 In the course of surfing around, looking for ways to get infected, I stumbled upon a site that offers visitors downloads of key generators, cracks, and other ways to circumvent the process used by most legitimate software companies to prevent people who didn’t pay for the software from registering or using it.
In the course of surfing around, looking for ways to get infected, I stumbled upon a site that offers visitors downloads of key generators, cracks, and other ways to circumvent the process used by most legitimate software companies to prevent people who didn’t pay for the software from registering or using it.
And of course, I stumbled into a morass of malware.
Well, “stumbled” isn’t entirely accurate. The site is well-known to us as a host of drive-by downloads — it’s a site that uses browser exploits to infect your computer. But I went there anyway just to see what they’re driving-by with these days. Technically, the site didn’t burn us — it came from an advertising network, which loaded a script that bounced to three separate machines before landing my test PC in the hot seat. Cold comfort if your PC happens to get slammed with this junk.
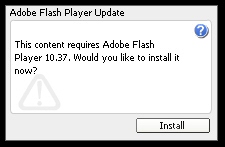
I was surprised to get infected with a copy of the Koobface worm, which spreads to users of Facebook like acne on chocoholic teenagers. Koobface hasn’t changed its M.O. since its inception, and this one was no different: I was shown a “video” for which I needed “Adobe Flash Player 10.37” — helpfully hosted on the IP address belonging to another hapless Koobface-infected PC somewhere.
The installer pulls down additional payloads (presumably from schlubs who had the misfortune to get themselves infected), sets up my infected machine as a proxy server, and loads a backdoor so other suckers can be victimized by the files hosted on my computer (in theory, anyway — my machine isn’t really reachable from the Internet).
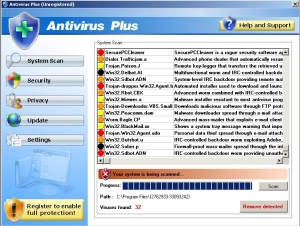
I also got a copy of a Rogue Security Product, a fake antivirus tool. Like all of them, it was a derivative of a derivative. This one is called Antivirus Plus — the “plus” being the stupid tricks it uses. Just look at the insane number of “detections” it made on a clean system.
One of the tricks is that it hijacks all searches on many different national versions of Google, redirecting them through a computer in Berlin by modifying the Hosts file.
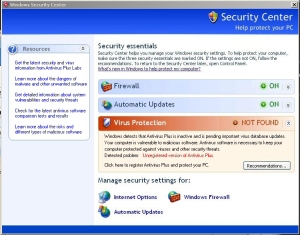
It also opens up ports in the Windows Firewall so it can communicate freely, and tosses fake warning dialog boxes all over the desktop, including the now-commonplace bogus Security Center control panel.
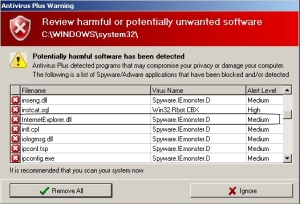
But the stupidest trick is that it watches for when you open a folder on your hard drive in Windows Explorer, and periodically throw up a dialog box “warning” you of an “infection.” What was kind of nifty was that the dialog actually pulls the filenames from the files within the folder.
The stupid part is how it claimed every file in the folder (including its own component — circled in the screenshot above) is infected — this on a totally clean test system. I’m pretty sure my entire system32 folder isn’t infected with something called Spyware.IEmonster.D.
The third and final payload was a downloader called Trojan-Downloader-Suurch. This spy profiles your computer and sets itself up as a Browser Helper Object (BHO) — an Internet Explorer plugin. In the guise of a BHO, this spy can download anything. In this case, it engages in clickfraud — actively “clicking” through online advertisements. Most clickers do this in order to either (a) deplete the target’s advertising budget, or (b) earn money for someone. But its random and uncontrolled wanderings through the Internet can also lead to additional infections if it follows the wrong link.
Oddly enough, none of these drive-by infections installed themselves. They all relied on variations of the “you need to install this missing codec” social engineering trick — and a user’s action, double-clicking the application — to get their malcode onto the target machine. Which means that, for now at least, you are potentially your own worst enemy, or your own best defense: Don’t double-click that codec!