recommend Firefox and the NoScript plugin, which could save your bacon if you accidentally click through to one of these bad sites. Remember that each time the bad guys take control of your browser with a malicious script — even for a moment — you don’t wanna be startin’ something.























