 Once in a while, you don’t have to do anything at all and malware just drops into your lap. That happened to me the other day, when I received a buddy request from a total stranger in my decade-old ICQ instant messenger account. It’s never failed to be a rich source for malicious links, SPIM, and other fun stuff (that is, from a malware research perspective).
Once in a while, you don’t have to do anything at all and malware just drops into your lap. That happened to me the other day, when I received a buddy request from a total stranger in my decade-old ICQ instant messenger account. It’s never failed to be a rich source for malicious links, SPIM, and other fun stuff (that is, from a malware research perspective).
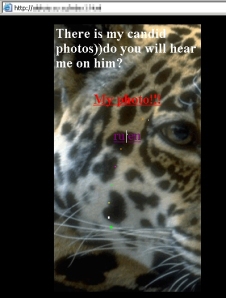
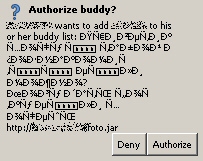
ICQ is a multi-lingual community, and this request was written in the Cyrillic alphabet. My client didn’t render it properly, so I couldn’t read the text of the come-on. But I could read the plain-ASCII URL that was linked at the bottom. So, curious, I took a look. The page looks pretty basic, with text (badly translated to English) which reads “There is my candid photos))do you will hear me on him?” and a link to download a file.
I’m a sucker for grammatically tortured social engineering, so I couldn’t resist. Yes, I thought to myself, I do will hear you on him.
The file, to my surprise, was a Java .jar file, designed to run on a Java-based mobile phone. I don’t have one handy, but I do have a pretty nifty Nokia emulator which is designed to run Java-based mobile apps, mainly games. It took the file and ran it without a hitch, but it didn’t seem to do anything, other than display a photo that was not safe for work, but pretty accurately represented what had happened to the phone.
That was when I took a look under the hood.
Unlike Windows applications, which can be compressed and manipulated in dozens of ways that make analysis difficult, Java applets — and especially ones designed for mobile phones — cannot be so easily obfuscated.
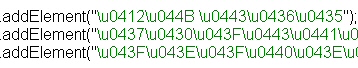
Decompiling the various .class files inside the .jar was made easier by the wide variety of free tools available for the job. Inside the .jar file was a series of five .class files, each of which perform a specific set of tasks. For example, one was used to load the photo that displays the first time the program loads.
If you try to immediately load it again, though, the program displays text, in Russian, which translates to “You have already run the program, try in an hour.”
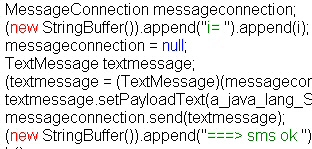
Another .class file appears to call functions in the phone’s text messaging system.
The files don’t affect PCs. I thought the most interesting thing about the entire endeavor is the fact that someone not only created a malicious .jar file but then spammed friend requests to ICQ users, assuming they would receive the link over their mobile phone, click it and infect themselves.
Two days later, I received yet another friend request, with a slightly modified version of the same thing.
If you’re running ICQ on your mobile phone, beware. Someone in Russia wants to send you more than just dirty pictures. Don’t follow links to files that appear unexpectedly in instant messages — even hilariously ungrammatical ones.